![]() One of the great things about the Internet is that things can live on indefinitely. Unfortunately, that long life expectancy applies to malware, as well.
One of the great things about the Internet is that things can live on indefinitely. Unfortunately, that long life expectancy applies to malware, as well.
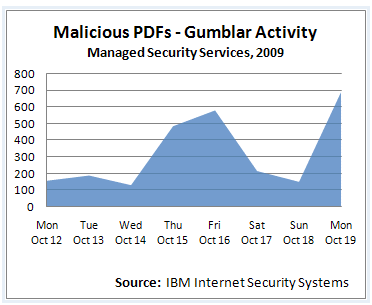
The Gumblar botnet, which has been active for several months now but had quieted down somewhat, is making a comeback in a big way. IBM ISS’s X-Force research team has been following Gumblar’s activity and has found that the malware’s creators have refined its capabilities and added some new exploits to increase its effectiveness.
Gumblar’s main infection method has been to compromise legitimate Web sites and then serve malware to unsuspecting visitors to those sites. That attack vector hasn’t changed; it’s simply become more efficient, the X-Force found.
So what’s different this time around? In previous versions of
Gumblar, the malicious scripts and payload were hosted on a remote
server. Iframe code was injected into the compromised website, and it
redirected visitors to their rogue server (gumblar.cn). This time
around, they are placing the malicious scripts and payload directly on
the compromised host, which gives them a decentralized and redundant
attack vector, spread across thousands of legitimate websites around
the world.
The uploaded scripts are placed carefully to match existing file
structures currently on the websites. Heavy obfuscation is used in an
attempt to evade some existing security measures.
Gumblar is using a different set of exploits in this iteration, as well. The malware is relying on a combination of PDF, Adobe Reader and Microsoft Office Web Components exploits to attack the machines of visitors who stumble on the compromised Web sites. Gumblar also still seems to be using its old, reliable method of searching infected machines for any FTP credentials they might have stored and then using those to compromise more Web sites, leading to an endless circle of infections and site compromises.









