Vulnerabilities in popular printer models made by HP, Dell and Lexmark expose the devices to attackers who can steal passwords, shut down printers and even steal print jobs.
Academic researchers at the University Alliance Ruhr on Monday published a series of advisories and an informational wiki regarding their findings that said nearly 20 printer models have vulnerabilities tied to common printing languages, PostScript and PJL, used in most laser printers.
“The attack can be performed by anyone who can print, for example through USB or network,” researcher Jens Müller wrote in an advisory. In other cases, an attack “can even be carried out by a malicious website, using advanced cross-site printing techniques in combination with a novel technique we call `CORS spoofing.'”
The vulnerabilities are based on a tool the researchers developed called the Printer Exploitation Toolkit (PRET). The tool connects to a printer via network or USB and exploits the weaknesses in the targeted printer’s PostScript or PJL language. “This (tool) allows stuff like capturing or manipulating print jobs, accessing the printer’s file system and memory or even causing physical damage to the device,” according to the GitHub description of PRET.
The researchers verified the vulnerabilities in printer models manufactured by HP, Lexmark, Dell, Brother, Konica and Samsung. Researchers say the PostScript and PJL flaws have existed for decades as part of known shortcomings in the aging PostScript language.
In total, researchers published six separate advisories tied to PostScript and PJL that ranging from password disclosure, print job captures and buffer overflow vulnerabilities.
One of the attack methods described by researchers allows attackers to access a printer’s file system. This type of attack takes advantage of the web mechanism called Cross-Origin Resource Sharing (CORS) that allows a third-party domain to read web page data such as fonts when performing tasks such as printing.
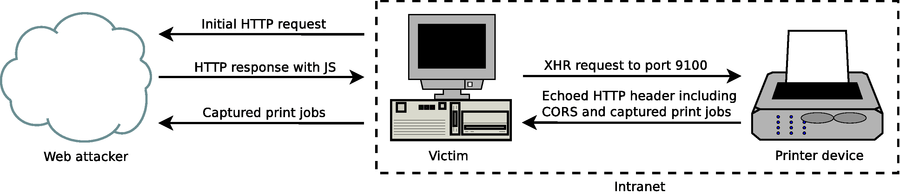
Researchers explain CORS spoofing and Cross-Site Printing (XPS) together can be used to access a printer via a web-based attack using “a hidden Iframe to send HTTP POST requests to port 9100/tcp of a printer within the victim’s internal network.”
“The HTTP header is either printed as plain text or discarded based on the printer’s settings. The POST data however can contain arbitrary print jobs like PostScript or PJL commands to be interpreted,” wrote the authors of the report. The researchers add that this type of cross-site printing attack enables a web attacker to obtain “captured print jobs, using the victim’s web browser as a carrier.”
Researchers are able to send data back to the browser from the printer by manipulating the PostScript output commands. “By using PostScript output commands we can simply emulate an HTTP server running on port 9100/tcp and define our own HTTP header to be responded – including arbitrary CORS Access-Control-Allow-Origin fields which instruct the web browser to allow JavaScript access to this resource and therefore punch a hole into the same-origin policy.”
By combining the XPS with CORS spoofing a web attacker has full access to the HTTP response which gives them the ability to extract arbitrary information such as captured print jobs from the targeted printer.
According to researchers, all printer vendors were notified of the flaw. The research will be presented in its entirety in May at the RuhrSec security conference.