An infamous business email compromise (BEC) gang has submitted hundreds of fraudulent claims with state-level U.S. unemployment websites and coronavirus relief funds. Researchers who tracked the fraudulent activity said cybercriminals may have made millions so far from the fraudulent activity.
Behind the attacks is Scattered Canary, a highly-organized Nigerian cybergang that employs dozens of threat actors to target U.S. enterprise organizations and government institutions. Since April 29, Scattered Canary has filed more than 200 fraudulent claims on the online unemployment websites of eight U.S. states; including at least 174 fraudulent claims with the state of Washington, for instance, and at least 17 fraudulent claims with the state of Massachusetts.
“In addition to the fraudulent unemployment activity against these states, we have also found evidence that links Scattered Canary to previous attacks targeting CARES Act Economic Impact Payments, which were meant to provide relief caused by the COVID-19 pandemic, as well as new scams targeting Hawaii unemployment benefits,” Patrick Peterson, founder and CEO of Agari, said in a Tuesday analysis. “We have also identified the methods Scattered Canary is using to create numerous accounts on government websites and where the stolen funds are directed.”
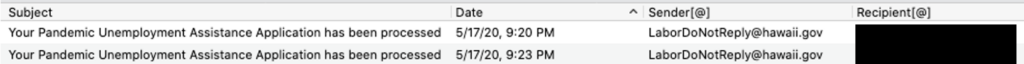
So far, the gang has targeted the unemployment websites of Florida, Massachusetts, North Carolina, Oklahoma, Rhode Island, Washington and Wyoming. And, most recently, on May 17, researchers observed Scattered Canary file its first two unemployment claims on Hawaii’s Department of Labor and Industrial Relations website.
“Based on our observations of Scattered Canary’s activity, the group seems to be setting their sights on Hawaii as their next target of fraudulent unemployment claims, which has not been previously reported,” said researchers.
The cybergang also previously targeted the COVID-19 relief fund provided by the CARES Act, which is meant to provide relief to families as a result of the coronavirus pandemic. The threat group filed at least 82 fraudulent claims for the relief fund between April 15 and April 29, using the Internal Revenue Service (IRS)-backed relief fund website to process claims from individuals who weren’t required to file tax returns. Of these filed claims, at least 30 were accepted and paid out by the IRS, they said.
“The only information needed by Scattered Canary to file these claims was an individual’s name, address, date of birth and Social Security number,” said researchers.
When asked by Threatpost where the group may have accessed this data, an Agari spokesperson said: “For the first time in over a year, we have seen a spike in W2 scams. And what’s interesting about this is that the increase in W2 scams occurred post April 15. Scattered Canary has a history and experience in W2 scams. We think that Scattered Canary is getting the personal identifiable information (PII) from the W2s.”
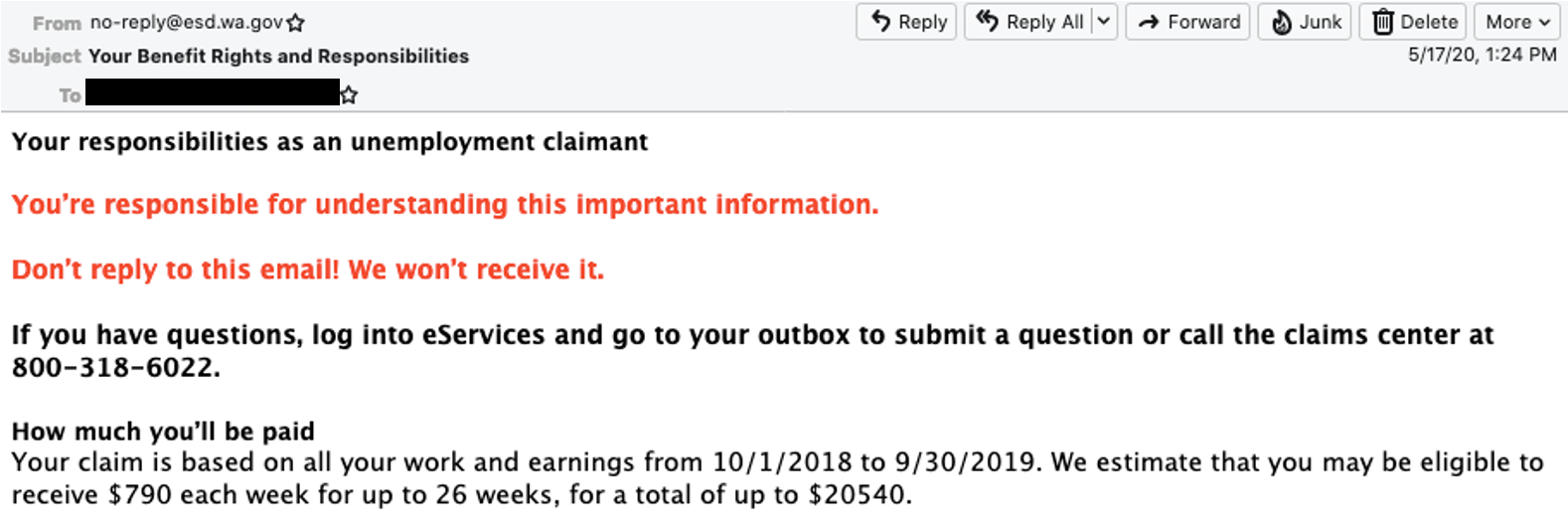
Based on communications sent to Scattered Canary, researchers said that unemployment claims were eligible to receive up to $790 a week (totaling $20,540 over a maximum of 26 weeks), while the CARES Act includes $600 in Federal Pandemic Unemployment Compensation each week through July 31. This adds up to a maximum potential loss as a result of these fraudulent claims of $4.7 million, said researchers.
Threatpost has reached out to the U.S. Treasury Department for comment.
Fraud Techniques
Researchers noted that Scattered Canary has utilized almost 50 Green Dot prepaid cards, which are prepaid debit cards, to “cash out” its fraudulent claims.
“Prepaid cards have previously been exploited to facilitate payroll-diversion BEC attacks because the cards can be used to receive direct deposit payments,” said researchers. “Green Dot cards are also advertised as being able to receive government benefits, such as unemployment payments, up to four days before they’re due to be paid, making them an attractive vehicle for groups like Scattered Canary to use in scams.”
The cybergang also used a trick that researchers call “Google dot accounts” to scale its operation. This trick abuses a legitimate Google feature – the tech company directs incoming email to the same account, regardless of where the period placement is within the email address. So, if one creates a Gmail account with an email address containing a period (e.g. attack.er01@gmail[.]com), Google strips out the period in its interpretation of the email (attacker01@gmail[.]com). That means that attack.er01@gmail[.]com and a.t.t.a.c.k.e.r.01@gmail[.]com all direct incoming email to the same account, though they may seem different.
Attackers leveraged this to create multiple versions of the same Google address for each target website – ultimately creating a fast and efficient method for carrying out the wide-scale financial crime. In fact, researchers found 259 different variations of a single email address used by Scattered Canary to create accounts on state and federal websites to carry out these fraudulent activities.
Threatpost has reached out to Google for further comment on the “Google dot accounts” tactic leveraged by the cybercriminals.
Moving forward, researchers warn that Scattered Canary will continue to take advantage of the ongoing coronavirus pandemic-relief efforts and unemployment-benefit offerings.
“As we’ve seen across the entire email threat landscape, cybercriminals have been quick to exploit the COVID-19 pandemic,” researchers said. “We have seen a more than 3,000 percent increase in COVID-19-themed phishing attacks since the beginning of February.”
Concerned about the IoT security challenges businesses face as more connected devices run our enterprises, drive our manufacturing lines, track and deliver healthcare to patients, and more? On June 3 at 2 p.m. ET, join renowned security technologist Bruce Schneier, Armis CISO Curtis Simpson and Threatpost for a FREE webinar, Taming the Unmanaged and IoT Device Tsunami. Get exclusive insights on how to manage this new and growing attack surface. Please register here for this sponsored webinar.