Cybercriminals are hijacking routers and changing Domain Name System (DNS) settings, in order to redirect victims to attacker controlled sites promoting fake coronavirus information apps. If victims download these apps, they are infected with information-stealing Oski malware.
This latest attack shows that hackers are becoming more creative in how they leverage the coronavirus pandemic. And it appears to be working – researchers believe that at least 1,193 victims have been targeted by this cyberattack over just the past couple of days. Reports of the hacks began on March 18, and have since skyrocketed over the past week, with victims from the U.S., Germany and France being mostly targeted.
“We estimate that the number of victims is likely to grow in the coming weeks, especially if attackers have set up other repositories, whether hosted on Bitbucket or other code repository hosting services, as the Coronavirus pandemic remains a ‘hot topic,'” said Liviu Arsene, with Bitdefender, in a post on Wednesday. “Attackers seem to have been probing the internet for vulnerable routers, managing to compromise them – potentially via bruteforcing passwords – and changing their DNS IP settings.”
According to researchers, cybercriminals are targeting routers by brute forcing remote management credentials. Bitdefender said cybercriminals are targeting Linksys routers. A report from Bleeping Computer indicates that D-Link routers are also being compromised.
The attackers will then hijack the router and alter their DNS IP addresses. When a user inputs the website name, DNS services send them to a corresponding IP address serving that domain name – so with this control over DNS settings, attackers can change the DNS IP addresses, and redirect unknowing users to [.]attacker-controlled webpages.
Some of the targeted domains, for which users are redirected, include: “aws.amazon[.]com”, “goo[.]gl”, “bit[.]ly”, “washington[.]edu”, “imageshack[.]us”, “ufl[.]edu”, “disney[.]com”, “cox[.]net”, “xhamster[.]com”, “pubads.g.doubleclick[.]net”, “tidd[.]ly”, “redditblog[.]com”, “fiddler2[.]com” and “winimage[.]com.”
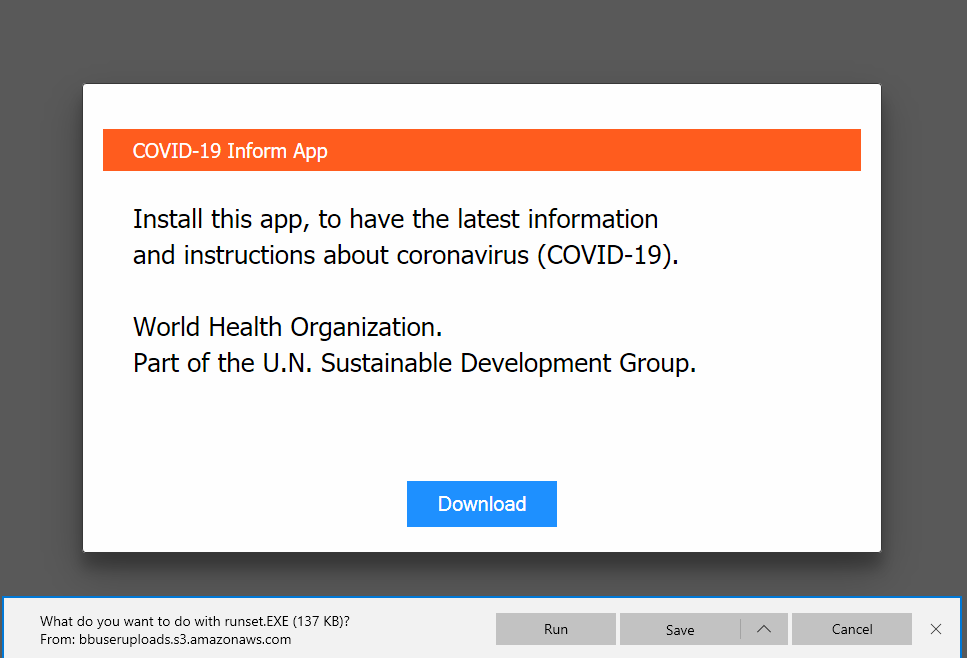
The attackers redirect victims that are trying to reach one of these domains to a specific list of coronavirus-themed webpages. These sites display a message pretending to be from the World Health Organization (WHO), which tells users to install an app offering further coronavirus information (via a “download” button).
“The download button has the ‘href’ tag (hyperlink) set to https://google[.]com/chrome so it seems clean when the victim hovers over the button. But actually an ‘on-click’ event is set that changes the URL to the malicious one, hidden in the URL shortened with TinyURL,” said researchers.
To further cover their tracks, attackers used Bitbucket, a legitimate (and popular) web-based repository hosting service, to store the malware samples. Once victims click on the TinyURL link, the Oski downloader is dropped via a file named “runset.EXE”, “covid19informer.exe”, or “setup_who.exe” (these names are another attempt by hackers to give an air of legitimacy).
 “Oski is a relatively new infostealer that seems to have emerged in late 2019,” said researchers. “Some of the features that it packs revolve around extracting browser credentials and cryptocurrency wallet passwords, and its creators even brag that it can extract credentials stored in SQL databases of various Web browsers and Windows Registry.”
“Oski is a relatively new infostealer that seems to have emerged in late 2019,” said researchers. “Some of the features that it packs revolve around extracting browser credentials and cryptocurrency wallet passwords, and its creators even brag that it can extract credentials stored in SQL databases of various Web browsers and Windows Registry.”
Over the past week, potential victims have been complaining of the hacks on Bleeping Computer’s forums. “So tonight I boot up my computer and just let it chill on my desktop while I am playing my switch. After a few minutes my computer automatically opens a browser window and goes to the microsoft internet redirect like it would when you need to accept terms and conditions to use a network,” said one user on March 18.
Researchers recommend that Linksys and D-Link router users change the router’s control panel access credentials. They also recommend users change their Linksys cloud account credentials, or any remote management account for their routers, to avoid any takeovers via bruteforcing or credential-stuffing attacks.
Attackers continue to leverage coronavirus-themed cyberattacks as panic around the global pandemic continues – including malware attacks, booby-trapped URLs and credential-stuffing scams. APT groups have been eyeing the pandemic as a lure for spreading data exfiltration malware – particularly with more businesses moving to a work from home model in response to the virus.
“While it’s not uncommon for hackers to piggyback global news, such as the pandemic, to deliver phishing emails laced with tainted attachments, this recent development proves they are nothing if not creative in compromising victims,” said Bitdefender researchers.
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.