 In a new twist on a couple of old attack techniques, hackers have begun using cross-site scripting to inject malicious iFrames onto some Web sites, redirecting users to malicious sites designed to install unwanted software.
In a new twist on a couple of old attack techniques, hackers have begun using cross-site scripting to inject malicious iFrames onto some Web sites, redirecting users to malicious sites designed to install unwanted software.
The new attack, which leads to the installation of a rogue antivirus program, is a combination of two long-known techniques that have been quite effective in recent years. Cross-site scripting and the use of malicious iFrames to redirect users are two of the more popular attack techniques on the Web and often are used to plant malicious code. The update on these techniques is that attackers now are putting them together in an effort to further hide their intentions and push victims through several hops to a malicious site on the other end.
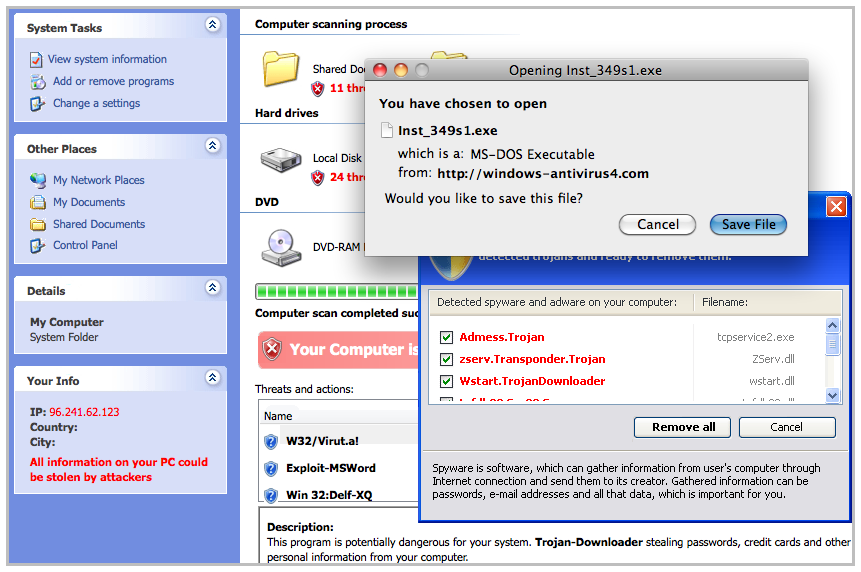
Security vendor Zscaler saw the attacks as they happened.
Today we saw a variety of pages being advertised that have search.htm and other pages vulnerable to cross-site scripting (XSS) being used to inject an iframe
to a malicious webpage redirector. To an unknowing user following such
an advertisement, they would believe that they were just visiting the
intended host site unaware that the iframe was also redirecting them to
malicious content.
In
each of the above examples, the parameter passed to the server’s .htm
or .php file is a string that includes encoded HTML. When the server
processes the parameter, it displays the original parameter (users
usually want to see their query string) and its results. Because the
original parameter is displayed on the page without any sanitization
for this type of encoded HTML, it is possible for this XSS to take
place. The encoded HTML in each case is hexadecimal encoded HTML.
In this case, the attackers were directing victims to a site where they downloaded a rogue AV program, a familiar end-game for this kind of attack. Zscaler has the details of the malicious URLs that the attack is using.









