Milan-based Hacking Team relies on servers in the United States and hosted by American companies to support its clients’ state-sponsored surveillance operations in some of the world’s most repressive regimes.
Hacking Team is an Italian security firm that develops surveillance equipment and sells it to foreign governments that allegedly turn around and use that equipment to spy on various targets. According to a new report from the University of Toronto’s Citizen Lab, in at least 12 cases, U.S.-based data centers contain servers that have some nexus in the infrastructure of foreign espionage.
The specific tool sold by Hacking Team is known as Remote Control System (RCS). According to the report, RCS has the capacity to spy on Skype conversations, email communications, and instant messaging services in addition to siphoning off passwords and local computer files.
Computers with RCS installed on them transmit surveillance data back to their controllers through a series of servers in third-party countries. Known as a proxy chain or circuit, the method – a type of data obfuscation – is commonly used to keep infected users and security experts from being able to accurately examine the sources of traffic. It is not altogether clear whether the proxy servers are established by Hacking Team or its government clients.
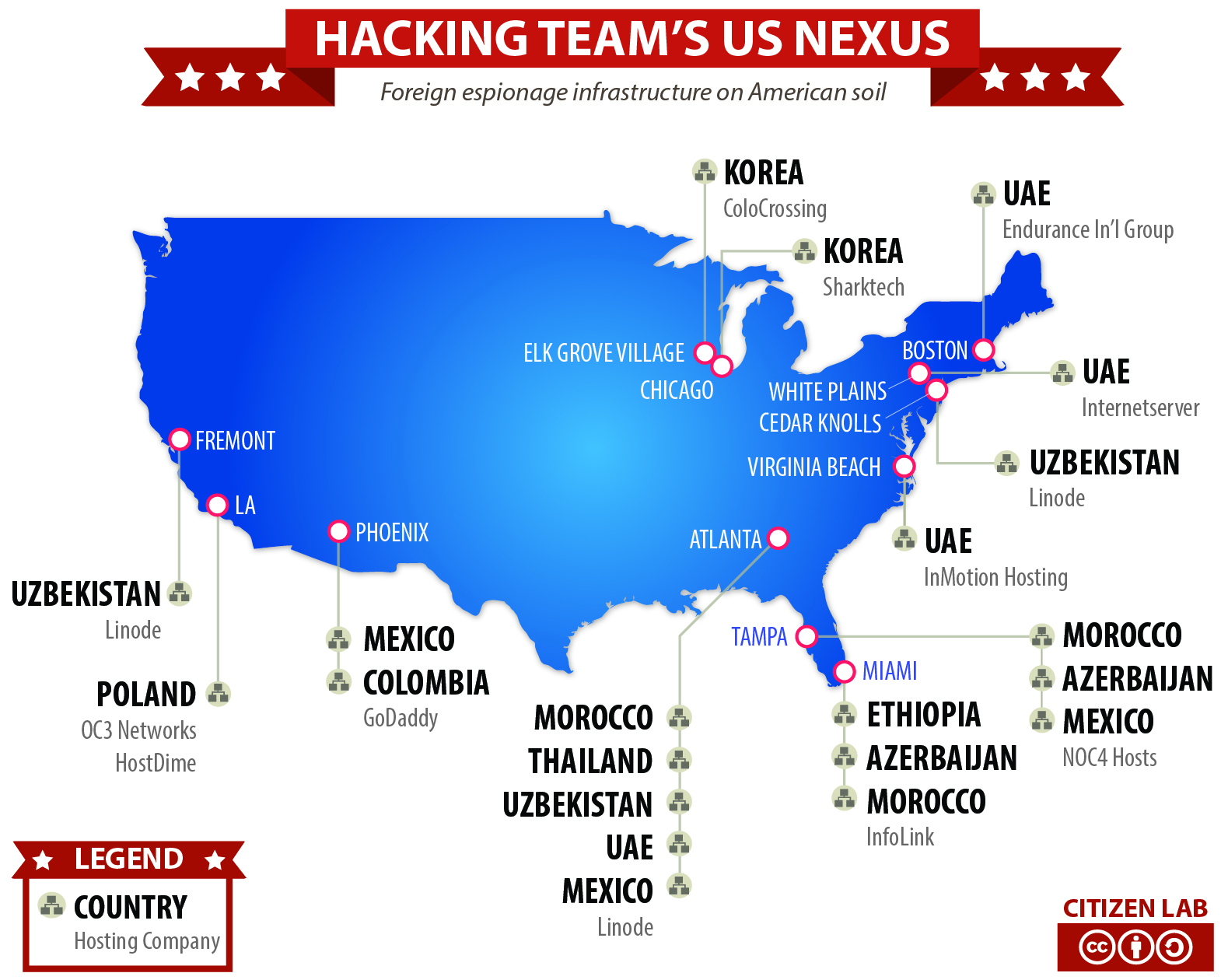
“For example,” the report says, “an infected target may discover that his computer is sending information to a server in Fremont, California, but would not be able to trace the ultimate destination of this information to Uzbekistan.”
In certain cases, the servers facilitating RCS masqueraded as ABC News, a small Oregon-based newspaper, and a New York financial services firm. The purpose of this was – of course – to further shield Hacking teams’ clients from exposure. Citizen Lab believes that these particular companies were chosen because the targets of RCS had some level of familiarity with them.
Obvious legal issues emerge when a foreign government is passing its surveillance traffic through servers in third-party countries. Citizen Lab suggests in its report that Hacking Team or its clients may choose the countries through which RCS traffic passes based on their laws. However, it’s also entirely possible that such actions represent a direct violation of the law in certain countries.
“The passage of RCS traffic through the US is not normal routing incident to benign electronic communications, but the purposeful use of US servers for the surreptitious transmission of wiretapped data to foreign governments. Whether moving such information through US-based communications facilities violates US law, including the Computer Fraud and Abuse Act and the Wiretap Act, deserves immediate attention.”
There is no evidence to suggest that the countries engaged in spying are seeking the approval of the countries in which their infrastructure is party hosted.
Citizen Lab is claiming that the surveillance apparatuses of Azerbaijan, Colombia, Ethiopia, Korea, Mexico, Morocco, Poland, Thailand, Uzbekistan, and the United Arab Emirates are enabled by companies located in a long list of American cities including Boston, Los Angeles, and Chicago. The hosting providers named in the report include GoDaddy, Linode, Sharktech, ColoCrossing, Endurance International Group, Internetserver, InMotion Hosting, NOC4 Hosts, HostDime, and OC3 Networks.
The U.S. contains the largest number of servers supporting RCS command and control communications, though it is by no means the only third-party country through which RCS data is bing routed. After the U.S., which has 114 RCS-related servers, Italy, the United Kingdom, Seychelles, and Japan are the largest hosters of Hacking Team servers.