A proof of concept bypass of Google’s reCaptcha V2 verification system, posted online Tuesday, uses Google’s own web-based tools to pull off the skirting of the system.
The tool dubbed ReBreakCaptcha “lets you easily bypass Google’s reCaptcha v2 anywhere on the web,” according to the author of the tool that is only identified as East-Ee Security.
Google rolled out reCaptcha in 2014 to most of its public services in an effort defeat bots and scripts that can speedily register hundreds of free web-service accounts at a time. CAPTCHA stands for Completely Automated Public Turing test to tell Computers and Humans Apart. ReCaptcha is Google’s name for its own technology and service that today uses image, audio or text challenges to verify a human is signing into an account.
East-Ee Security’s ReBreakCaptcha method is able to defeat reCaptcha V2 security via a script that uses Google’s own APIs to capture audio challenges as sound files. Then it uses speech-to-text technology to convert audio into text answers that are then inputted as text-based solutions to audio-based challenges used in reCaptcha V2.
To pull this off, first East-Ee Security devised a way to only access audio reCaptcha challenges. That’s not too difficult because every challenge includes a link, in the form of a tiny pair of headphones, that indicates an audio challenge request is available, according to the author.
“Some of you may notice that instead of an audio challenge, sometimes you get a text challenge,” the researcher writes. “To bypass it and get an audio challenge, you simply click the ‘Reload Challenge’ button until you get the correct type.”
Once the audio challenge is presented reCaptcha allows you to either play the audio file from the webpage or download it.
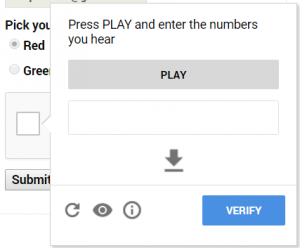 “Let’s download the audio file and send it to Google Speech Recognition API. Before doing so, we will convert it to a ‘wav’ format, which is requested by Google’s Speech Recognition API. Now we have the audio challenge file and are ready to send it to Google Speech Recognition. How can this be done? Using (Google’s own) API,” the author wrote.
“Let’s download the audio file and send it to Google Speech Recognition API. Before doing so, we will convert it to a ‘wav’ format, which is requested by Google’s Speech Recognition API. Now we have the audio challenge file and are ready to send it to Google Speech Recognition. How can this be done? Using (Google’s own) API,” the author wrote.
Next, the author writes, “We will send the ‘wav’ audio file and the Speech Recognition will send us back the result in a string (e.g. ‘25143’). This result will be the solution to our audio challenge,” East-Ee Security explains.
The author of the post posted a proof of concept script using Python on GitHub. “It utilizes all of the presented stages of the technique for a fully-automated bypass of ReCaptcha v2.”
Neither Google nor East-Ee Security replied to requests for comment.
Threatpost did reach out to a number of software developers that confirmed the proof of concept script worked, but only when their tests were from a public IP address.
This is also not the first time Google’s reCaptcha service has been bypassed. Last year, at Black Hat Asia, security researchers from Columbia University published a paper I’m not a human: Breaking the Google reCAPTCHA (PDF).
That research was based on bypassing the Google reCaptcha V2’s security checks for detecting suspicious browser attributes or behavior. It also based its bypass technique on identifying and predicting images used in reCaptcha. According the paper’s authors, their technique automatically solved 70.78 percent of the image reCaptcha challenges, while requiring only 19 seconds per challenge.
East-Ee Security did not provide any comparable data for its ReBreakCaptcha bypass.











