FTCODE, a PowerShell-based ransomware that targets Italian-language users, has added new capabilities, including the ability to swipe saved web browser and email client credentials from victims.
Samples of the ransomware, which has been around since 2013, were recently observed in September 2019. After further analysis, researchers say new versions of the ransomware now aim to steal credentials from Internet Explorer and Mozilla Firefox, as well as email clients Mozilla Thunderbird, Google Chrome and Microsoft Outlook.
“The FTCODE ransomware campaign is rapidly changing,” said researchers Rajdeepsinh Dodia, Amandeep Kumar and Atinderpal Singh with Zscaler, in an analysis last week. “Due to the scripting language it was written in, it offers multiple advantages to threat actors, enabling them to easily add or remove features or make tweaks much more easily than is possible with traditionally compiled malware.”
It’s unclear how many victims have been targeted as part of FTCODE’s recent campaign; Threatpost has reached out to researchers for more details.
Attack Chain
The attack chain for FTCODE previously started with spam emails being sent to victims containing malicious macro documents, which when clicked downloaded the ransomware. However, in more recent campaigns, the bad actor has been sending victims links to VBScripts, which then download FTCODE. Once a user executes the VBScript, it in turn executes a PowerShell script, which then downloads and opens up a decoy image (saved into the %temp%folder).
This image, which purports to be an outline of prices (the image is titled “Dettaglio dei costi” in Italian, translated to “cost details”), attempts to convince users that they simply received an image. However, in the background, the ransomware is downloaded (saved in %Public%\Libraries\WindowsIndexingService.vbs) and executed.
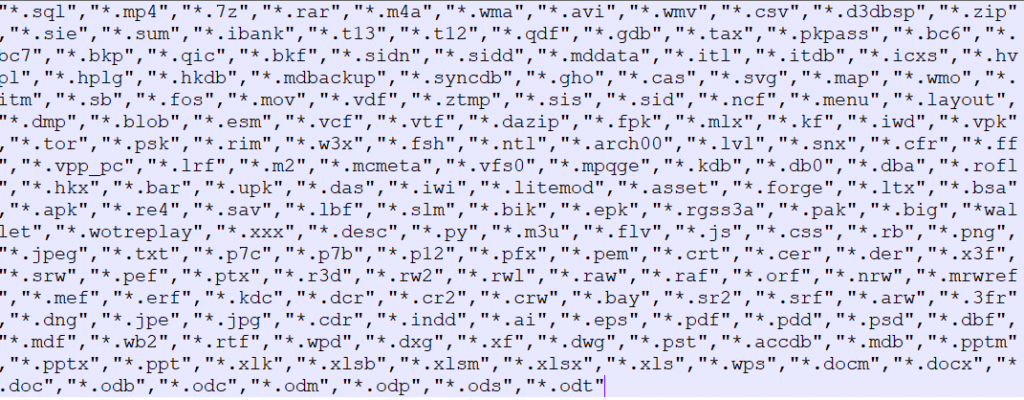
The ransomware then searches for all drives with at least 50 KB of free space and starts encrypting the files with various extensions (see picture below for a full list of the extensions).
Credential Theft
Once downloaded, FTCODE takes history details from Internet Explorer and decrypts the stored credentials from information in the registry (HKCU:\Software\Microsoft\Internet Explorer\IntelliForms\Storage2).
For Mozilla Firefox and Thunderbird, the script checks four paths and steals any credentials in them (SystemDrive\Program Files\Mozilla Firefox, SystemDrive\Program Files\Mozilla Thunderbird, SystemDrive\Program Files (x86)\Mozilla Firefox, SystemDrive\Program Files (x86)\Mozilla Thunderbird). For Google Chrome, the ransomware steals files from the file \%UserProfile%\AppData\Local\Google\Chrome\User Data\*\Login Data.
And, in Microsoft Outlook, the ransomware accesses the registry key below to steal the credentials:
- HKCU:\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\*\9375CFF0413111d3B88A00104B2A6676\*
- HKCU:\Software\Microsoft\Office\1[56].0\Outlook\Profiles\*\9375CFF0413111d3B88A00104B2A6676\*
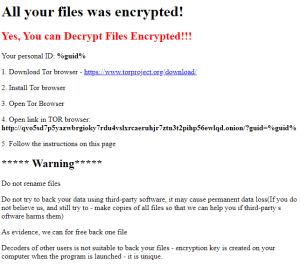 After encryption, the ransomware drops the ransom note “READ_ME_NOW.htm” in the directory that contains the encrypted files. The ransom note gives instructions to download a Tor browser and follow the instructions on the browser for next steps.
After encryption, the ransomware drops the ransom note “READ_ME_NOW.htm” in the directory that contains the encrypted files. The ransom note gives instructions to download a Tor browser and follow the instructions on the browser for next steps.
As ransomware attacks can be extremely damaging to businesses, more ransomware strains are continuously evolving to update their targeting and capabilities.
“This trend toward more creative ways to exploit… is a compelling reason to focus on stronger preventative measures and not just the ability to quickly restore files after the infection occurs,” Erich Kron, security awareness advocate at KnowBe4, said in an email.
Concerned about mobile security? Check out our free Threatpost webinar, Top 8 Best Practices for Mobile App Security, on Jan. 22 at 2 p.m. ET. Poorly secured apps can lead to malware, data breaches and legal/regulatory trouble. Join our experts from Secureworks and White Ops to discuss the secrets of building a secure mobile strategy, one app at a time. Click here to register.