Google this week shared with developers security enhancements it has added to the new Nougat version of Android and additional security features for webmasters via Safe Browsing to help pinpoint harmful content on websites.
Under the banner of its nine-year-long Safe Browsing initiative, Google introduced new features that protect against threats such as deceptive sites and unwanted software that may reside on a website. Access to the tools is via Google’s Search Console and within the Security Issues report feature.
Google announced the update Tuesday and said the enhancements bolster the Security Issues reporting mechanism. Added to the reporting system are new security parameters to monitor things such as malware, deceptive pages, harmful downloads and “uncommon” downloads.
The goal, said Kelly Hope Harrington, with Google Safe Browsing Team, is to give webmasters context and more details about threats on their system and make browsing websites safer for users. The new features offer webmasters tailored recommendations for each type issue that crops up.
In the example provided on the blog announcing the feature enhancements, Google showed a console where malware, harmful downloads and deceptive pages were red-flagged.
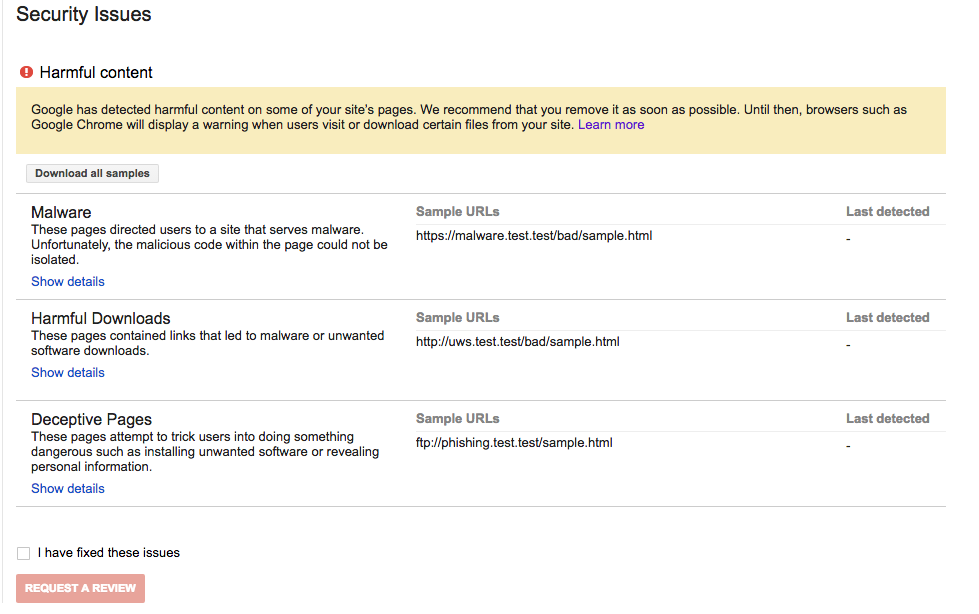
In one example the Security Issues console showed the warning to a webmaster, “Google has detected harmful content on some of your site’s pages.” The report allowed a webmaster to download samples and detailed each incident.
“These pages directed users to a site that serves malware. Unfortunately, the malicious code within the page could not be isolated,” read a description under the malware banner.
Android Security Roundup
Post-QuadRooter, Google on Tuesday posted a roundup of security enhancements it brought to Android 7.0, or Nougat, released Aug. 22.
Over the past several months, Google has dealt with a number of high-profile security vulnerabilities. On Aug. 8 four critical vulnerabilities were found in Qualcomm chips used in 900 million Android devices. The flaws, called Quadrooter, could give hackers complete system control and impacted popular handsets from leading OEM device makers.
On Tuesday, Google patched a potentially massive Android bug that could allow attackers to compromise – or brick – Android devices dating back to version 4.2.
In her blog posted Tuesday, Xiaowen Xin, member of the Android Security Team, recapped the work that went into snuffing out nagging security issues tied to problematic Android components such as MediaServer in Android 7.0. Xin wrote:
“Over the course of the summer, we previewed a variety of security enhancements in Android 7.0 Nougat: an increased focus on security with our vulnerability rewards program, a new Direct Boot mode, re-architected mediaserver and hardened media stack, apps that are protected from accidental regressions to cleartext traffic, an update to the way Android handles trusted certificate authorities, strict enforcement of verified boot with error correction, and updates to the Linux kernel to reduce the attack surface and increase memory protection.”
One of those Nougat security enhancements included a new Direct Boot and Encryption feature. The Direct Boot feature allows an Android 7 user with an encrypted phone to access key smartphone features such as the phone app and alarm clock without having to unlock their phone.
With Nougat, Google also has moved to file-based encryption. “File-based encryption better isolates and protects individual users and profiles on a device by encrypting data at a finer granularity,” Xin wrote.
Google also claims to have hardened and re-architected its problem-plagued Mediaserver component. The Mediaserver component was tied to the infamous Stagefright attacks last year. With Nougat, Mediaserver will have fewer permissions and less access to the kernel, limiting the damage that can be done on an Android 7.0 device.
“We’ve modularized the media stack to put different components into individual sandboxes and tightened the privileges of each sandbox to have the minimum privileges required to perform its job,” Xin wrote. He said that this containment approach limits significantly the exposed kernel attack surface.
At least a dozen more Android OS security additions to Nougat were highlighted by Xin, including: kernel hardening, a new v2 APK signature scheme, SELinux and a Verified Boot feature that prevents compromised devices from booting.