 The infection routines being used by some scareware and rogue AV gangs are much more comprehensive and far-reaching than many current analyses have shown, experts say, including some attacks that not only place a malicious script on a compromised server, but infect every single legitimate script on the server, as well.
The infection routines being used by some scareware and rogue AV gangs are much more comprehensive and far-reaching than many current analyses have shown, experts say, including some attacks that not only place a malicious script on a compromised server, but infect every single legitimate script on the server, as well.
One attack in particular, which an analyst at the SANS Internet Storm Center has been taking apart in recent days, includes a malicious PHP script which the rogue AV gang is using to infect every one of the PHP scripts on all of the sites hosted on a compromised Web server. In many similar attacks in the past, the attackers have simply compromised one specific site on a server and left it at that. But this rogue AV campaign looks to be several levels beyond that.
“Once the site has been compromised, the attackers install their script
in any directory, preferably in a directory that is not accessible
directly from the web since they will not need to access it directly. The next step the attackers do is to infect all (and I mean all!) PHP
files on the compromised web site. If it’s a shared web site, and the
permissions are not setup correctly, they will actually infect
absolutely every web site hosted on that machine,” SANS ISC analyst Bojan Zdrnja wrote in his analysis of the rogue AV attack.
The attack relies on the insertion of a one-line addition to the beginning of each legitimate PHP script on the site, which ensures that the attacker’s code is executed every time one of the scripts is called. This gives the scareware gang a lot of flexibility in how and where they redirect victims once the script is executed.
“If you wonder how the attackers insert this line into every single PHP
file, the answer is simple – a special function in the master PHP script
takes care of this. It recursively traverses all directories, finds any
PHP files and if it can modify them inserts the line at the beginning.
Once the attackers installs the master PHP script (style.css.php), all
he has to do is call the script with a proper parameter,” Zdrnja wrote.
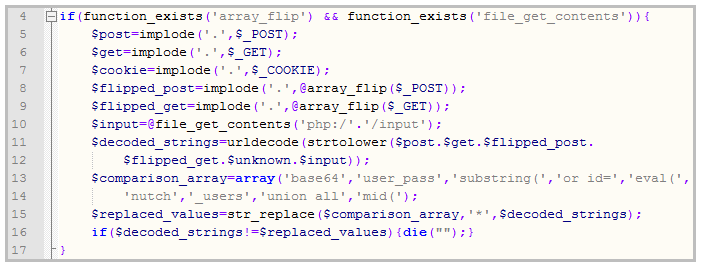
The PHP script that is at the heart of this particular attack has a slew of different functions, and Zdrnja said that one of them is designed to prevent other attackers from messing around with the script.
“This is interesting as it appears that the author of the script tried
to implement a very simple intrusion detection system – notice how it
contains SQL injection strings or parts of PHP code. This does not make a
lot of sense (especially matching of SQL injection) since the master
PHP script, for example, does not use a database at all so I wonder if
this was part of another program that the author just reused,” he said.
It’s increasingly common these days for attackers to implement measures designed to prevent rival gangs from removing their malware or otherwise disabling their attack. It’s been seen in both traditional malware campaigns, as well as in Web-based attacks for some time.









