Search giant Google said it is quintupling the top bounty it will pay for information on security holes in its products to $20,000.
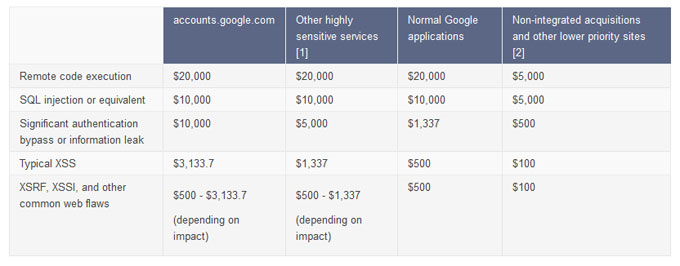
In a post on the company’s Online Security Blog, Google said it was updating its rewards and rules for the bounty program, which is celebrating its first anniversary. In addition to a top prize of $20,000 for vulnerabilities that allow code to be executed on product systems, Google said it would pay $10,000 for SQL injection and equivalent vulnerabilities in its services and for certain vulnerabilities that leak information or allow attackers to bypass authentication or authorization features.
The new rewards represent a big jump from the previous top reward of $3,133.70, which the company announced in July, 2011 and is among the top prizes for product vulnerabilities offered by any software maker. The company said that it will continue to pay the $3,133.7 bounty for certain types of cross site scripting, cross site request forgery and other “high impact” flaws in “highly sensitive applications.” (The unusual figure is a numeric representation of “eleet” – hacker slang for “elite.”)
In a post, researchers Michal Zalewski and Adam Mein called the bounty program a success. Google has received 780 qualifying vulnerability reports and paid around $460,000 in bounties to around 200 individuals.
The company said it would also begin distinguishing between the prices paid for vulnerabilities in high risk applications – such as Google Wallet – and those in lower risk applications and products from what it terms “non integrated acquisitions.”









