 IT administrators know there’s nothing more frustrating than losing administrative access to your network equipment. But Allied Telesis, a Japan-based maker of switches, routers and other networking devices, has a fix: guaranteed backdoors for every product.
IT administrators know there’s nothing more frustrating than losing administrative access to your network equipment. But Allied Telesis, a Japan-based maker of switches, routers and other networking devices, has a fix: guaranteed backdoors for every product.
That revelation comes after a support page, titled “Backdoor Password for Allied Telesis Devices” turned up on Google. The page, labeled ***INTERNAL ONLY*** was written to answer customer questions like “‘How do I obtain a backdoor password for my Allied Telesis device?'” and includes instructions on accessing a “built in Backdoor function” on any Allied Telesis device.
Backdoor administrative accounts and functions are a dirty secret of the hardware industry. Traditionally, they have been written into the device operating system to give administrators or support staff emergency access to devices that are malfunctioning or that they have been locked out of. However, default back doors have also been a boon for malicious hackers, who can often discover how to access the backdoor functions, as in this case, from support manuals and forums.
A hard coded back door in industrial control systems from Siemens played a prominent role in the spread of the Stuxnet worm. More recently, Hewlett Packard acknowledged a hard coded back door account in some of its storage area networking (SAN) products. Such features are attractive to malicious hackers because they require little time or technical skill to access, and are less likely than other types of external attacks to arouse attention from the device’s proper owner or be detected by security and monitoring tools.
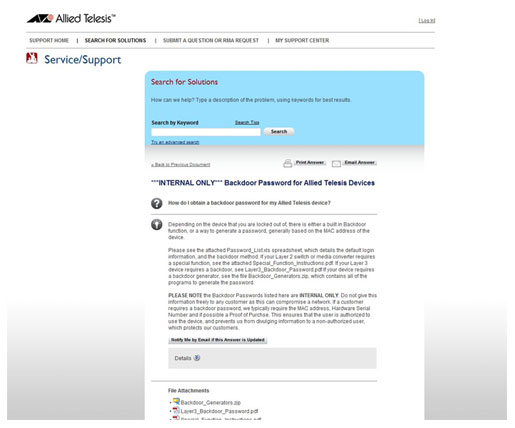 In the case of Allied Telesis, which makes a wide range of networking equipment, including wired and wireless switches and routers, media converters and network interface cards, backdoors are apparently a common feature of many products.
In the case of Allied Telesis, which makes a wide range of networking equipment, including wired and wireless switches and routers, media converters and network interface cards, backdoors are apparently a common feature of many products.
“Depending on the device that you are locked out of, there is either a built in Backdoor function, or a way to generate a password, generally based on the MAC address of the device,” the support note reads. It goes on to provide links to a Microsoft Excel spreadsheet, Password_List.xls,” which “details the default login information and the backdoor method,” as well as written instructions for accessing backdoor functions on Layer 2 switches or Layer 3 devices by Allied. Those documents were not accessible directly from the support page.
It is unclear whether the page in question was intended for customers or for Allied Telesis staff only. Contacted by Threatpost, Chad Brooks, a level 1 technical support engineer said the page was part of the company’s support Web site and intended for customers to use. However, the text of the support note suggests otherwise.
“PLEASE NOTE the Backdoor Passwords listed here are INTERNAL ONLY. Do not give this information freely to any customer as this can compromise a network,” it reads.
Allied support staff are instructed to confirm the customer’s identity before dispensing backdoor passwords. Customers must supply a MAC address, Hardware Serial Number and, if possible, proof of purchase, the support note reads.
An Allied Telesis support manager was unable to determine whether the backdoor instructions were intended for public consumption, or whether the page inadvertently ended up accessible from the public Internet.









