 The criminals behind the Gumblar botnet and malware campaign have been adapting their techniques, as attackers are wont to do, in order not only to evade detection but to prevent researchers from downloading and analyzing new versions of the malware.
The criminals behind the Gumblar botnet and malware campaign have been adapting their techniques, as attackers are wont to do, in order not only to evade detection but to prevent researchers from downloading and analyzing new versions of the malware.
A new analysis of the recent activity by Gumblar shows that the current version (or one of the current versions) has a new piece of functionality that checks to see what country a newly infected machine is located in during the initial infection routine. The goal of the bad guys in implementing this check is to prevent Gumblar from infecting any new machines in Japan, where researchers have been quite diligent about finding and taking apart pieces of the Gumblar network.
Gumblar has been infecting servers and PCs for more than a year now,
with a high rate of success. The new change of direction by the
attackers show that they’re not content to stand still.
Gumblar developers have noticed non-stop activity coming from many
Japanese IPs targeting their system. The hard work analysing the threat
and the active online data being harvested from Japan resulted in a
response from the bad guys. Not so long ago we came across a new variant
of the infector script created by the Gumblar developers which
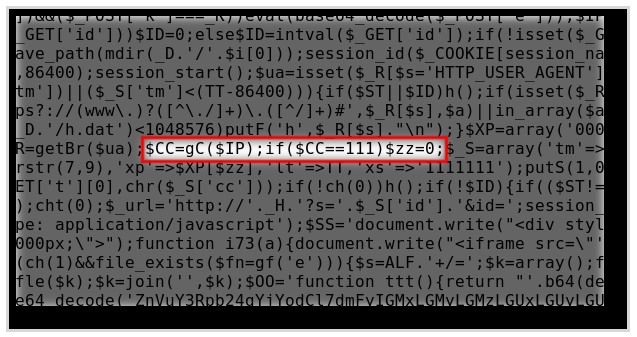
verifies where the remote client is coming from. The script uses a free
IP-to-country database to locate the country of the client. And if the
country turns out to be Japan, the script halts and doesn’t attack.
Below is the part of the code which implements it:
The new research, by Vitaly Kamluk of Kaspersky’s Japanese office, found that the complex Gumblar network now comprises at least 4,460 backdoored servers. That’s a rather large number of servers, any way you slice it, and a fraction of that number would be plenty to put together a pretty large client botnet.
“At this moment no one has information on how many compromised client
machines are in the Gumblar botnet, but we believe it’s more than just
the number of compromised servers, because the number of servers
represents only the count of infected users that have their own websites
and use FTP clients on the infected system,” Kamluk wrote.









