Google removed a handful of malicious apps from its Play marketplace recently that were found manipulating ad traffic, sending premium text messages, and downloading additional plugins.
Bernhard Grill, Megan Ruthven, and Xin Zhao, security software engineers with the company, said Monday they detected the family of potentially harmful applications–one of the largest they’ve ever come across–during a routine ad traffic quality evaluation.
Applications from the family, which Google dubbed Chamois, showed users deceptive graphics that tricked them into clicking through and downloading additional apps that committed ad fraud.
Unbeknownst to the user, the apps were sending premium text messages, downloading and executing unwanted plugins, and installing invisible apps in the background.
It’s unlikely a victim would even realize they were infected, Google says, because the Chamois apps didn’t appear in a device’s app lists, meaning they couldn’t see the apps or uninstall them.
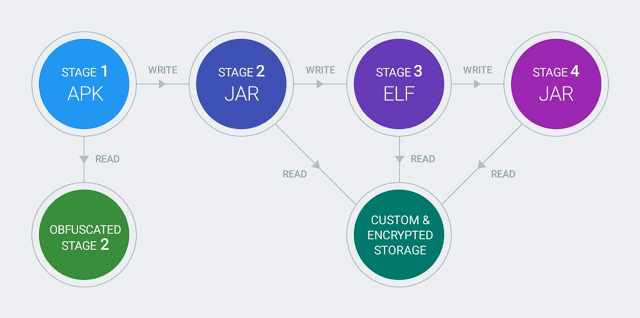
Apps associated with Chamois had a knack for evading detection, researchers said. The apps featured both a multistage payload and custom encrypted storage, two traits that took Google a little longer to decipher. Because they constantly changed file formats, first from an .APK file, then a .JAR file, then an .ELF file, the malicious aspects of the apps were tough to nail down.
“This multi-stage process makes it more complicated to immediately identify apps in this family as a PHA because the layers have to be peeled first to reach the malicious part,” the researchers wrote.
The company used its malware scanner, Verify Apps, to root out the family of adware. The scanner routinely checks activity on an Android device and informs users if it observes any harmful activity. After a malicious app is identified the feature gives users a chance to uninstall it.
Google discussed the system and the scoring system that drives it, DOI, or Dead or Insecure, earlier this year. The scoring system is based around apps having a similar device retention rate, Google’s Ruthven said in January. If the rate trips a threshold, Google combines it with other security data to flag an app. The scanner has helped flag thousands of apps belonging to families similar to Chamois like Ghost Push, Gooligan, and Hummingbad over the past 10 months.
According to Grill, Ruthven, and Zhao, “many apps downloaded by Chamois were highly ranked by the DOI scorer.”
Google didn’t release numbers around exactly how many devices were ensnared by the Chamois botnet. HummingBad, which sets up a persistent rootkit on devices to carry out ad fraud, controlled 10 million devices worldwide and raked in $300,000 a month according to researchers last summer.