For years enterprises have been trying to control peer-to-peer (P2P) technologies inside their networks, and for good reason. The efficiency with which P2P technology move large files have made P2P networks key enablers of the Internet grey market by acting as the distribution mechanism of choice for pirated movies, music or applications. Aside from P2P being a source for pirated content, they are also a significant enabler of malware as both an infection vector and a command-and-control (C2) channel. These security risks have made controlling P2P traffic a priority for many security teams.
One approach to controlling the grey market usage of P2P would be to provide an alternative means for moving large files such as web-based file transfer applications YouSendIt!, Dropbox or Box.net. These are just a few of many “digital locker” alternatives and their use is becoming so common that one might assume that P2P is on the decline.
Interestingly, data from Palo Alto Networks Application Usage and Risk Report issued today shows that the opposite is true: The use of P2P is surging in the enterprise and web-based file transfer is staying relatively flat. In terms of bandwidth consumed, P2P saw a seven-fold increase compared to the previous report (from 2% to 14%), and it continues to dwarf web-based file transfer applications. In fact, BitTorrent alone accounted for 58 times more bandwidth than Dropbox, RapidShare, Box.net and the other 68 variants combined. What makes these reports particularly interesting is they are based on analysis of real traffic from enterprise networks (petabytes of traffic from more than 2,000 different organizations in this version of the report). So the obvious question is what makes P2P so tenacious in the enterprise despite alternatives and efforts to control it?
Evasiveness and Resilience
The simplest answer is that P2P thrives because it can. P2P is notoriously difficult to control because it is inherently dynamic. P2P is not bound to a single default port, and can easily adapt to the network to find available ports as the need arises. This is made particularly clear in the Palo Alto Networks report, which breaks out the behavior of all file transfer applications based on port behavior. In this case 88% of the filesharing/file transfer bandwidth was consumed by applications that port-hopped between multiple ports, compared to only 5% by applications that used port 80 or 443. Both web-based and P2P file transfer applications were seen in abundance, but the heavy lifting in terms of bandwidth was being done by dynamic P2P apps.
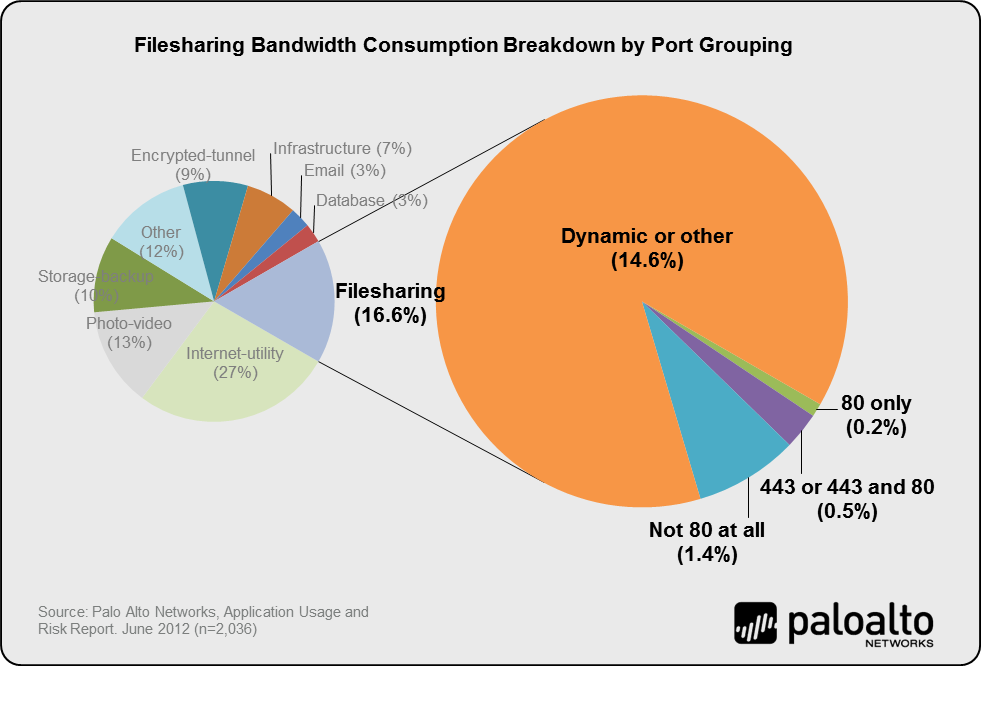
The importance of controlling P2P is not limited to simply preserving bandwidth and warding against copyright infringement. P2P networks are inherently distributed and designed to easily survive the loss of any (or many) endpoints. This trait has made P2P increasingly attractive as a C2 channel for botnets. Instead of relying on command-and-control servers that can be taken down, a peer-to-peer based control structure allows a botnet to survive and provide coordination simply by using the end-points of the botnet themselves. Botnets that use P2P for command and control – from Storm and Kelihos to TDL-4 and even new forms of Zeus – have proven to be notoriously difficult to take down. The Application Usage and Risk Report further indicates that P2P protocols were repeatedly being used as the starting point for new botnet protocols. In particular, polymorphic malware was observed building on top of QVOD (a P2P streaming protocol) to build custom malware communications channels. If nothing else, this underscores the risk of allowing P2P traffic to run unchecked in the enterprise in that it provides an ideal cover for malware to hide in the network.
The increasing use of P2P as a malware vector and C2 channel re-emphasizes two key facts that are sometimes overlooked. First, and most obvious, is that web-connected applications are a common malware vector. The second, yet less obvious, fact is that the applications used as a malware vector are not always the most common or most visible. P2P has in recent years, been quietly maintaining a steady existence, hiding in the shadows of social media and digital lockers – yet the risks are as great, or greater, comparatively.
Browse the report findings using the interactive application at www.paloaltonetworks.com/aur.
Wade Williamson is a Senior Security Analyst at Palo Alto Networks. He has extensive industry experience in intrusion prevention, secure mobility, and both wired and wireless networking. Prior to joining Palo Alto Networks, he led the product management team at AirMagnet, Inc. He has been a steady and active researcher of new threats and techniques used to compromise enterprise networks and mobile end-users. He also brings well-rounded experience from silicon-valley visionaries Netscape and Sun Microsystems.










