Google on Monday issued 11 security fixes for its Chrome browser, including a high-severity zero-day bug that’s actively being jumped on by attackers in the wild.
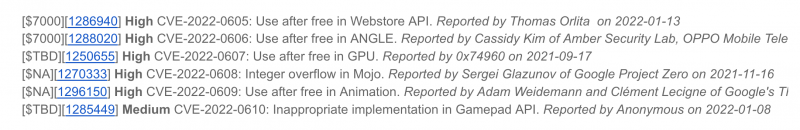
In a brief update, Google described the weakness, tracked as CVE-2022-0609, as a use-after-free vulnerability in Chrome’s Animation component. This kind of flaw can lead to all sorts of misery, ranging from the corruption of valid data to the execution of arbitrary code on vulnerable systems. Such flaws can also be used to escape the browser’s security sandbox.
“Google is aware of reports that an exploit for CVE-2022-0609 exists in the wild,” according to its security update.

To fix the Animation problem, along with 10 other security issues, Google released Chrome 98.0.4758.102 for Windows, Mac, and Linux, due to roll out over coming days or weeks.
Chrome users can fix it straight away, though, by going into the Chrome menu > Help > About Google Chrome.
Given that the zero day is under active attack, updating Chrome should be done ASAP.
Credit for the Animation zero day goes to Adam Weidemann and Clément Lecigne, both from Google’s Threat Analysis Group (TAG).
Monday’s update also plastered over four other high-severity use-after-free flaws found in Chrome’s Webstore API, File Manager, ANGLE and GPU. As well, the company addressed a high-severity integer overflow in Mojo, plus a high-severity heap buffer overflow in Tab Groups. Finally, Google patched a medium-severity issue with inappropriate implementation in Gamepad API.
And So It Begins
This is Chrome’s first zero day of the year, and more are sure to follow. But at least we’ve made it into the new-ish year 10 more days than we managed in 2021, when the first bug to hit arrived on Feb. 4.
Last year delivered a total of these 16 Chrome zero days:
- CVE-2021-21148 – Feb. 4, a vulnerability in its V8 open-source web engine.
- CVE-2021-21166 – March 2, a flaw in the Audio component of Google Chrome.
- CVE-2021-21193 – March 12, a use-after-free flaw in Blink, the browser engine for Chrome that was developed as part of the Chromium project.
- CVE-2021-21220 – April 13, a remote-code execution issue.
- CVE-2021-21224 – April 20, an issue with type confusion in V8 in Google Chrome that could have allowed a remote attacker to execute arbitrary code inside a sandbox via a crafted HTML page.
- CVE-2021-30551 –- June 9, a type confusion bug within Google’s V8 open-source JavaScript and WebAssembly engine.
- CVE-2021-30554 – June 17, a use-after-free bug.
- CVE-2021-30563 – July 15, type confusion in V8.
- CVE-2021-30632 and CVE-2021-30633 – Sept. 13, an out-of-bounds write in V8 and a use-after-free bug in the IndexedDB API, respectively.
- CVE-2021-37973 – Sept. 24, a use-after-free flaw in Portals.
- CVE-2021-37976 and CVE-2021-37975 – Sept. 30, an information leak in core and a use-after-free bug in V8, respectively.
- CVE-2021-38000 and CVE-2021-38003 – Oct. 28, an issue with Insufficient validation of untrusted input in Intents in Google Chrome on Android, and an inappropriate implementation in V8 respectively.
- CVE-2021-4102 – Dec. 13, a use after free in V8.
Join Threatpost on Wed. Feb 23 at 2 PM ET for a LIVE roundtable discussion “The Secret to Keeping Secrets,” sponsored by Keeper Security, focused on how to locate and lock down your organization’s most sensitive data. Zane Bond with Keeper Security will join Threatpost’s Becky Bracken to offer concrete steps to protect your organization’s critical information in the cloud, in transit and in storage. REGISTER NOW and please Tweet us your questions ahead of time @Threatpost so they can be included in the discussion.