The numbers are in, and judging by them, OSS-Fuzz, the program Google unveiled last December to continuously fuzz open source software, has been a success.
In five months the effort has unearthed more than 1,000 bugs, a quarter of them potential security vulnerabilities, Google says.
OSS-Fuzz, still in beta mode, is built on fuzzing engines such as libFuzzer, sanitizers such as Address Sanitizer, and a distributed fuzzing architecture that catalogs statistics as they pop up. The project was one of two Google unveiled last December. It also released Project Wycheproof, a collection of unit tests designed to help cryptographers check for weaknesses in cryptographic algorithms.
Engineers behind the platform–Oliver Chang and Abhishek Arya with Chrome Security, Kostya Serebryany, software Engineer with Dynamic Tools, and Josh Armour, a Security Program Manager with Google–wrote a blog post Monday to fill the public in on the last five months.
While it can’t disclose all of the bugs because some are still restricted, Google says the project has helped find bugs in all types of open source software, including 10 bugs in FreeType2, 17 in FFmpeg, 33 in LibreOffice, eight in SQLite 3, 10 inGnuTLS, 25 in PCRE2, nine in gRPC, and seven in WireShark.
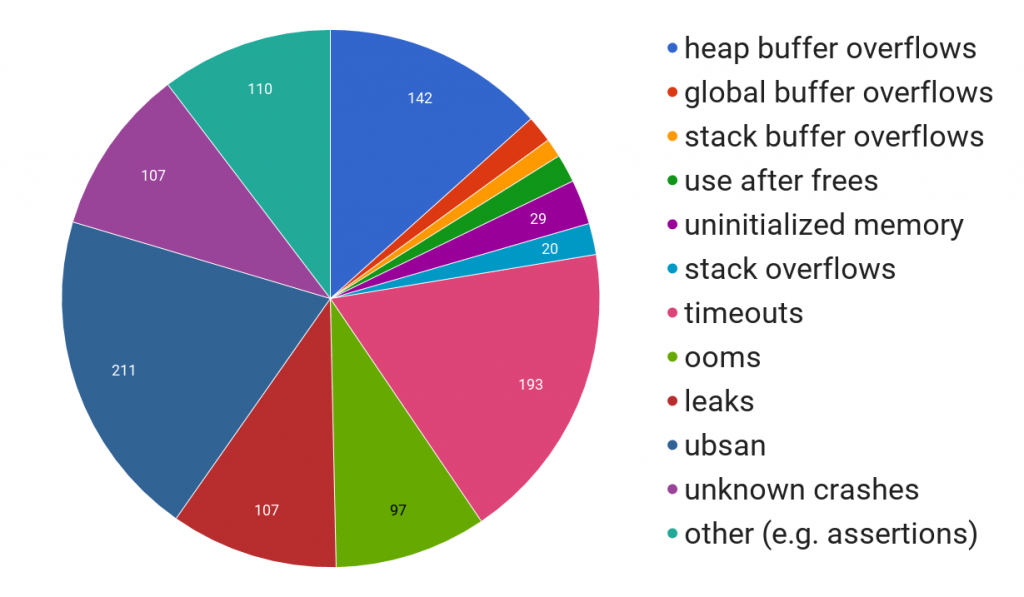
Roughly 50 percent of the bugs OSS-Fuzz has identified so far fall under ubsan, or UndefinedBehaviorSanitizer, or leaks. A good chunk are heap buffer overflows, unknown crashes, and out of memory terminations (oom), Google said.
In December, Google said the project was producing four trillion test cases a week. On Monday, engineers said activity on the platform has spiked, and that it’s now processing more than twice that figure in even less time: 10 trillion test inputs a day.
While the statistics behind OSS-Fuzz are positive news, Google also said something else that should put a smile on developers’ faces. The engineers said the company wants to help developers behind some of the open source projects, many which operate on a shoestring budget, better fund their projects.
The company announced Monday it will extend its current patch rewards program to include rewards for integrating fuzz targets into OSS-Fuzz. There are some prerequisites. Google is mandating the projects have a large user base or be critical to global IT infrastructure. Those that are eligible will receive $1,000 for “initial integration” and up to $20,000 for what it calls ideal integration.
The engineers said they’re broadening the scope of the program in hopes of recruiting more open source programs.
“We believe that user and internet security as a whole can benefit greatly if more open source projects include fuzzing in their development process. To this end, we’d like to encourage more projects to participate and adopt the ideal integration guidelines that we’ve established,” the engineers wrote.
Open source projects are required to have a large user base in order to join OSS-Fuzz as it is. Since the project is based around disclosing and fixing bugs, developers have to subject themselves to Google’s 90-day disclosure deadline.
The company claims it’s begun reaching out to preliminary projects eligible for the $1,000, but is also directing interested parties to a submission form on its site.
Google is one of several companies over the last several months to extend an olive branch to open source developers.
In March, the bug bounty platform HackerOne announced it would offer open source projects free access to a version of its platform called HackerOne Community Edition. Eligible projects receive a Professional subscription of the service, including vulnerability submission coordination, analytics, and bounty programs, for free.
HackerOne’s CEO Marten Mickos told Threatpost at the time the move was done to give back and to ensure that open source projects can get as much support as possible.