A honeypot set up to observe the current security landscape in smart manufacturing systems observed numerous threats—including cryptomining malware and ransomware—in just a few months, highlighting the new threats that industrial control systems (ICS) face with increased exposure to the internet.
While in the past ICS networks were traditionally proprietary and closed systems, the advent of the Internet of Things (IoT) has created manufacturing systems that have exposed devices and network ports to the internet. This also makes these systems vulnerable to more threats from bad actors – which could have dire implications when it comes to manufacturing plants or critical infrastructure.
To further study these threats, researchers with Trend Micro simulated the fake smart factory system last year in what they called “our most realistic honeypot to date,” according to their report. “We created an environment that could lure cybercriminals into carrying out attacks and at the same time give us an all but unimpeded look at their actions,” they said.
Developing the Honeypot
To make the system seem real to hackers, researchers completely mimicked an entire factory , including programmable logic controllers, a human-machine interface (HMI) and other components. They even went so far as to create a fake company with a website (see image) — a rapid prototyping consultancy firm complete with employees, working contact channels and a client base comprised of large anonymous organizations from critical industries.
, including programmable logic controllers, a human-machine interface (HMI) and other components. They even went so far as to create a fake company with a website (see image) — a rapid prototyping consultancy firm complete with employees, working contact channels and a client base comprised of large anonymous organizations from critical industries.
Researchers also made numerous intentional security mistakes in setting up the system that they said would be common at a factory with limited or inexperienced IT staff, such as leaving VNC open without a password for remote control and using a common password throughout the network.
“We practically had to do everything wrong when it came to our faux company’s general security stance,” researchers wrote. “However, for many small businesses with no IT or security staff, such a situation is not uncommon.”
The Attacks
The attacks started about two months after the honeypot went live on May 6, 2019; researchers kept the honeypot active through the end of the year. The first attack came in July when researchers observed an attacker enter the 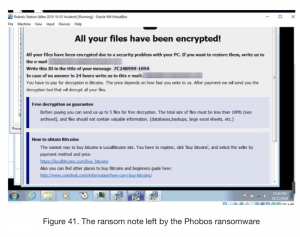 system and download a cryptocurrency miner. Over the next few months the actor returned several times to relaunch the miner.
system and download a cryptocurrency miner. Over the next few months the actor returned several times to relaunch the miner.
Ransomware was the most common type of attack researchers observed, with different attacks of this type coming in subsequent months from September to October. The September attack was a Crysis ransomware infection on Sept. 22 in which a threat actor downloaded the ransomware through TeamViewer and “continued with their routine, up to the point they left the ransom note,” researchers reported. A second ransomware attack on Oct. 21 used a Phobos variant (see image).
A unique attack in November disguised itself as a ransomware campaign, but actually was just a threat actor renaming filings so that two days later he could re-enter the system to delete files and leave open tabs of a porn site on the desktop.
Overall researchers said they observed hackers entering their system on a “regular basis” by October, but not all of these actors had nefarious intentions. One that entered the system on Nov. 1 did so just to leave a note “advising us to put a password on our VNC,” researchers said.
ICS Security
However, ICS security continues to pose a large threat, particularly with the continual disclosure of security bugs in the manufacturing, power and water plants, and the oil and gas industries – such as flaws found in 2019 in the Delta enteliBUS Manager and the Rockwell Automation industrial drive. In fact, a 2018 Kaspersky report found that a full 41.2 percent of industrial control systems were attacked by malicious software at least once in the first half of 2018.
It’s also becoming a bigger focus for the security community, and just this week Pwn2Own Miami dished out hundreds of thousands in awards for a hacking contest focusing exclusively on ICS.
When it comes to ICS security, “organizations should ensure that their equipment and the components of their ICSs are not exposed online, as we purposely did with our various ‘misconfigurations,'” researchers wrote in the report. “Although we did not see any attack taking advantage of how we used the same admin password for several workstations, organizations would do well to not imitate the same practice and to keep strict authentication policies to minimize the possibility of intrusions.”











