The HawkEye malware kit and information-stealer has been spotted in a newfound slew of campaigns after a recent ownership change.
While the keylogger has been in continuous development since 2013, in December a thread on a hacking site noted an ownership change, after which posts on hacking forums began to appear, selling new versions of the kit. “HawkEye Reborn v9” sports new anti-detection features and other changes, researchers said.
“Recent changes in both the ownership and development efforts of the HawkEye Reborn keylogger/stealer demonstrate that this is a threat that will continue to experience ongoing development and improvement moving forward,” said Edmund Brumaghin and Holger Unterbrink, researchers with Cisco Talos, in a Monday analysis. “HawkEye has been active across the threat landscape for a long time, and will likely continue to be leveraged in the future as long as the developer of this kit can monetize their efforts.”
This latest version of HawkEye is sold through a licensing model (meaning that purchasers gain access to the software and future updates based on a varying tiered pricing model), and is being marketed on hacking sites as an “advanced monitoring solution.”
“The current developer of the HawkEye Reborn keylogger/stealer is continuously adding support for different applications and software platforms to facilitate the theft of sensitive information and account credentials,” researchers told Threatpost. “The malware has recently undergone changes to the way in which it is obfuscated and additional anti-analysis techniques have been implemented as well.”
HawkEye Reborn v9 also now features a terms-of-service agreement: While the seller says that the keylogger should only be used on systems with permission, the agreement also explicitly forbids scanning of HawkEye Reborn v9 executables using antivirus software.
In a further attempt “to minimize the likelihood that anti-malware solutions will detect HawkEye Reborn binaries,” researchers said that the keylogger also now comes with several anti-analysis features, such as an anti-debugging thread process and the ability to disable certain antivirus-related programs.
In tandem with the ownership change of HawkEye, researchers observed a slew of campaigns from late 2018 into 2019 that involve this most recent version of the malware.
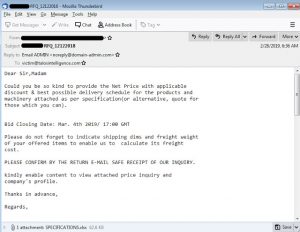
The malicious email campaigns include messages that appear to be requesting invoices, bills of materials, order confirmations and other things related to normal corporate functions. However, the emails actually arrive with malicious Microsoft Excel attachments (which exploit an arbitrary code execution bug in Microsoft Office, CVE-2017-11882), as well as RTF (Rich Text Format) or Doc files.
Once a victim clicks on the attachment, the email-senders have intentionally made the contents of the documents look blurry — and the user is prompted to enable editing to have a clearer view of the contents. After they do that, the injection process begins, with the HawkEye keylogger being downloaded.
The malware then snatches up sensitive information, such as the system information, passwords from common web browsers, clipboard contents, desktop screenshots, webcam pictures and account credentials.
Threatpost has reached out to Cisco Talos researchers for further details about the campaigns, including how many there have been, and what victims have been targeted.
Moving forward, researchers warn that HawkEye will continue to evolve. But more significantly, the malware kit represents yet another offering that reduces the barrier for entry for bad actors, who may not necessarily have the programming skills to carry out sophisticated hacks.
“In many cases, the adversaries leveraging these tools do not need to possess programming skills or in-depth computer science expertise, as they are now being provided as commercial offerings across the cybercriminal underground,” researchers said.
Don’t miss our free Threatpost webinar, “Data Security in the Cloud,” on April 24 at 2 p.m. ET.
A panel of experts will join Threatpost senior editor Tara Seals to discuss how to lock down data when the traditional network perimeter is no longer in place. They will discuss how the adoption of cloud services presents new security challenges, including ideas and best practices for locking down this new architecture; whether managed or in-house security is the way to go; and ancillary dimensions, like SD-WAN and IaaS.