Google removed a nasty Trojan from Google Play earlier this week that could have rooted Android devices and injected malicious code into an infected device’s system library.
The malware, dubbed Dvmap, was disguised as a game that had been downloaded more than 50,000 times prior to its removal, according to Roman Unuchek, a senior malware analyst with Kaspersky Lab who uncovered the Trojan.
Unuchek found the malware on May 19, while analyzing results from an internal system he monitors to find new strains of rooting malware. Google removed the Trojan on Tuesday after Kaspersky Lab reported it to the company on May 25.
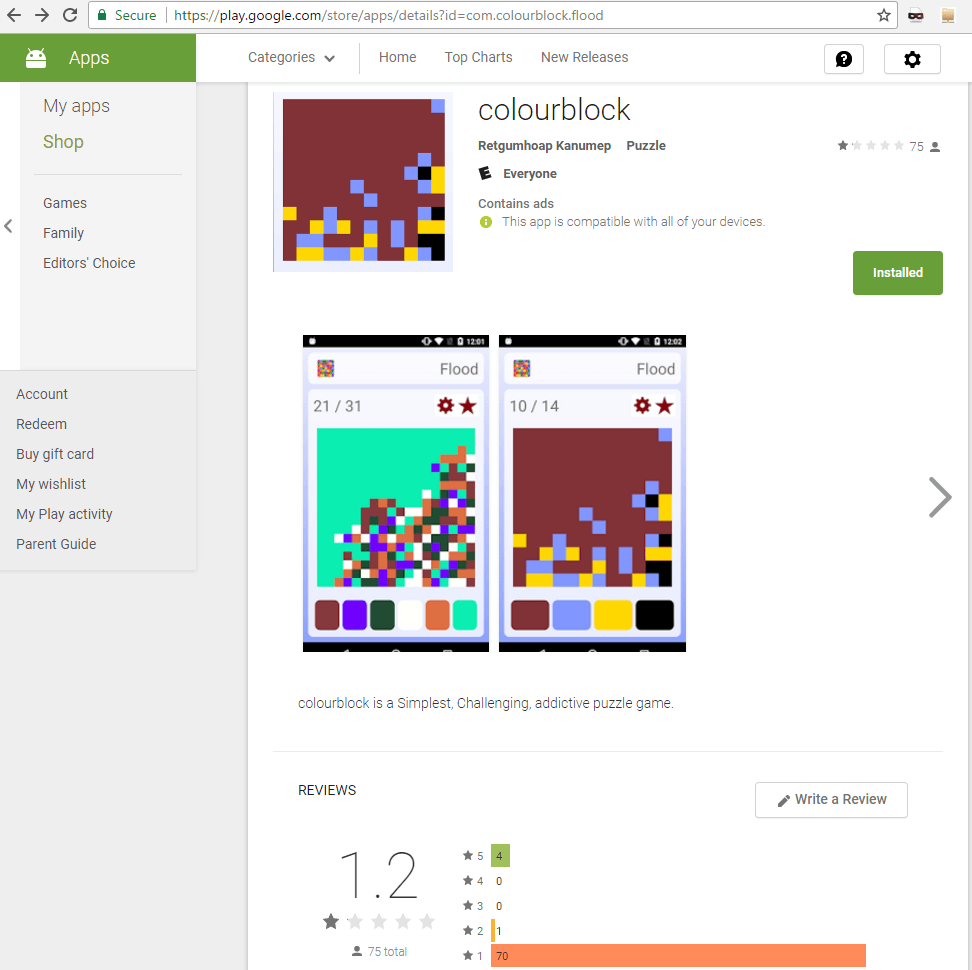
The game, “colourblock,” was billed as a “simplest, challenging, addictive” puzzle game in which users change the colors of blocks in order to to change the color of the whole screen.
Once installed, Dvmap attempts to gain root access by launching a start file which checks the version of Android running on the device and which library to inject its code into. If successful, the malware goes ahead and installs tools – some written in Chinese – to connect the Trojan to its command and control server.
Unuchek, who described Dvmap today in a post to Securelist, says it’s unclear if the malware is ready for primetime yet though. The researcher observed modules within the malware firing information back to the command and control server, but the server never responded back, something that hints the malware either isn’t fully ready, or implemented.
Modifying system libraries is not a failsafe practice, Unuchek cautions. The researcher says in some instances the malware can cause devices to crash by overwriting existing code.
It appears the criminals behind Dvmap uploaded a clean version of the game to Google Play at the end of March, then updated it with a malicious version – on and off – five times over the course of four weeks. The strategy likely helped the attackers bypass the marketplace’s security checks, Unuchek says.
VerifyApps, Google’s malware scanner for Android, can check new and installed software on devices against a list of known malware, but isn’t immune to Dvmap, Unuchek says.
“The newly patched system libraries execute a malicious module which can turn off the ‘VerifyApps’ feature,” Unuchek said, “It then switches on the setting ‘Unknown sources’ which allows it to install apps from anywhere, not just the Google Play Store. These could be malicious or unsolicited advertising apps.”
Android malware that helps attackers gain root access isn’t exactly new. Researchers at Kaspersky Lab discovered an Android banking trojan that tried to gain root privileges on devices last September. While that app wasn’t in the Google Play marketplace, an app that Unuchek stumbled upon in September was. The app, masquerading as a Pokémon GO game, also gave attackers root access. On top of that, it was more popular than the game Unuchek found last week; having been downloaded more than 500,000 times before Google removed it.
Unuchek says one of the traits that makes Dvmap different, the fact the malware can inject itself into system libraries, is particularly concerning.
“Injecting code into the system library is a new thing for Android malware and very powerful thing,” Unuchek told Threatpost, “But at the same time, it is very dangerous method that can break the device. I think that we’ll see a few more Trojans doing so in future, but it is too dangerous functionality for most trojans and its hard to implement.”
Kaspersky Lab and Unuchek are encouraging users who either downloaded the game or believe they’re infected to back up their data and perform a full factory data reset to mitigate the malware.
“Users who don’t have the security in place to identify and block the threat before it breaks in have a difficult time ahead,” Unuchek said of the malware.