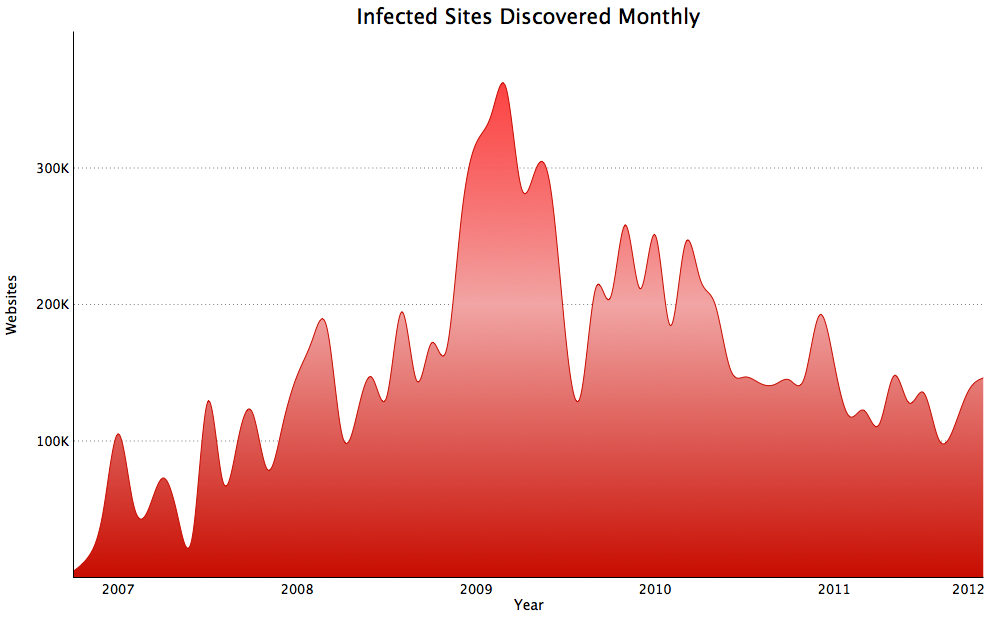
 The number of compromised sites detected each month by Google’s antimalware and anti-phishing systems has been dropping rather steadily from a peak of more than 300,000 in early 2009 and is now down around 150,000. However, the company’s statistics also show that the number of outright malicious attack sites is back on the rise.
The number of compromised sites detected each month by Google’s antimalware and anti-phishing systems has been dropping rather steadily from a peak of more than 300,000 in early 2009 and is now down around 150,000. However, the company’s statistics also show that the number of outright malicious attack sites is back on the rise.
Google uses a number of different methods for detecting malicious sites, potentially malicious downloads and other threats, and one of the key technologies is the company’s Safe Browsing API, which it shares with other browser vendors, as well. The company first announced its online security efforts five years ago, and in looking back at the statistics it has compiled in that time, Google security researchers found a number of interesting things that stood out.
The company found that while it is still detecting about 9,500 malicious sites every day, the number of legitimate sites that have been compromised to serve malware has been dropping for the last few years. Those compromised sites typically are used in drive-by download attacks to install malware on victims’ machines or use them as part of a botnet or to send spam. Some of those attacks also involve the use of other tactics such as social engineering or a series of redirects to push users to the compromised sites.
“When a legitimate website is compromised, it’s usually modified to include content from an attack site or to redirect to an attack site. These attack sites will often deliver “Drive by downloads” to visitors. A drive by download exploits a vulnerability in the browser to execute a malicious program on a user’s computer without their knowledge,” Niels Provos of Google’s security team wrote in a blog post.
“As companies have designed browsers and plugins to be more secure over time, malware purveyors have also employed social engineering, where the malware author tries to deceive the user into installing malicious software without the need for any software vulnerabilities. A good example is a “Fake Anti-Virus” alert that masquerades as a legitimate security warning, but it actually infects computers with malware. “
One thing that’s left unsaid in the Google report is how many of the compromised sites are re-infected once they’re flagged by Google or another company and cleaned up. In some cases, sites are infected several times if the underlying vulnerability that’s leading to the compromise isn’t addressed.
Google’s statistics also show that the number of phishing sites, which had declined sharply through most of 2011, began to increase rapidly again toward the end of the year. The company’s stats show that the number of phishing sites found each month was down toward 100,000 near the end of last year, but has spiked again and is now up above 300,000. It’s not clear exactly what’s behind the big increase, but one explanation may be that phishers now are changing the URLs for their sites as often as every hour, jacking up the total volume of sites.
“Many phishers go right for the money, and that pattern is reflected in the continued heavy targeting of online commerce sites like eBay & PayPal. Even though we’re still seeing some of the same techniques we first saw 5+ years ago, since they unfortunately still catch victims, phishing attacks are also getting more creative and sophisticated. As they evolve, we improve our system to catch more and newer attacks,” Provos wrote.









