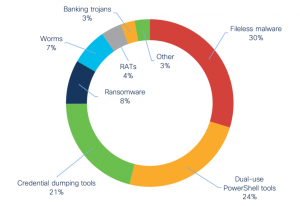
In the first half of 2020, the most common critical-severity cybersecurity threat to endpoints was fileless malware, according to a recent analysis of telemetry data from Cisco.
Fileless threats consist of malicious code that runs in memory after initial infection, instead of files being stored on the hard drive. Cisco flagged threats like Kovter, Poweliks, Divergent and LemonDuck as the most common fileless malware.
Another prevalent critical threat to endpoints in the first half was dual-use tools that are typically leveraged for both exploitation and post-exploitation tasks. Examples in circulation include PowerShell Empire, Cobalt Strike, Powersploit and Metasploit, according to Cisco.
“While these tools can very well be used for non-malicious activity, such as penetration testing, bad actors frequently utilize them,” wrote Ben Nahorney, researcher with Cisco, in a blog posting on Monday.
Credential-dumping tools make up a third critical-severity threat category. The most commonly seen of these tools that malicious actors to scrape login credentials from a compromised computer in the first half of 2020 was Mimikatz, Cisco found.

IoC threats by severity level (Click to enlarge). Source: Cisco.
The activity appears to be extending into the rest of the year. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said last week that threat actors have been spotted using the Cobalt Strike commercial penetration testing tool to target commercial and federal government networks; they have also seen the nation-states successfully deploying open-source tool Mimikatz to steal credentials.
These first three categories comprise 75 percent of the critical-severity indicators-of-compromise (IoC) seen in the analysis period; the remaining 25 percent is made up of a mix of different malwares, including ransomware (Ryuk, Maze, BitPaymer and others); worms (Ramnit and Qakbot); remote-access trojans (Corebot and Glupteba); banking trojans (Dridex, Dyre, Astaroth and Azorult); and various downloaders, wipers and rootkits.
Cisco also took a look at how threats were distributed across the MITRE ATT&CK framework of tactics.
Another way to look at the IoC data is by using the tactic categories laid out in the MITRE ATT&CK framework. Within Cisco’s Endpoint Security solution, each IoC includes information about the MITRE ATT&CK tactics employed. These tactics can provide context on the objectives of different parts of an attack, such as moving laterally through a network or exfiltrating confidential information.
“Multiple tactics can…apply to a single IoC,” the researcher explained. “For example, an IoC that covers a dual-use tool such as PowerShell Empire covers three tactics: Defense evasion (it can hide its activities from being detected); execution (it can run further modules to carry out malicious tasks); and credential access (it can load modules that steal credentials).
 By far the most common tactic, defensive evasion appears in 57 percent of IoC alerts seen. Execution also appears frequently, at 41 percent, as bad actors often launch further malicious code during multi-stage attacks.
By far the most common tactic, defensive evasion appears in 57 percent of IoC alerts seen. Execution also appears frequently, at 41 percent, as bad actors often launch further malicious code during multi-stage attacks.
“For example, an attacker that has established persistence using a dual-use tool may follow up by downloading and executing a credential dumping tool or ransomware on the compromised computer,” Nahorney said, adding that execution is more common among critical severity IoCs than defense evasion.
Two tactics commonly used to gain a foothold, initial access and persistence, come in third and fourth, showing up 11 and 12 percent of the time, respectively. Persistence appears in 38 percent of critical IoCs, as opposed to 12 percent of IoCs overall.
And, communication through command-and-control rounds out the top five tactics, appearing in 10 percent of the IoCs seen.
“While these [critical issues] make up a small portion of the overall IoC alerts, they’re arguably the most destructive, requiring immediate attention if seen,” according to Nahorney. He added, “As you might expect, the vast majority of alerts fall into the low and medium categories, [and] there’s a wide variety of IoCs within these severities.”











