Increasingly sophisticated attacks that target supply chains, counter-incident response and lateral movement within a network are quickly becoming the new normal in the corporate security threat landscape.
That’s according to Carbon Black’s latest quarterly Global Incident Response Threat Report, which found that 50 percent of today’s attacks leverage “island hopping.” This means that attackers are after not only one target network but also those that are connected via a supply chain.
“At this point, it’s become part and parcel of a cybercrime conspiracy,” said Tom Kellermann, Carbon Black’s chief cybersecurity officer, in the report. “They’re using their victim’s brand against customers and partners of that company. They’re not just, say, invading your house — they’re setting up shop there, so they can invade your neighbors’ houses too.”
As “island hopping” becomes a more persistent threat, the technique has taken on new forms, the firm said. For instance, network-based attacks are often taking the form of targeting an organization’s managed security services provider (MSSP) to attack targets through their connections. Also, in the past 90 days, 17 percent of respondents saw a victim’s website compromised and converted into a watering hole to ensnare a victim’s customers and partners.
Kellermann noted, “It’s the greatest way to hijack a brand, and, as such, organizations need to make this a brand protection issue. CMOs have to have their own cybersecurity strategy in place as it relates to their digital marketing footprint.”
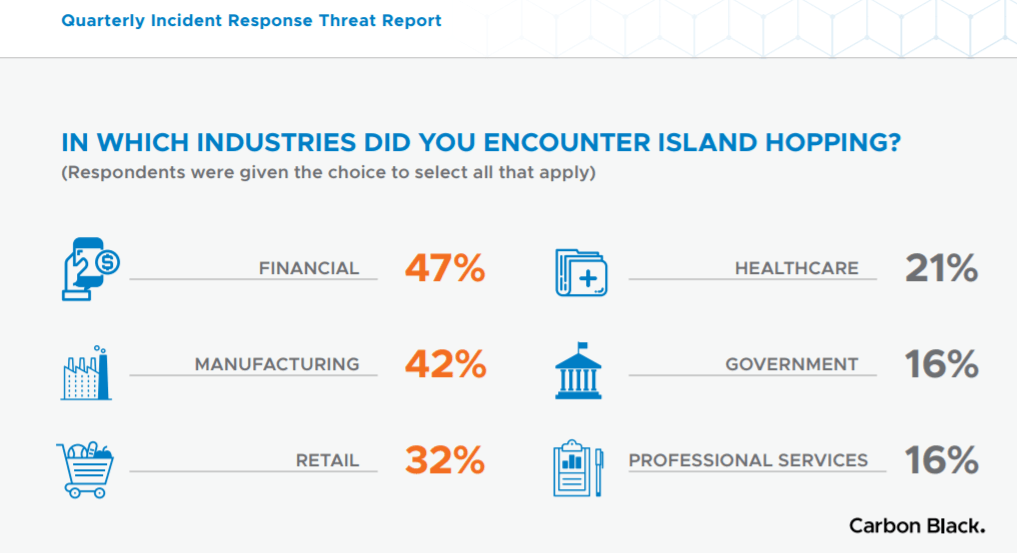
Reverse business email compromise (BEC) is also becoming more common, primarily in the financial sector. Here, attackers take over the mail server of the victim company and leverage fileless malware attacks from there to those who trust it.
Meanwhile, more than half of survey respondents (56 percent) encountered instances of counter-incident response (IR) in the past 90 days, according to the report. A full 87 percent have seen this take the form of destruction of logs, while 70 percent witnessed various evasion tactics.
Again, financial and manufacturing are top targets, with 36 percent of IR professionals seeing these instances within financial organizations and 27 percent in manufacturing.
“An attacker is going to turn off antivirus, firewalls, anything that’s going to send a trigger upstairs, because the longer they have to achieve their goal — whether it’s lateral movement, ‘island hopping’ further up the supply chain or data collection — the better chance they’ll have for success,” said Thomas Brittain, who leads Carbon Black’s Global IR Partner Program.
Speaking of which, Carbon Black also found that 70 percent of all attacks now involve attempts at lateral movement, as attackers take advantage of new vulnerabilities and native operating system tools to move around a network.
“Troublingly, even if you kick an attacker out of a system these days, the attacker will often have methods for lurking around and eventually getting back in undetected,” according to the report. “For instance, 40 percent of respondents encountered instances of secondary command-and-control server (C2) used on a sleep cycle. What’s more, the increased use of steganography — essentially, hiding data in other content types like images, videos, and network traffic — means that these attackers may be hanging out in a network without IR teams even knowing they’re there.”
Unfortunately, the report also found that nearly a third (31 percent) of targeted victims now experience destructive attacks — an alarming byproduct of attackers gaining better and more prolonged access to targets’ environments, the report noted.
And finally, the research found that the financial and healthcare industries remain most vulnerable to attacks, but the threat to manufacturing companies has grown significantly. In the past 90 days, nearly 70 percent of all respondents saw attacks on the financial industry, followed by healthcare (61 percent) and manufacturing (59 percent, up from 41 percent last quarter).
“Attackers are fighting back,” Kellermann said. “They have no desire to leave the environment. And they don’t just want to rob you and those along your supply chain. In the parlance of the dark web, attackers these days want to ‘own’ your entire system.”