Almost 200,000 servers and devices are still vulnerable to Heartbleed, the OpenSSL flaw patched nearly three years ago. The numbers come from search engine Shodan, which released data showing U.S. servers hosted on Amazon AWS are disproportionately vulnerable to the flaw.
“There’s a lot to be worried about with this data, but also a lot that’s unsurprising,” said Tim Jarrett senior director of security, Veracode.
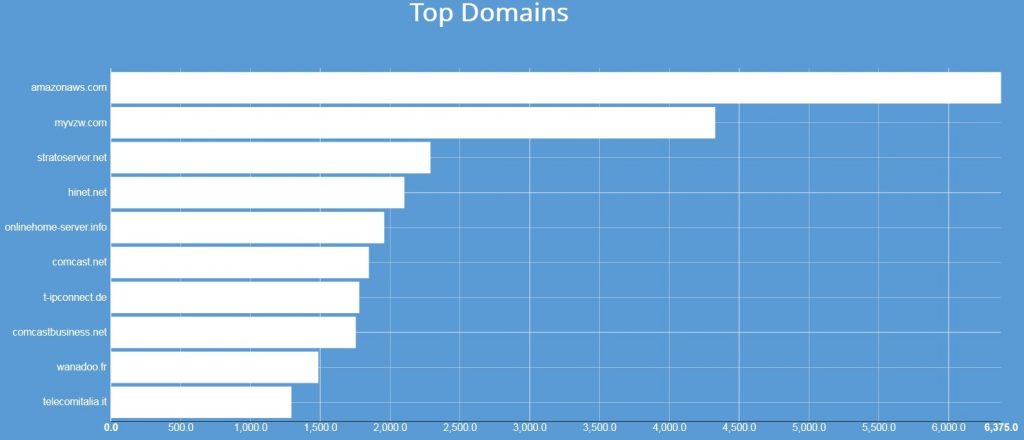
The Shodan analysis released over the weekend is part of the search engine’s Heartbleed Report (2017-01). It paints a gloomy picture when it comes to Heartbleed mitigation. The report indicates that almost 52,000 Apache HTTPD servers remain vulnerable and exposed to the internet, in particular versions 2.2.22 and 2.2.15. Amazon Web Services hosts the highest number of vulnerable devices (6,380), followed by Verizon Wireless (4,330) and German-based ISP Cronon AG (2,290).
“The initial media blizzard for Heartbleed helped secure hundreds of thousands of devices (from 600,000 down to 200,000) but the subsequent follow-up has been lackluster as the problem keeps lingering,” said John Matherly, Shodan founder. He points out that the vast majority of affected services actually support TLSv1.2. “This means they support good encryption, unfortunately their dependencies are old,” he said.
Heartbleed was an internet-wide bug that in 2014 affected millions of Linux, UNIX and Apple machines running vulnerable versions of the OpenSSL library. The Heartbleed vulnerability can result in the revelation of 64 KB of memory to any client or server that is connected. In April of 2014, fixes for versions of OpenSSL were quickly pushed out.
“Most Heartbleed vulnerabilities are reported in the U.S. This makes sense given the prevalence of web applications hosted in Amazon AWS and Verizon as well as other US-based ISPs,” Jarrett said.
He said part of the issue is that it’s easy to create new servers in AWS that don’t enforce the same type of safety provisions as they once required.
“What used to require a sysadmin and a capital expenditure can now be done with a few lines of code. And we know that both real and virtual servers are easy to forget about, particularly when created outside of normal IT processes. So it’s unsurprising that some of these ‘forgotten servers’ are unpatched and dangerous,” Jarrett said.
The Shodan data shows the overwhelming impacted services are HTTPS with 148,420 vulnerable servers followed by HTTPS (port 8443) with 23,600 servers and then Webmin, the sys admin interface for Unix (5,970).