Google said key business services were knocked offline Monday when web traffic to a portion of its cloud platform was hijacked and routed through Chinese, Nigerian and Russian ISPs.
The incident lasted for 74 minutes in what is called a Border Gateway Protocol (BGP) hijacking.
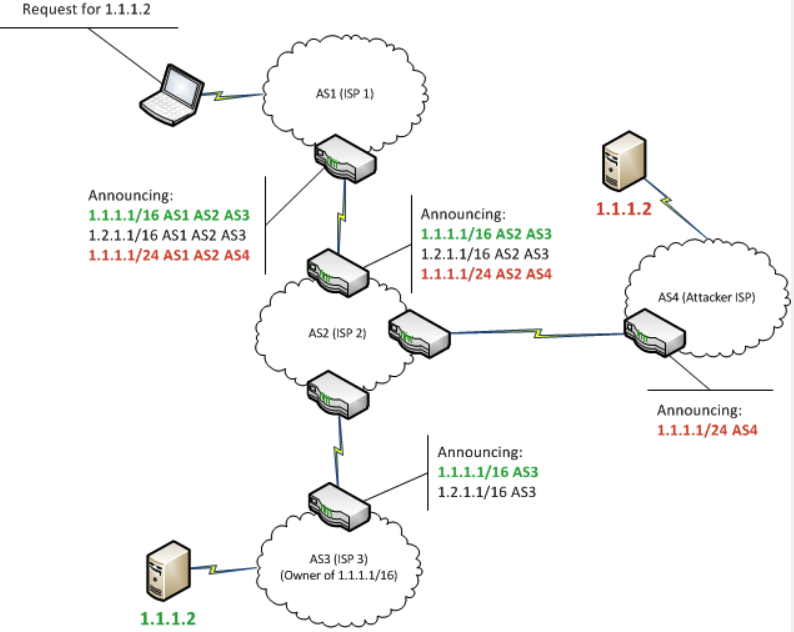
BGP is a protocol that defines the way IP packets travel across the internet; BGP hijacking is a well-known technique used by attackers to reroute, intercept and modify internet traffic. However, security experts said they don’t have enough information to determine whether Monday’s hijacking was malicious or not.
Ameet Naik, a technical marketing manager with the security firm ThousandEyes, said the hijacking knocked Google’s G Suite, Google Search and Google Analytics services offline between 1:00 p.m. and 2:23 p.m. Pacific time in western half of the United States, and in other regions around the globe.
The source of the BGP hijacking, he said, was a BGP peering relationship between a Nigerian ISP called MainOne Cable Company and the parent company of the ISP China Telecom. Security experts at BGPmon added more details via Twitter, noting that MainOne configured its edge routers erroneously with hosting IP addresses normally assigned to Google’s data-center network.
https://twitter.com/bgpmon/status/1062120256737406976
“This is what we know: Starting at 2018-11-12 21:12 UTC Nigerian ISP AS37282 ‘MainOne Cable Company’ leaked 212 @google prefixes to China Telecom. Causing traffic to be redirected and dropped,” wrote BGPmon on Twitter.
That triggered nearby ISPs to re-route traffic destined to Google services through MainOne’s network, instead of normal BGP routes.
“Appears that Nigerian ISP (AS37282) ‘MainOne Cable Company’ leaked many @google prefixes to China Telecom, who then advertised it to (AS20485) TRANSTELECOM (Russia). From there on, others appear to have picked this up,” BGPmon continued via Twitter.
Overall, for its part, ThousandEyes detected over 180 prefixes affected by the route leak, which covers a vast scope of Google services.
“This incident at a minimum caused a massive denial of service to G Suite and Google Search,” Naik wrote in a posting on Tuesday evening. “However, this also put valuable Google traffic in the hands of ISPs in countries with a long history of internet surveillance.”
In communications with its customers, Google said: “We will conduct an internal investigation of this issue and make appropriate improvements to our systems to help prevent or minimize future recurrence.”
Monday’s incident was the latest in a string of similar incidents that many trace back to China Telecom. Last month, researchers Chris C. Demchak and Yuval Shavitt released a report [PDF] alleging that for years China Telecom has been misdirecting internet traffic through China using BGP forwarding tables.
ThousandEyes’ Naik also noted that BGP-related incidents have been on the rise. In April, it said that it had spotted a cryptocurrency heist tied to a BGP hijacking, and in 2017 a large number of e-commerce and financial services websites were impacted when Russia’s leading telcom company, Rostelecom, suffered a BGP-related incident.
Inside BGP Hijacking
According to an overview of BGP hijacking by Bishop Fox senior security analyst Zach Julian, the attack takes advantage of how data travels from its source to its destination.
“Internet-level BGP hijacking is performed by configuring an edge router to announce prefixes that have not been assigned to it. If the malicious announcement is more specific than the legitimate one, or claims to offer a shorter path, the traffic may be directed to the attacker,” Julian wrote.
“Attackers will frequently target unused prefixes for hijacking to avoid attention from the legitimate owner. By broadcasting false prefix announcements, the compromised router may poison the Routing Information Base (RIB) of its peers,” he continued.
Julian warned that because the architecture of BGP does not support the ability to verify the accuracy of the routing information, BGP hijacking is difficult to prevent.