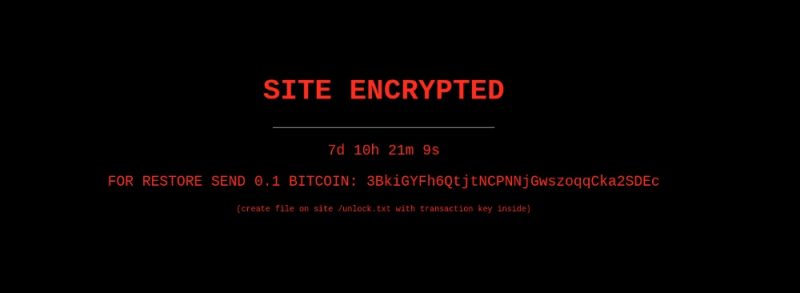
Fake red-on-black warnings have been plastered to hundreds of WordPress sites, warning that they’ve been encrypted.
The warnings have at least one ransomware accoutrement that might look convincing at first blush: a countdown clock tick-tick-ticking away, warning site owners that they’ve got seven days, 10 hours, 21 minutes and 9 seconds to fork over 0.1 Bitcoin – about USD $6,000 at the time this story was posted – before the files are encrypted and go up in an irretrievable puff of e-smoke.
That’s a good chunk of change to any small-time user of the open-source content management system (CMS): “Not a negligible sum of money for an average website owner, to say the least!” Sucuri security analyst Ben Martin wrote in a Tuesday post. It’s most particularly steep given that it’s all smoke and mirrors.
Sucuri first noticed the fake vampire-movie-colored red-on-black warnings on Friday. It started out slow, and then it started to grow: Running a Google Search last week turned up only six results for the ransom demand – “FOR RESTORE SEND 0.1 BITCOIN”. That was up to 291 hits when the website security service provider reported its findings on Tuesday.
The screechy, bleedy, full-caps message:
SITE ENCRYPTED
FOR RESTORE SEND 0.1 BITCOIN: [address redacted]
(create file on site /unlock.txt with transaction key inside)
Fortunately, before letting their precious Bitcoin fly out the window, at least one website admin reported the “ransomware” warning to Sucuri.
Tick, Tock, What a Crock
The warning was clearly intended to get targets’ adrenaline pumping, instilling a sense of urgency with that ticking countdown clock. It’s a tried-and-true tool in swindlers’ kits, whether you’re talking romance scams, phoney Amazon package-delivery notices designed to lift credentials or a gazillion other “Rush! Rush!” frauds.
But Sucuri researchers who tracked down and analyzed the fake ransomware said they found a whole lot of nothing. When running an on-site scan for a file that contained the bitcoin address, they found that the phony ransomware alert was just a simple HTML page generated by a bogus plugin, “./wp-content/plugins/directorist/directorist-base.php.”
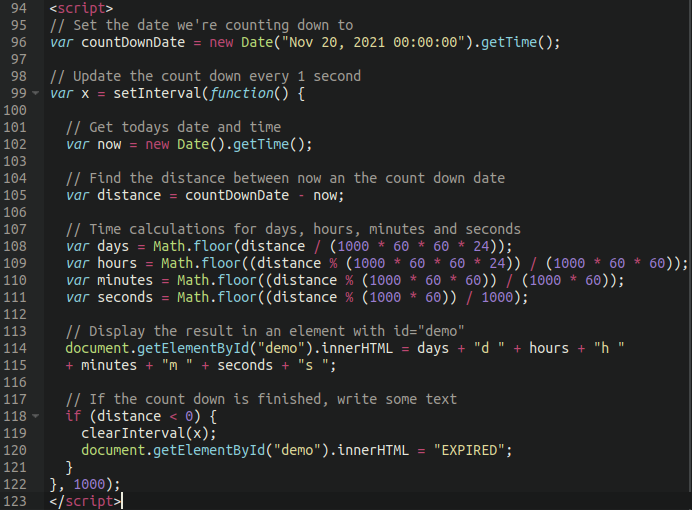
They shared a screen capture, shown below, that showed the “very basic HTML” used to generate the ransom message:
As far as the countdown timer goes, it was generated by basic PHP, as shown below. The date could be edited “to instill more panic into the request,” Martin wrote. “Remember folks, rule number one about online scams like phishing is instilling a sense of urgency to the victim!”
Scrubbing the Site Clean
Removing the infection was a snap: “All we had to do was remove the plugin from the wp-content/plugins directory,” Martin said. However, once they got the main website page back, the researchers found that all of the site’s pages and posts were leading to “404 Not Found” messages.
That was the malicious plugin’s parting shot: It included a basic SQL command that finds any posts and pages with the “publish” status and changes them to “null,” according to Sucuri’s post. The content was all still there in the database, but it couldn’t be viewed.
Again, it was a snap to undo: “This can be reversed with an equally simple SQL command,” according to Sucuri. To wit:
UPDATE `wp_posts` SET `post_status` = ‘publish’ WHERE `post_status` = ‘null’;
“This will publish any content in the database marked as null.” Martin wrote. “If you have other content marked as such, it will re-publish that, but that is certainly better than losing all your website posts and pages.”
Sucuri noted that the malicious plugin did have a file – ./wp-content/plugins/directorist/azz_encrypt.php – that looked like it might actually be used for file encryption, but researchers didn’t see that file in any of the infections they analyzed – at least, not yet.
Who’s Spooking WordPress Admins?
Sucuri’s client was located in the southern United States, but their site’s access logs showed multiple requests from a foreign IP address that was interacting with the malicious plugin using the plugin editor feature of wp-admin. “This suggests that the legitimate plugin was already installed on the website and later tampered with by the attackers,” Sucuri said.
“Interestingly, the very first request that we saw from the attacker IP address was from the wp-admin panel, suggesting that they had already established administrator access to the website before they began their shenanigans,” Martin said. “Whether they had brute forced the admin password using another IP address or had acquired the already-compromised login from the black market is anybody’s guess.”
Who Needs Ransomware When Fear Works Just Fine?
You can see the appeal: Skip the tricky task of creating real, live ransomware, and just head straight to the part where you scare the bejeezus out of people. Dan Piazza, technical product manager for Stealthbits, now part of Netwrix, told Threatpost that it’s not surprising to see fake ransomware attacks in the wake of the yearly increase in actual ransomware attacks, “especially considering how low-effort these fake attacks can be,” he said. “Less skilled attackers can take advantage of the growing fear of ransomware and try to profit with simple hacks, rather than well-developed and complex ransomware.”
Saumitra Das, CTO and cofounder of Blue Hexagon, called this one an interesting take on extorting victims – one that “may succeed for site owners who fear loss of business.”
“Ransomware actors are innovating on extorting rather than encryption given that backup technology and its adoption has improved in the last few years,” Das pointed out. “This is just another example of extortion innovation. Attackers are not just encrypting but naming and shaming the brand, exfiltrating data, threatening executives and users as well.”
Even Fake Ransomware Shows Something’s Vulnerable
Piazza told Threatpost that it doesn’t matter that this attack was fake. The fact is that these WordPress sites were indeed compromised via their most privileged attack surface – “a WordPress Admin,” he said via email.
“Should the attackers have wanted to deploy actual ransomware, then they already had the keys to the kingdom,” Piazza said.
To stay vigilant against real ransomware, Piazza advised that admins make sure that their sites are running the latest updates to the CMS, any plugins they’re using, and any libraries or frameworks they’ve implemented in their source code.
“Patched zero day exploits are still a big target for attackers, as many websites remain on older versions of their software,” he pointed out.
“Access management is also essential, to limit the number of privileged admins or even the lifecycle of those admins,” Piazza continued. “Privileged Access Management software can help here, by providing just-in-time permissions and even admin accounts that only exist when needed.”
Scheduled backups are also a must, he said. “If backups are stored completely separate from the website servers, then it’s easy to get back up and running in the event of compromise.”
He also suggested that multi-factor authentication (MFA) be used for all privileged credentials, pointing to a Microsoft report that MFA can block over 99.9 percent of account compromise attacks.
111821 17:49 UPDATE: Threatpost got a tip about a recent fix on the Directorist plugin that addressed a bug that allowed low-privilege users to run arbitrary code and to take other actions. The flaw is a possible source of the fake-ransomware-warning attacks.
This suggests that MFA wouldn’t address the possibly underlying issue and that the attackers could successfully pull off the attack again if they come across sites that are still running the older, vulnerable version of the Directorist plugin. Updating the plugin should hence be considered a priority and, as Piazza noted, the same goes for the CMS and any libraries or frameworks.
Image courtesy of Disney Parks.
Cybersecurity for multi-cloud environments is notoriously challenging. OSquery and CloudQuery is a solid answer. Join Uptycs and Threatpost for “An Intro to OSquery and CloudQuery,” an on-demand Town Hall with Eric Kaiser, Uptycs’ senior security engineer, and find out how this open-source tool can help tame security across your organization’s entire campus.
Register NOW for the on-demand event!