The crew responsible for operating the Gameover variant of the infamous Zeus banking trojan is soliciting the enormous Cutwail botnet’s spamming capacity as an engine to fire off millions of malicious emails that seemingly originate from a number of recognizable U.S. banks.
The fraudulent emails inform their recipients that they “…have received a new encrypted message or a secure message from” whichever bank the email purports to come from. According to Dell SecureWorks’ Counter Threat Unit, the emails claim that the bank is concerned about user privacy and has devised some secure email exchange system for its customers. Attached in the email is a file that recipients are urged to download in order to register as a first time user for the email exchange.
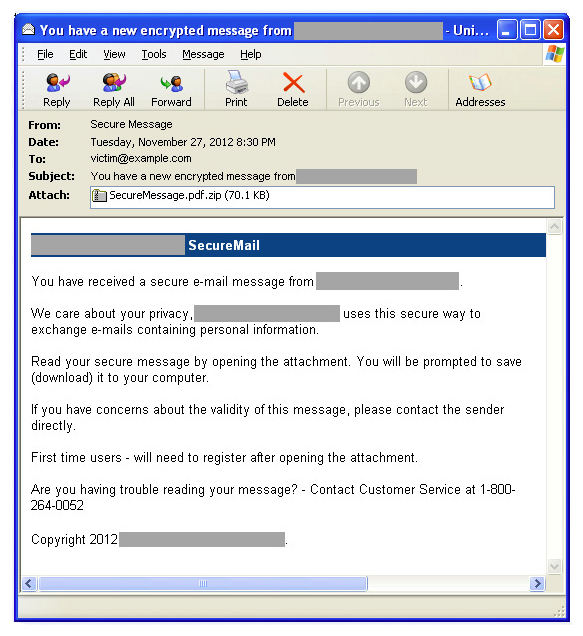
The attachment is an executable that, if clicked, loads the Pony downloader onto the machines of its victims, which, in turn, installs the Gameover Zeus variant.
Gameover is particularly troubling, according to the CTU, not only because of its peer-to-peer design, which makes taking it down nearly impossible, but also because it is privately operated, meaning, you can’t really buy variants of it on criminal hacking forums, making it harder for researchers to track down and reverse engineer.
A second flavor of the attack is attempting to trick users by claiming they are receiving a fax, scan, or voicemail that can only be accessed with a free program that can be downloaded by clicking the attachment in the email.
In an email exchange, a Dell SecureWorks spokesperson stated that as a point a policy Dell does not name victims involved in scams but said they are top U.S. banks.









