Built to provision, deprovision, audit, and manage user access rights to data, files, and other systems, SolarWinds® Access Rights Manager (ARM) is designed to help security admins and IT pros protect their companies from potential risks like data loss and breaches. Visualize who has access to what and when they accessed, by analyzing authorizations and access permission of users. ARM enables you to generate customized reports to help demonstrate most regulatory compliance requirements with just a few clicks. Using role-specific templates, provision and deprovision users to help assure conformity of access privilege delegation that aligns with your organization’s security policies. Start today with a free 30-day trial of ARM.
In summary, with ARM you can:
- Monitor and audit changes to Active Directory
- Alert on unauthorized access or changes to Windows file servers
- Analyze and administer Exchange access rights
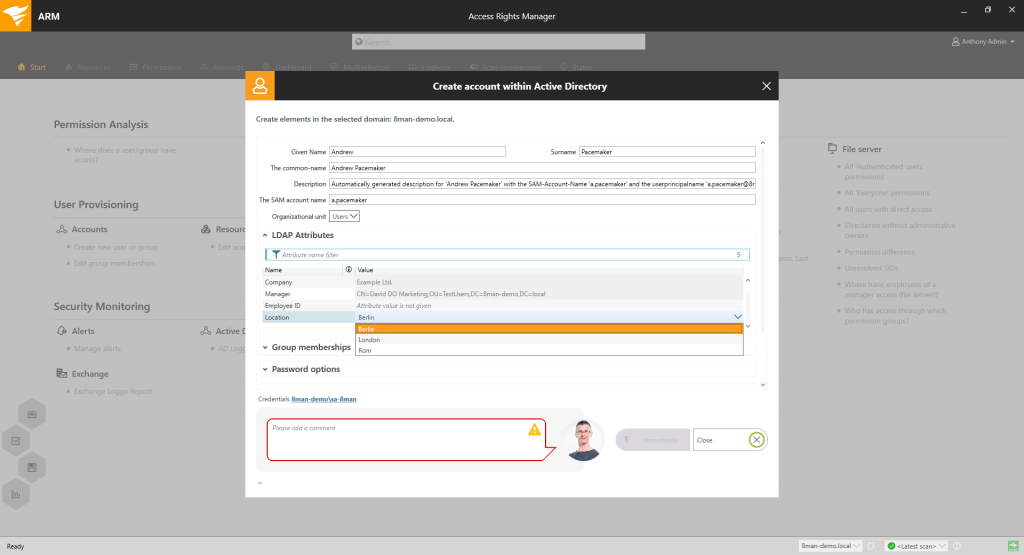
- Create, modify, activate, deactivate, and delete user access to services and files
- See group memberships from Active Directory and access rights to file servers
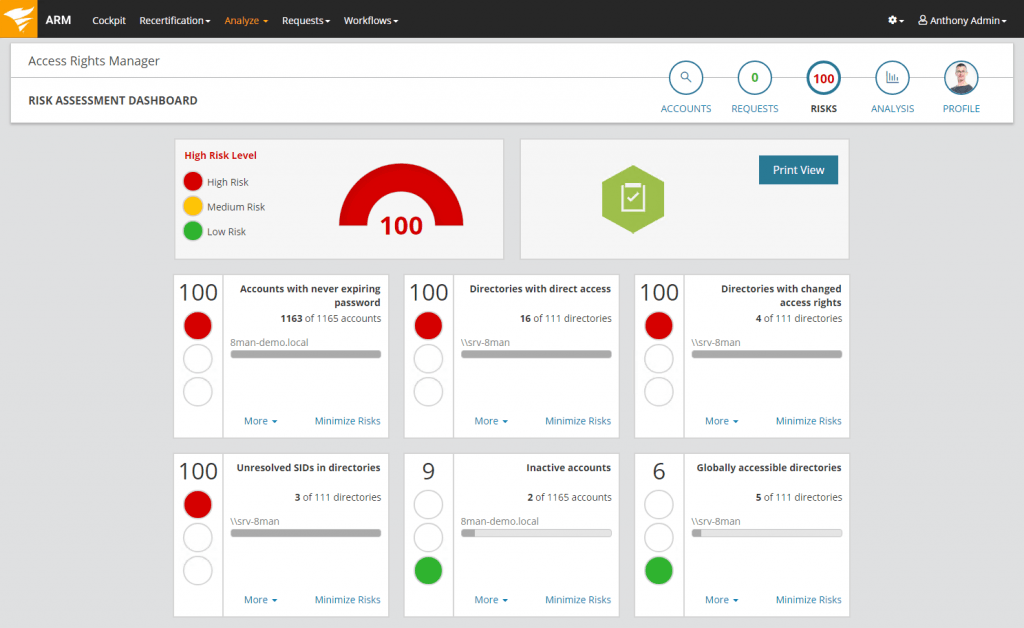
(Figure 1: The risk assessment dashboard shows your top risk factors with the highest impact on security.)
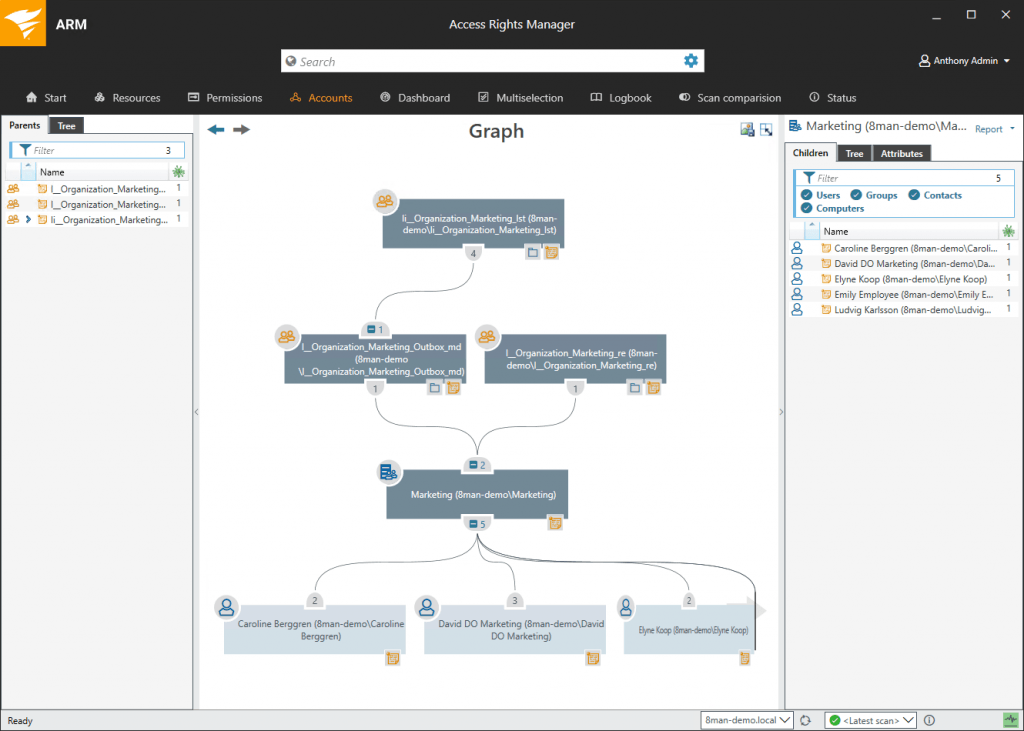
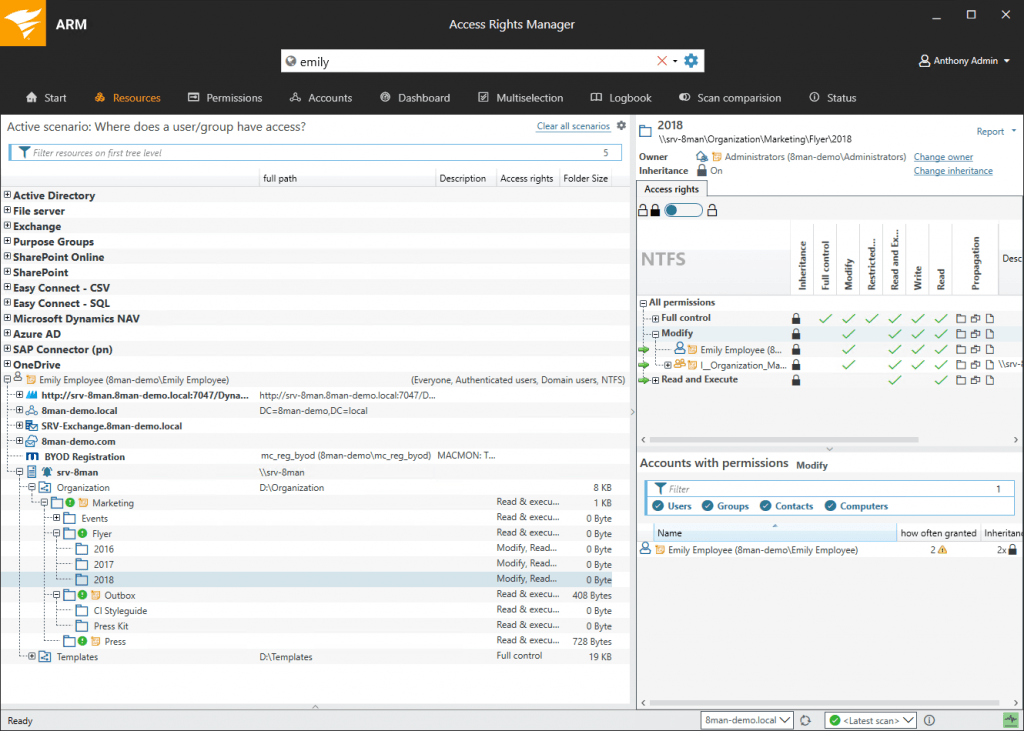
(Figure 2: Access Rights Manager (ARM) visualizes who can access a given resource at your organization. In a central view, you can see the group memberships from Active Directory® and the access rights given.)
See what changes have been made by monitoring, analyzing and auditing Active Directory. ARM is built to increase efficiency while reducing risks in your environment. Whether you are an MSP managing Active Directory infrastructure on behalf of a client or managing your own company’s user accounts, relying on manual tools for user management can potentially expose organizations to risk and error. Through the automation of creating, modifying, deleting or disabling accounts, ARM scales to meet the demands of your business while keeping track of an audit trail of account activity and access.
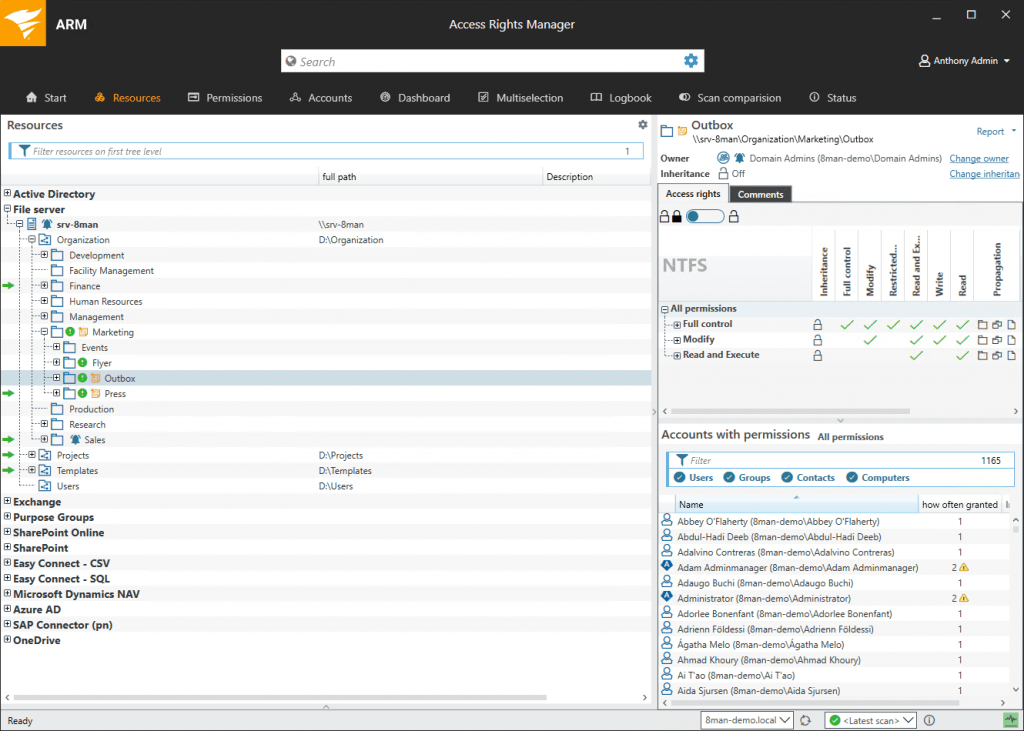
(Figure 3: Help protect against data leaks and unauthorized changes through the visualization of permissions on file servers.)
When dealing with insider threats it can be challenging to distinguish between malicious activity and innocent error. Quick response is essential to help secure data and resume regular operation. Role specific templates within ARM allow for safe account creation and streamlined deprovisioning processes in response to an insider threat. ARM’s authentication management system is designed to deliver effective and secure cybersecurity solutions.
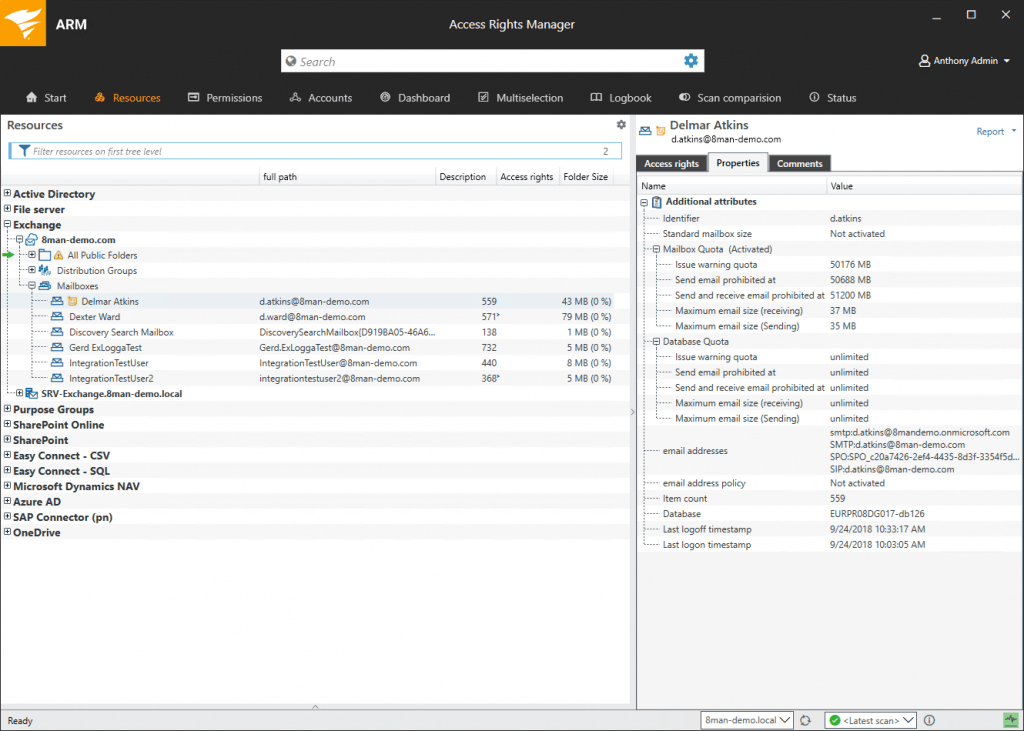
(Figure 4: Simplify monitoring and auditing in Exchange and help prevent data breaches with Access Rights Manager. Tracking changes to mailboxes, calendars and public folders can help improve compliance and detect unauthorized changes.)
(Figure 5: Set up and manage new user accounts typically in seconds with standardized role-specific templates that provide access to file servers and Exchange.)
(Figure 6: Help protect from internal security threats by analyzing user access to services and file servers with visibility into group memberships from Active Directory and file servers. )
Learn how Access Rights Manager can help improve IT and data security in your environment today with a free 30-day trial. Download Now!