Spammers and cybercriminals have revived email-based attacks in the last year, giving new life to macro-based malware hidden in Word documents, and with greater intensity of late, .js files that run JavaScript on infected clients, largely to download malware from an attacker’s site.
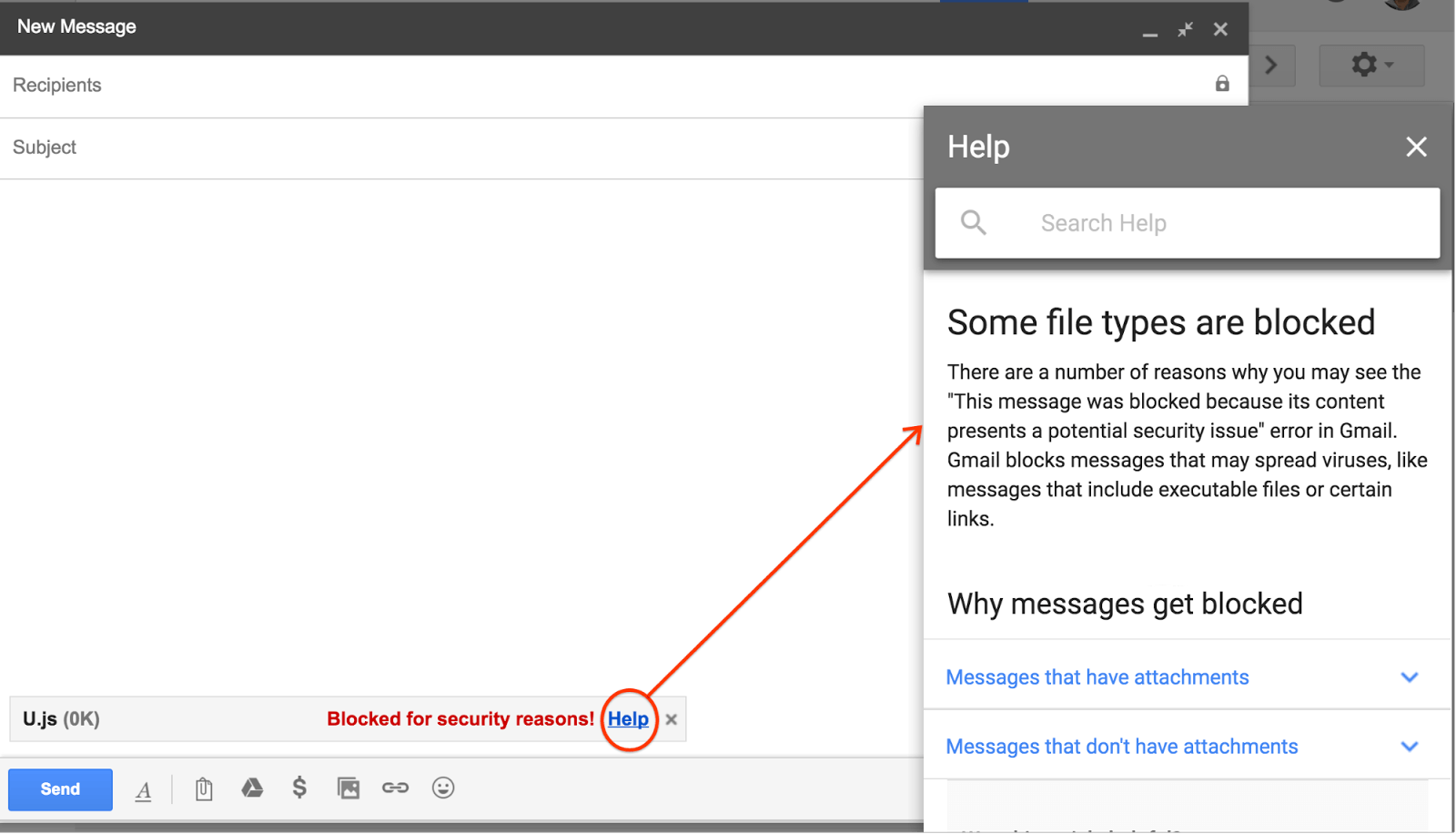
Google responded on Wednesday with news that it would begin blocking .js files in Gmail attachments, starting Feb. 13, because of such security concerns.
“Similar to other restricted file attachments, you will not be able to attach a .js file and an in-product warning will appear, explaining the reason why,” Google said in an announcement published on the G Suite website.
Google already blocks more than 30 file types as attachments in Gmail, including .cmd, .exe, .jar, .lib, .scr, .vbs and many others.
Google acknowledges that there may be business cases necessitating the sharing of .js files, but will not allow it in email, instead suggests sharing via Google Drive or other cloud-based storage options.
The Feb. 13 start date will be rapid release only, Google said, with a scheduled release set for two weeks later.
The move is a response to the growing threat posed by these file types, which are being used in cybercrime operations to spread banking malware, ransomware, click-fraud malware and adware to users. Over the weekend, the SANS Internet Storm Center warned of a new campaign started by criminals known for spreading Cerber ransomware. They were using email-based attacks and .js files buried inside of two .zip archives to download the Sage 2.0 ransomware from a third-party site.
The same campaign also relies on macro malware to infect endpoints with crypto-ransomware.
Another campaign last September used emails spoofing popular business sources to spread a JavaScript-based downloader that was downloading click-fraud malware such as Kovter and Miuref, as well as the Corebot Trojan, which started out as malware focused on stealing credentials, before it was transitioned into full-fledged banking malware.
Attackers were also spreading Locky ransomware in this way, using a .js downloader—among others—to grab the malware from the web once a machine had been compromised. Locky was a particularly worrisome threat early last year when it was the center of high-profile infections at hospitals in Hollywood and Kentucky.