The VenusLocker group appears to be back, hatching a fresh GandCrab ransomware campaign, so to speak, using the EGG niche file type. The emails with EGG attachments are meant to specifically take aim at South Korean users.
Trend Micro researchers, who first observed the offensive campaign in early August and posted about it today, noted that the attachments are being used to deliver the GandCrab v4.3 ransomware. The firm said the rash of emails uses “e-commerce violation” lures; for instance, a common subject line reads “[Fair Trade Commission] Notice of Investigation of Violation of E-Commerce Transaction” in English.
By way of background, EGG (.egg) is a compressed archive file format that would seem exotic in most places around the globe – but in South Korea it’s the default format, much akin to ZIP files in the U.S. It was developed by a South Korean company called ESTsoft in 1999, as part of its multi-format compression utility ALZip. Even now, EGG files can only be uncompressed using the ALZip tool.
“Many South Korean users might find it odd if an archived file was sent to them by a friend or colleague in an archive file format other than .EGG,” said independent security researcher Graham Cluley.
Trend Micro researcher Donald Castillo in a post Monday cited further evidence that the operators behind the spam are specifically going after South Korean users: The use of the specifically South Korean alphabet, Hangul, in the spam mails’ subject, body and filename attachment.
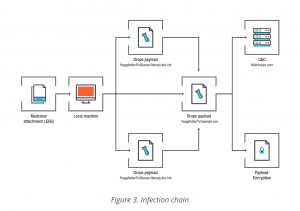
In the Trend Micro analysis of the campaign, the EGGs are most definitely rotten, filled with three files bent on malicious intent. There are two shortcut .lnk files that are disguised to appear as documents, and an executable that disappears once the user decompresses the EGG file. The hidden executable carries the GandCrab payload; it unpacks once a user clicks on either one of the two files that purport to be the documents.
“This is an example of the shift of ransomware actors moving to more targeted campaigns than the traditional ‘spray-and-pray’ technique used in the past,” said Trend Micro’s Jon Clay, director of global threat communications, told Threatpost. “Utilizing phishing email techniques that use multiple files, hidden files and a unique, and interesting subject to entice the victims into clicking on the weaponized attachments allow the threat actors behind this campaign to likely improve their infection rates.”
As for attribution, “Within the .lnk files, ‘VenusLocker_korean.exe’ is inscribed, which could mean that the VenusLocker group was behind the distribution of spam mails,” said Castillo. VenusLocker also has been spotted in the past using EGG archives, as well as the same hidden-file technique and two decoy shortcut files.
That said, Clay said that a different group could be using the file name and the VenusLocker approach as a smokescreen to throw off any investigators.
If VenusLocker is indeed the threat actor, it would mark yet another reinvention for the group. VenusLocker has a long history of targeting South Korean users via phishing campaigns, usually distributing its own proprietary ransomware. Last December, however, it was observed changing tactics, following broader trends in the threat landscape to ditch ransomware for cryptomining. In that campaign, it went after users to implant Monero mining malware.
Switching back to ransomware now also follows global trends: Data from Trend Micro shows that GandCrab was the second-highest detected ransomware family globally from March to July 2018, despite its command-and-control servers being seized by Romanian Police and Europol in March.
The criminals behind GandCrab quickly tweaked the malware after the takedown to keep ransomware payments coming in; the group has been staying profitable and staying one-step ahead of white hats by adopting a unique, highly agile malware development approach.
In any event, the attack is notable because it “reinforces the recent change we’ve seen whereby ransomware actors have shifted to more targeted, socially engineered email campaigns to improve their infection rates,” said Clay.