 Online criminal gangs have begun using special malware that enables them to hide the amount of money that they’re stealing from victims’ online banking accounts, helping them evade detection for longer periods of time and extend the effectiveness of their crime sprees.
Online criminal gangs have begun using special malware that enables them to hide the amount of money that they’re stealing from victims’ online banking accounts, helping them evade detection for longer periods of time and extend the effectiveness of their crime sprees.
Using a banking Trojan called URLZone, in combination with the ubiquitous LuckySploit exploit toolkit, one gang was able to steal approximately 300,000 Euro in the course of a few weeks in August and September, according to a new report published today by Finjan. The hackers were able to draw nearly 100,000 visitors to a fake Web site they set up to infect users’ machines with the banking Trojan.
Once the URLZone malware was on a victim’s PC, it would connect to a remote command and control server to receive instructions on how much money to extract from the victim’s bank account. This particular scheme was aimed at customers of German banks and employed a common structure of money mules transferring money to back-end thieves to hide the identities of the people actually perpetrating the attack.
Money mules are the middlemen in these schemes, often innocent people unaware that they’re involved in a criminal operation. They answer ads for work-from-home positions and end up taking money from victims’ accounts and then transferring it to the criminals in a simple money-laundering operation. It’s a recipe straight from the hacker’s handbook.
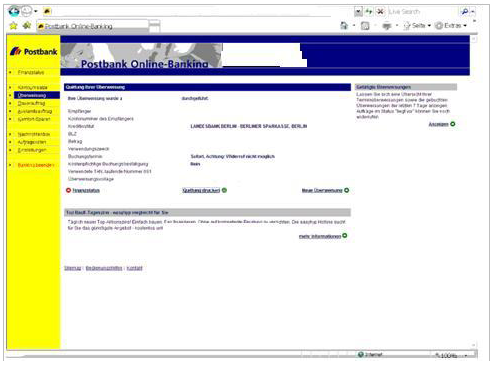
In this case, the URLZone Trojan sat on victims’ machines, logging their online banking credentials (above) and then, when commanded by the C&C server, goes in and steals a specific, random amount of money from the user’s account. The amount is kept low enough that it won’t trigger the bank’s anti-fraud systems.
“To minimize detection by anti-fraud systems, the cybergang used various parameters to define the amount of money it will steal on each transaction. Criteria used by this cybergang included: making sure that the victim‟s balance is positive, ensuring that the amount to be stolen is not too high, setting a random amount on each transaction, making sure that the remaining balance remains positive. They are all aimed at minimizing detection by the anti-fraud systems,” Finjan wrote in the report.
Once the money is transferred to the money mule’s account, the Trojan shows a fake transfer confirmation page to the user, which includes a transfer amount that is much smaller than the amount actually stolen. In one case, Finjan found, the hackers stole more than 8,500 Euro from one account while making it look like the transfer was for about 53 Euro.









