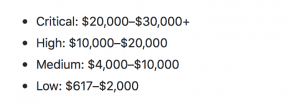GitHub has bolstered its bug-bounty program with increased rewards, an expanded scope of products and the addition of legal “safe-harbor” terms aiming to protect bounty hunters.
The web-based hosting service announced Tuesday that its program, first launched in 2014, will no longer have a maximum reward amount for critical vulnerabilities. The change comes after GitHub said it paid out a grand total of $165,000 to researchers who found vulnerabilities in its products in 2018.
“Over the past five years, we have been continuously impressed by the hard work and ingenuity of our researchers,” said GitHub’s Phil Turnbull, in a post. “We’re happy to share some of our highlights from the past year and introduce some big changes for the coming year: full legal protection for researchers, more GitHub properties eligible for rewards and increased reward amounts.”
GitHub said that it has increased rewards so that critical bugs now earn researchers between $20,000 and $30,000 – but there is no cap on these types of bugs, so the company could “reward significantly more for truly cutting-edge research.”
In comparison, the bug bounty reward for critical vulnerabilities was between $10,000 and $20,000 before, a spokesperson told Threatpost.
Critical bugs “present a direct and immediate risk to a broad array of our users or to GitHub itself;” this includes flaws like arbitrary code/command execution on a GitHub server, arbitrary SQL queries on the GitHub production database, a bypass of the GitHub login process, access to sensitive production user data or access to internal production systems.
Meanwhile “high”-severity flaws can bring in between $10,000 to $20,000 in bounties (the “high”-severity flaw bounty was between $5,000 and $10,000 before).
. Below is a full breakdown of the flaws’ payouts:
Meanwhile, the scope of products that can earn bounties have increased as well: “We’re excited to share that we are now increasing our bounty scope to reward vulnerabilities in all first-party services hosted under our github.com domain,” said GitHub.
As before, products like GitHub.com, the GitHub API and GitHub CSP are in scope; but now, more products, like GitHub Education (GitHub’s tools to help educators work more effectively in the classroom), GitHub Learning Lab (a GitHub learning app), GitHub Jobs (a job posting app for open software development positions),and the GitHub Desktop application (an open-source app for working with GitHub.com or a GitHub Enterprise account) have been added to the program.
GitHub now also offers bounties for vulnerabilities in first-party services under the employee-facing githubapp.com and github.net domains.
GitHub has also expanded the scope of its enterprise products bounties, which previously included Enterprise Server since 2016, to now also include Enterprise Cloud.
Safe-Harbor Changes
Finally, GitHub is adopting a set of legal safe-harbor terms to its policies. Safe-harbor terms are conditions clearly outlining how researchers, who are acting in good faith, can report bugs without facing legal repercussions.
GitHub’s version specifically mandates that research activity remains protected and authorized – even if researchers accidentally overstep the bounty program’s parameters.
“Our safe harbor now includes a firm commitment not to pursue civil or criminal legal action, or support any prosecution or civil action by others, for participants’ bounty-program research activities,” GitHub said. “You remain protected even for good-faith violations of the bounty policy.”
In addition, GitHub said it will do its best to protect researchers against legal risk from third parties who don’t have the same level of safe-harbor terms in place; and researchers won’t be violating site terms if it is specifically for bounty research.
“In creating these terms, we aim to go beyond the current standards for safe-harbor programs and provide researchers with the best protection from criminal, civil and third-party legal risks,” GitHub said.