Cisco Systems has patched two high-severity vulnerabilities in its popular Webex video conferencing platform, which if exploited could allow an attacker to execute code on affected systems.
Two multimedia players tied to the Webex platform are impacted. First is the Cisco Webex Network Recording Player, used to play back Advanced Recording Format (ARF) files on the Windows operating system. ARF files contain data from a recorded online meeting, such as video data and a list of attendees. Cisco Webex Player is also affected, which used to play back Webex Recording Format (WRF) files on the Windows OS. WRF files contain audio and video recordings, typically used for demonstrations, training and conferencing.
The vulnerabilities (CVE-2020-3127 and CVE-2020-3128) are both 7.8 out of 10.0 on the CVSS scale, making them high-severity. They stem from an insufficient validation of non-detailed, “certain elements” within a Webex recording that is stored in either ARF or WRF, said Cisco.
While Cisco did not detail the technicalities of the vulnerabilities, it said that “an attacker could exploit these vulnerabilities by sending a malicious ARF or WRF file to a user through a link or email attachment and persuading the user to open the file on the local system,” according to Cisco in a Wednesday advisory. “A successful exploit could allow the attacker to execute arbitrary code on the affected system with the privileges of the targeted user.”
Brian Gorenc, director of vulnerability research and head of Trend Micro’s ZDI program, told Threatpost that the flaw allows remote attackers to execute arbitrary code – but it does require user interaction.
“User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file,” he told Threatpost via email. “Specifically, this bug exists is in atpdmod.dll module and the vulnerable code is reachable using a crafted ARF File. This program fails to initialize a pointer and later writes data to this pointer. In the worst case, this could lead to remote code execution in the context of the current process.”
Different versions of Webex Network Recording Player and Webex Player are affected by the flaws, based on the platforms they are being managed on. The players are available from Cisco Webex Meetings and Cisco Webex Meetings Online (which is when conferencing systems are managed by Cisco Webex), and Cisco Webex Meetings Server (where customers host and manage conferencing solutions in their own private clouds).
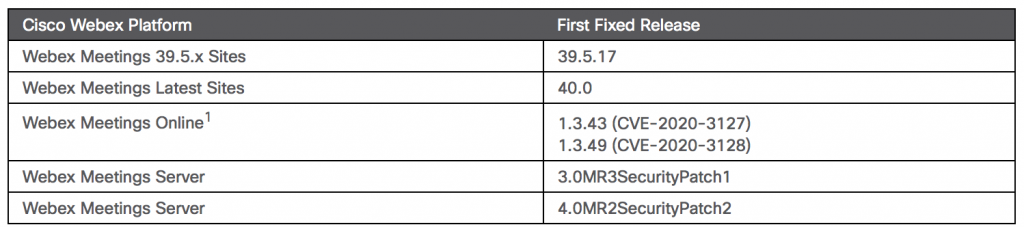
For Cisco Webex Meetings, affected versions for both products include releases earlier than WBS 39.5.17 or WBS 39.11.0. For Webex Meetings Online, affected versions for both products include releases earlier than 1.3.49. And, for Cisco Webex Meetings Server, versions of Webex Network Recording Player earlier 3.0MR3SecurityPatch1 and 4.0MR2SecurityPatch2 are affected.
To determine which release of Cisco Webex Network Recording Player or Cisco Webex Player is installed on a system, users can open the player and choose Help > About. The fixed releases can be found below.
Cisco said it’s not aware of the flaws being exploited by attackers at this time. Francis Provencher (PRL) working with Trend Micro Zero Day Initiative, and Kexu Wang of Fortinet’s FortiGuard Labs were credited with discovering the flaws (Threatpost has reached out to both researchers for further details of the vulnerability and will update this post accordingly).
Webex has been haunted by other vulnerabilities since the start of the year. In January, Cisco fixed a high-severity vulnerability in Webex that could have let strangers barge in on password-protected meetings sans authentication. A separate high-severity flaw also disclosed by Cisco in January could enable a remote attacker to execute commands in Webex.
Beyond Webex, Cisco on Wednesday released patches addressing flaws tied to a total of 13 CVEs. Other high-severity flaws include a vulnerability in the SSL implementation of the Cisco Intelligent Proximity solution, which is a tool allowing users to see and control content in a meeting room from their own devices. The certificate validation vulnerability (CVE-2020-3155) could allow an unauthenticated, remote attacker to view or alter information shared on Cisco Webex video devices and Cisco collaboration endpoints.
And, a high-severity cross-site request forgery (CSRF) flaw exists in Cisco Prime Network Registrar, software that is comprised of components for various services, including Domain Name System (DNS) services and Dynamic Host Configuration Protocol services. The flaw (CVE-2020-3148) in the online interface of the registrar could allow an unauthenticated, remote attacker to conduct a CSRF attack on an affected systems.
Interested in security for the Internet of Things and how 5G will change the threat landscape? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.