Researchers on Friday began warning of MacRansom, a new and free macOS-based ransomware as a service (RaaS) that’s been making the rounds over the past several weeks.
It leverages a portal hosted on the Tor network, but attackers looking for the malware won’t find it there. Interested parties need to contact the ransomware’s creators directly, via a secure ProtonMail email address, to build the ransomware. Rommel Joven and Wayne Chin Low, two researchers with Fortinet’s FortiGuard Lion Team, did just that and described what they found in a blog entry Friday.
What the researchers received back was an email from security researchers, purportedly former engineers at Yahoo and Facebook, who said they had a knack for creating Mac malware.
“We believed people were in need of such programs on macOS, so we made these tools available for free. Unlike most hackers on the darknet, we are professional developers with extensive experience in software development and vast interest in surveillance,” the email reads, “You can depend on our software as billions of users world-wide rely on our clearnet products.”
The researchers went back and forth with the creators on details such as the Bitcoin amount a target would pay, the Bitcoin address, when the ransomware could be triggered, and if it could be executed via USB.
According to Joven and Chin Yick Low, who eventually received a .zip file of the ransomware and carried out an analysis, a prompt pops up informing the user the program is from an unidentified developer. Clicking open in this instance allows the ransomware to run. As long as users don’t open it – or any files from unknown developers, they’d seemingly be safe, they write.
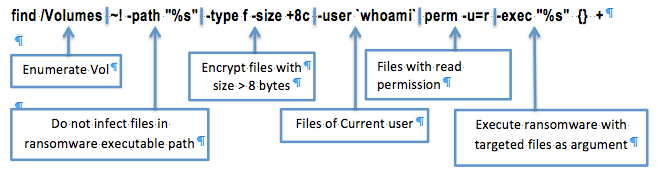
Once the malware is initiated, the researchers claim it determines whether it’s being run in a non-Mac environment or if its being debugged. If it’s not, the ransomware uses symmetric encryption with a hardcoded key to encrypt victims’ files, and stops after it has encrypted 128 files. Below is the ransomware’s file path denoted by %:
The ransomware asks the victim for a quarter (.25 BTC) Bitcoin, roughly $700, and tells them to contact another ProtonMail address, getwindows@protonmail.com, to decrypt their files but researchers say it’s unclear if that’s even possible.
Because of the algorithm the malware uses, the researchers say they’re skeptical that files infected by the ransomware can be decrypted. After reverse engineering its encryption/decryption algorithm, Joven and Chin Yick Low noticed that TargetFileKey – something that would be key to decrypting files – is permuted with a random generated number.
“In other words, the encrypted files can no longer be decrypted once the malware has terminated – the TargetFileKey will be freed from program’s memory and hence it becomes more challenging to create a decryptor or recovery tool to restore the encrypted files,” the researchers wrote, “Moreover, it doesn’t have any function to communicate with any C&C server for the TargetFileKey meaning there is no readily available copy of the key to decrypt the files.”
It may not be completely impossible, Joven and Yick Low write, adding the decryption file could likely be brute-forced but this could be a less than ideal scenario.
Noted Mac hacker and director of research at Synack Patrick Wardle, tore the covers off of MacRansom on Monday, calling it a “rather lame piece of ransomware.”
As Fortinet noted, Wardle points out that since the ransomware doesn’t use a RSA-based scheme, any hope of retrieving lost files is dashed as soon as the malware begins encrypting files.
“Once encrypted, the files are pretty much gone for good,” Wardle wrote.
Wardle acknowledges the ransomware can be generically blocked on OS X/macOS via RansomWhere? a utility Wardle released last summer however. The tool monitors OS X machines for untrusted processes that are encrypting files and was partially spurred by KeRanger, another strain of Apple malware that was signed with a legitimate Apple developer ID certificate.
Fortinet’s finding came on the same day researchers with AlienVault reported finding an OS X RAT as a service, MacSpy.
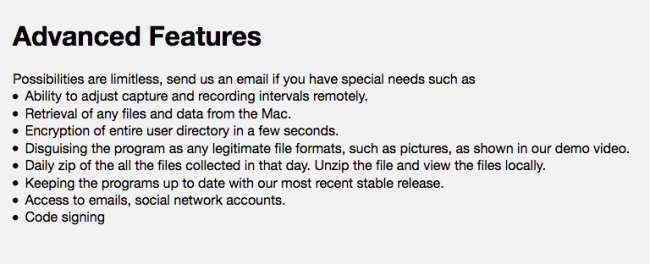
MacSpy, also obtained via an email with the malware’s author, appears to be modeled after MacRansom, at least in the sense that it’s hosted on a similar looking darkweb site and can be assembled to the specifications, see below, of an attackers’ choosing.
Like MacRansom, MacSpy has techniques that help prevent it from being debugged, or being run in a virtual machine. According to Peter Ewane, a researcher at AlienVault who penned the blog post, the malware forwards along data it collects to a command and control server, via POST requests through Tor.
“This process repeats again for the various data the malware has collected. After exfiltration of the data, the malware deletes the temporary files containing the data it sent,” Ewane wrote.
Both discoveries come as malware continues to slowly bleed over to Mac setups.
The risk around KeRanger, discovered last summer, was quickly mitigated. The malware spread in a Trojanized version of Transmission, a BitTorrent client, but was patched by the company; the certificate used to sign the ransomware meanwhile was revoked by Apple.
Earlier this year however Fortinet reported spotting macro malware that targets both Microsoft and Apple operating systems. Synack reported seeing similar malware explicitly targeting Mac versions of Microsoft Word in February.