Google Chrome will soon restrict certain files, like PDFs or executables, from being downloaded via an HTTP connection, if they are loaded on HTTPS webpages.
HTTPS indicates that a website has an encrypted connection. When connecting to an HTTP website, browsers merely look up the IP address and send data over to it in clear text. When using an HTTPS website, on the other hand, the browser checks that it has a legitimate SSL certificate before sending data in encrypted form – preventing man-in-the-middle (MiTM) attacks and more.
With Chrome 68’s 2018 release, Google started to label HTTP websites with an “insecure” warning label in the navigation bar. However, just because websites use an HTTPS connection does not guarantee that they are safe from all threats. For example, phishing landing pages can easily make use of SSL certificates (and many do). Similarly, HTTPS websites can still serve up images, scripts or other file types that are downloaded using the less-secure HTTP connection.
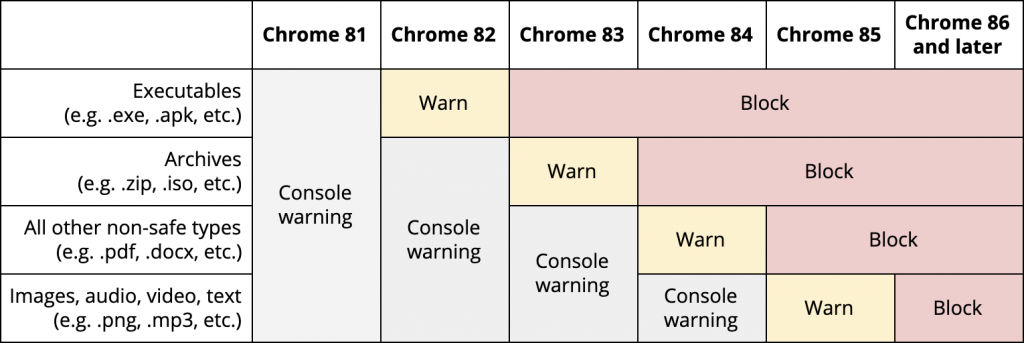
Starting in Chrome 82, set to be released in April, Google wants to uproot this issue by first warning users of, and later blocking, “mixed content downloads,” over HTTP, which could consist of HTTP executables (such as .exe and .apk files), archives (like .zip or .iso files), multimedia files (such as .png, .mp3 files) and all other “non-safe” types (.pdf, .docx, etc.).
“Insecurely-downloaded files are a risk to users’ security and privacy,” said Joe DeBlasio, with the Chrome Security Team, in a Thursday post. “For instance, insecurely downloaded programs can be swapped out for malware by attackers, and eavesdroppers can read users’ insecurely downloaded bank statements. To address these risks, we plan to eventually remove support for insecure downloads in Chrome.”
Google, which first dropped proposals around this idea last April, has outlined a roadmap to eventually ban the files downloads in question over the next seven months. Starting with Chrome 82, Google Chrome will first merely warn users if they are downloading executables using an HTTP connection – then, with Chrome 83 (June 2020) the browser will begin to block them. It will do the same with other mixed content downloads until blocking everything in Chrome 86, set to be released September 2020.
“File types that pose the most risk to users (e.g., executables) will be impacted first, with subsequent releases covering more file types,” according to DeBlasio. “This gradual rollout is designed to mitigate the worst risks quickly, provide developers an opportunity to update sites, and minimize how many warnings Chrome users have to see.”
The gradual rollout will also give developers a head start toward fully migrating to HTTPS by ensuring that downloads on their websites also use HTTPS connections. Google also said that in the current version of Chrome Canary (Google’s web browser aimed for developers) and in Chrome 81 (once it’s released), developers can activate a warning on all mixed content downloads for testing by enabling the “Treat risky downloads over insecure connections as active mixed content” flag at [chrome://flags/#treat-unsafe-downloads-as-active-content].
Fausto Oliveira, principal security architect at Acceptto, told Threatpost the move is a “good idea.”
“We have been using HTTPS as the de facto standard for web pages, however, annoyingly some implementations such as those mentioned by Google (i.e. banking statements) come to your browser unencrypted,” he said. “This allows anyone in the middle to have access to confidential data. I hope that this move by Google leads to other browsers following and also blocking the download of files from unencrypted connections.”
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.