A spike in recent phishing and business email compromise (BEC) attacks can be traced back to criminals learning how to exploit Google Services, according to research from Armorblox.
Social distancing has driven entire businesses into the arms of the Google ecosystem looking for a reliable, simple way to digitize the traditional office. Armorblox co-founder and head of engineering Arjun Sambamoorthy just published a report detailing how now-ubiquitous services like Google Forms, Google Docs and others are being used by malicious actors to give their spoofing attempts a false veneer of legitimacy, both to security filters and victims.
“Open APIs, extensible integrations and developer-friendly tools mean that entire virtual offices — complete with virtual workflows — can exist in a Google ecosystem,” Sambamoorthy wrote. “Unfortunately, Google’s open and democratized nature is being exploited by cybercriminals to defraud individuals and organizations of money and sensitive data.”
The report gives several specific examples of how Google Services help attackers with their schemes.
Google Forms
One campaign used a Google Form and an American Express logo to try and get victims to enter sensitive information.
“Hosting the phishing page on a Google Form helps the initial email evade any security filters that block known bad links or domains,” according to Sambamoorthy. “Since Google’s domain is inherently trustworthy, and Google forms are used for several legitimate reasons, no email security filter would realistically block this link on ‘day zero.'”
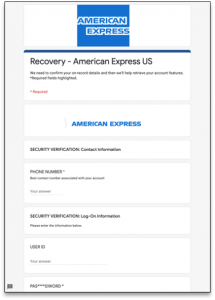
The American Express scam. Source: Armorblox.
Another attack Sambamoorthy found used a fictious letter from a childless widow looking for someone to whom she could bequeath her fortune. The link in the email leads to a Google Form with a blank question field. In this instance, the Google Form helps attackers with the social engineering strategy, the report said.
“Many people will feel the email is suspicious after going through the content and visiting this dummy form,” he continued. “But some people will submit the only option allowed by the form, or they will send a reply to the address provided in the email. This allows attackers to shortlist the most naive and emotionally susceptible email recipients, who will be prime targets for follow-up emails from the childless widow.
Google Firebase, Google Sites & Google Docs
Google’s mobile platform Firebase was used in another scheme to host a phishing page, which allowed it to sneak through email filters for the same reason – because Firebase is trusted.
In a Google-services-powered payroll diversion fraud scam that Sambamoorthy highlighted, a scam email link sent recipients to a Google Doc file to “confirm” their payment details.
And in yet another attack, an email was delivered to victims, purportedly from their own IT team, asking them to review a secure message on Microsoft Teams from a colleague. The link led to web page with a bogus Office 365 login portal hosted on Google Sites.
“The malice of the page’s intent was hidden behind the legitimacy of the page’s domain,” Sambamoorthy added. “This page would pass most eye tests during busy mornings (which is when the email was sent out), with people happily assuming it to be a legitimate Microsoft page.”
Hijacking Google Services: A Trend
The ability for malicious actors to leverage Google Services for their activities is starting to emerge as a full-fledged trend.
At the beginning of November, researchers found 265 Google Forms impersonating brands like AT&T, Citibank and Capitol One and even government agencies like the Internal Revenue Service and the Mexican Government used in phishing attacks.
The forms were removed by Google after researchers from Zimperium reported them.
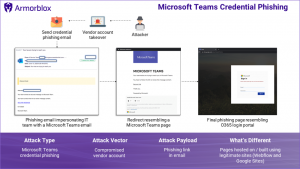
The Teams phish. Source: Armorblox.
Just days earlier, scammers were found to be using a legitimate Google Drive collaboration to trick victims into clicking on malicious links.
Even Google Calendar has been abused in the past, in a sophisticated cyberattack that targeted mobile Gmail users through fraudulent, unsolicited meeting notifications.
For its part, Google stresses the company is taking every measure to keep malicious actors off their platforms.
“We are deeply committed to protecting our users from phishing abuse across our services, and are continuously working on additional measures to block these types of attacks as methods evolve,” a Google spokesperson told Threatpost by email.
The statement added that Google’s abuse policy prohibits phishing and emphasized that the company is aggressive in combating abuse.
“We use proactive measures to prevent this abuse and users can report abuse on our platforms,” the statement said. “Google has strong measures in place to detect and block phishing abuse on our services.”
Sambamoorthy told Threatpost that the security responsibility does not rest on Google alone and that organizations should not rely solely on Google’s security protections for their sensitive data.
“Google faces a fundamental dilemma because what makes their services free and easy to use also lowers the bar for cybercriminals to build and launch effective phishing attacks,” he said. “It’s important to remember that Google is not an email security company — their primary responsibility is to deliver a functioning, performant email service.”
Sambamoorthy said two-factor authentication (2FA) and maintaining strong passwords with a password manager are the best ways for users to protect themselves. Besides those best practices, the report recommended “rigorous eye tests” of emails “related to money and data.”
Organizations, he said, should establish basic security policies and set up mechanisms which are able to adapt to new and evolving threats.
“Security has an important ‘process’ component, so organizations should ensure they have the right controls, checks, and balances in place to protect users and data,” Sambamoorthy said. “Since these attack patterns are always evolving, organizations should invest in security technologies that have built-in feedback mechanisms. These mechanisms should learn from new attacks and refine detection algorithms with time ”











