Android malware called Gooligan is being blamed for 1 million breached Google accounts. The malware is still active, according Check Point Software Technologies, and is responsible for an additional 13,000 new breaches of Android devices daily.
“We believe that it is the largest Google account breach to date,” Check Point wrote in a technical overview of the malware.
In a blog post, Adrian Ludwig, Google’s director of Android security, acknowledged the mass infections and identified Gooligan as a variant of Ghost Push malware first identified in 2014. Check Point said it also recognizes Gooligan as a variant of the Android malware campaign found by its researchers last year that was part the malicious Windows backup application SnapPea.
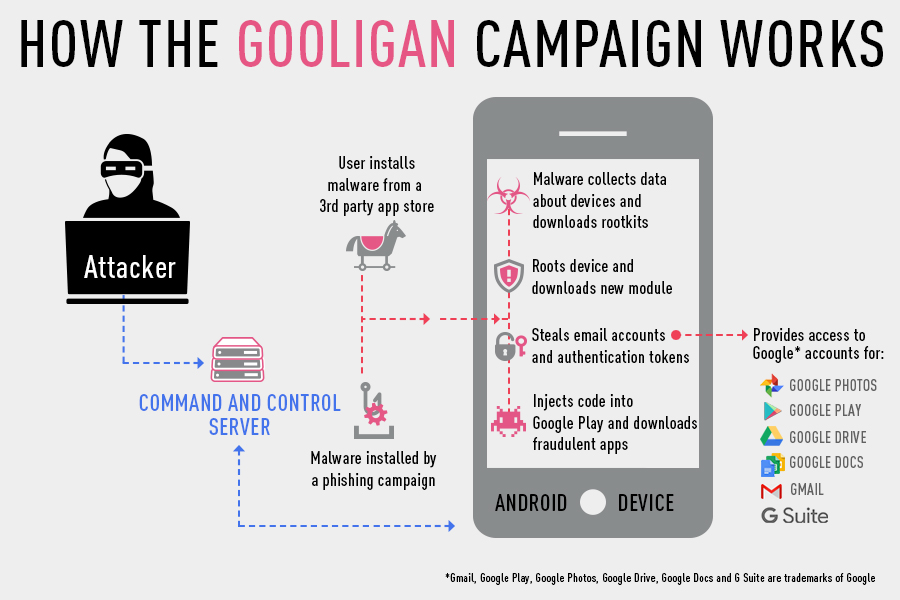
Check Point reported Wednesday that at least 86 Android apps available in third-party marketplaces were laced with Gooligan malware that ultimately allowed hackers to breach Google accounts. Check Point said attackers are enticing victims to download free versions of popular paid Android apps via third-party app stores hosting Gooligan-infected apps such as StopWatch, Flashlight Free and Pedometer.
“The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device,” Check Point researchers wrote. “Our research team has found infected apps on third-party app stores, but they could also be downloaded by Android users directly by tapping malicious links in phishing attack messages.”
Vulnerable Android handsets include devices running OS versions 4 (Ice Cream Sandwich, Jelly Bean, and KitKat) and 5 (Lollipop). Check Point estimates 74 percent of Android devices in use today are vulnerable to the malware. Once a malicious Gooligan app is installed on a vulnerable device, attackers can push either the rootkit VROOT or Towelroot from a command-and-control server.
With root access established on the handset, researchers said, attackers have one main objective and that is to breach the victim’s Google account via the theft of authentication token information. That gives attackers access to the breached victim’s Google services such as Google Play, Gmail, Google Docs, Google Drive and Google Photos.
However, despite having access to a potential treasure trove of personal account data, Google’s Ludwig said that there is no evidence that Gooligan adversaries have accessed user data in any of the 1 million breached accounts.
“We used automated tools to look for signs of other fraudulent activity within the affected Google accounts. None were found,” Ludwig wrote. He added that the motivation behind Gooligan, as with Ghost Push, is to “promote apps, not steal information.”
To that end, Check Point said that phones rooted by hackers download a module that injects code into Google Play to mimic user behavior. This gives hackers the ability to generate revenue via ads and fake app referrals. Researchers say the technique is similar to those used by hackers behind the mobile malware HummingBad that reportedly earned criminals $300,000 a month last year.
As with HummingBad, Gooligan installs apps from Google Play and rates them to both raise their reputation and also install adware on infected handsets to generate revenue. Check Point explains:
“Ad servers, which don’t know whether an app using its service is malicious or not, send Gooligan the names of the apps to download from Google Play. After an app is installed, the ad service pays the attacker. Then the malware leaves a positive review and a high rating on Google Play using content it receives from the C&C server.”
Approximately 20 percent of Gooligan-infected devices are located in the Americas, 57 percent in Asia, 15 percent in Africa and 9 percent in Europe, according to researchers.
To guard against Gooligan, Check Point says end users should forgo downloading apps from third-party Android app stores and check to make sure their email address isn’t on its list of compromised Google accounts. If a Google account has been breached advice includes a re-flashing of Android devices associated with account and a resetting of the account password. Check Point has developed a tool that will check whether a user’s Google address is on its list of breached accounts.