Gartner’s CARTA (Continuous Adaptive Risk and Trust Assessment), which sets out their vision for security, is increasingly being adopted by several enterprises. Recently Gartner also called out CARTA strategic approach in the top 10 security projects for 2019. CARTA, being a strategic approach, covers a whole gamut of areas and multiple security products from endpoints, devices, IoT, procurement, etc. contribute to different parts of CARTA.
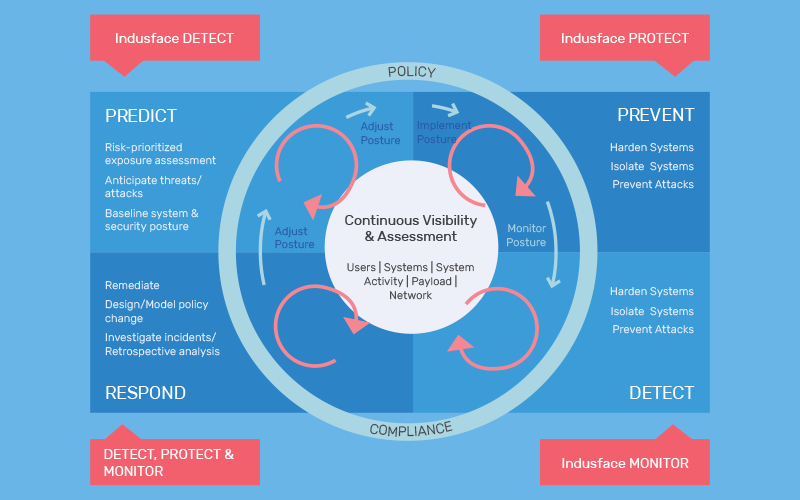
Very high-level CARTA primer
A couple of years back, Gartner introduced CARTA (Continuous Adaptive Risk and Trust Assessment) – a strategic approach to information security. With workloads increasingly moving to the cloud, access is made from multiple devices and locations outside office boundaries, one-time gates are no longer sufficient and must change to be adaptive and context-aware.
The CARTA approach suggests that both Risk (threat/attack) and Trust (access by entities) should not be made as a one-time gate of good/ bad, allow/disallow but instead, be continuously evaluated and actions taken in a dynamic, adaptive manner based on various factors like device, risk, asset value, incidents, behavior, analysis, etc. This strategy is applicable to Ops (production), Build (development), and Planning (business owners).
In this document, we talk about CARTA as it applies to Web Application Security and Indusface, applicable more to threat assessment and mitigation and not as much to trust. For this aspect, CARTA sets out a cycle of Predict – Prevent – Detect – Respond which resonates with the Detect-Protect-Monitor approach that Indusface provides.
CARTA: Indusface terminology
Anticipate Threats & Exposure. (Detect)
Indusface Web Application Scanner automatically scans applications for vulnerabilities. Customers that need deeper business logic scanning will use our premium pen testing service.
Prevent Attacks (Protect)
Indusface WAF implements the Protect part and prevents attacks. The highly tuned advanced rule set is in block mode right from the start. Premium (custom) rules will be written and applied depending on specific customer scenarios.
Incident/breach (Protect, Monitor)
Indusface tools and teams will analyze and Monitor events to detect indicators of attempted attack and take appropriate action including automated response, alerting, and getting security experts involved.
Remediate, analyze incidents (Detect, Protect, Monitor)
Raw and analyzed logs are stored so post facto analysis can be done by internal and customer teams. Internally, detection, prevention rules are adjusted, customized and new targeted rules written as needed in response to incidents.
CARTA Results from the Gartner Adaptive Security Architecture
How Indusface uses CARTA in its product ethos?
Integrated WAS and WAF
Vulnerabilities found by scanning have additional information associated with them that explains whether there is protection out of the box, additional rules must be applied, or a premium custom rule should be requested. Known vulnerabilities are tracked closely though they are mitigated by WAF – an attempt to attack is always interesting. Similarly, areas of the web application that are accessed in the real world but not yet scanned will be prioritized for scanning the next time a scan is performed.
Data pipeline
Without data there is no analysis and timely data is required for a quick response. Indusface has built a high volume, high-speed data pipeline so that security and non-security events rapidly get to the backend for analysis. This augments the longer-term storage of raw data that can be used for post facto analysis by customers if needed.
Analytics, AI, ML, automation
“Use analytics, AI, automation, and orchestration to speed the time to detect and respond — and to scale our limited resources”
This has always been our philosophy. We use our years of experience with numerous web applications to drive what to automate like manual pen test cases -> automated scanning and automated rule generation. With the data pipeline, now we are adding more analytics and AI so our teams can focus on and prioritize security issues and incidents. This is the only scalable way to handle the sheer volume of data that is generated/collected.
Adaptive protection
Allow more decisions than a simple block / allow e.g. CAPTCHA, throttle, alert. These decisions are not static and depend on the behavior, context, threat assessment, and vulnerability scans. This also means that IP as an identity is not sufficient, a more fine-grained knowledge of the session is needed. Sometimes this can be done by looking at the traffic while for others we need to integrate with IAM providers.
Play well with others
Along with the business cases like CDN integration, let us Encrypt certificates, on a security-specific basis, we are implementing API driven integration that can be used for things like getting events from Indusface (e.g. SIEM), adjusting security posture, richer session identity, etc.
What about the recent paper Top 10 Security Projects for 2019?
Firstly, in Table 1 “Foundational Security Projects and Capabilities”: Server Protection Agents/ Security Infrastructure, WAF is one of the solutions for perimeter security controls. Of the specific 10 security projects that Gartner mentions, there are two that directly apply
- CARTA-Inspired Vulnerability Management
WAF is specifically called out in the project advice as mitigating technology.
Project Advice — Look at current threat and vulnerability management products and processes to accomplish this. Also, consider mitigating technologies such as intrusion detection and prevention systems (IPDS) and web application firewalls (WAFs) that could be actively protecting for unpatched vulnerabilities.
- Detection and Response
Indusface Detect-Protect-Monitor and all the features relating to CARTA discussed above make Indusface an ideal partner to implement CARTA strategies for your web application security.
If you have taken a managed security services approach, consider a detection and response project that can feed valuable information into a managed detection and response (MDR) provider and/or a managed security service provider (MSSP).
CARTA Operational Checklist for CISO and Security Practitioners
From an operational standpoint, the foundation of CARTA starts with an assessment, and then building the zero-trust principles on top of that with an adaptive security model:
From an operational Standpoint, the foundation of CARTA starts with an assessment and then building the zero-trust principles on top of that with an adaptive security model
- Assessment – Ensure that you have a cadence in place to regularly assess your web application. An automated solution for doing it frequently (even daily) and a deeper assessment to include business logic checks and manual penetration testing whenever there are major changes in the applications.
- Trust – The assessment will put a spotlight on the current risks on your applications and based on that have adaptive trust policies to mitigate those risks and learn from those risks and apply dynamic changes to your web application firewall rules. Example- A medium risk of -Client-side validation override can have a trust policy in WAF as a virtual patch and can be a trigger to dynamically block the user or throw more challenges as the user has bypassed the client-side validation and is not normal behavior. This ensures that trust policies are applying the concept of Zero trust and evaluate every request-response applying the principles of zero trust before fulfilling the request.
- Risk- Have a clear understanding of the current risk score after the assessment and trust policies to at least be able to understand the current risk for your applications
- Adaptive- Adapt the policies, action items based on the current risks
- Continuous- Do all the above on a continuous basis
While Indusface has been doing much of this for years, using the CARTA framework to focus our approach helps us and our customers achieve Adaptive Attack Prevention.