The botnet problem has reached epidemic levels in recent months, with the continued growth of large-scale botnets, as well as the identification of smaller, more targeted networks around the world. But researchers have been taking steps to disrupt botnets of late, with some notable successes, as the recent takedown of the Mega-D botnet shows.
Mega-D, also known as Ozdok, is a botnet that has been in operation for more than a year, and is the work of the Mega-D Trojan, which has been infecting machines since February 2008. The network has at various times comprised tens of thousands of machines and was responsible for sending out a large portion of the spam on the Internet–at some points north of 30 percent. Researchers had identified the botnet early last year and had a good handle on its command-and-control structure, but it wasn’t until last week that a group of researchers at FireEye began an effort to disrupt the Mega-D botnet.
The researchers started by identifying all of the servers involved in the command-and-control infrastructure and working with the ISPs to take the servers offline. The company was able to get all but four of the C&C servers offline, and also took six of the C&C domains offline by working with the registrars involved. This is fairly standard stuff, but most botnets have backup mechanisms for the disruption of their C&C infrastructure. Mega-D was no exception.
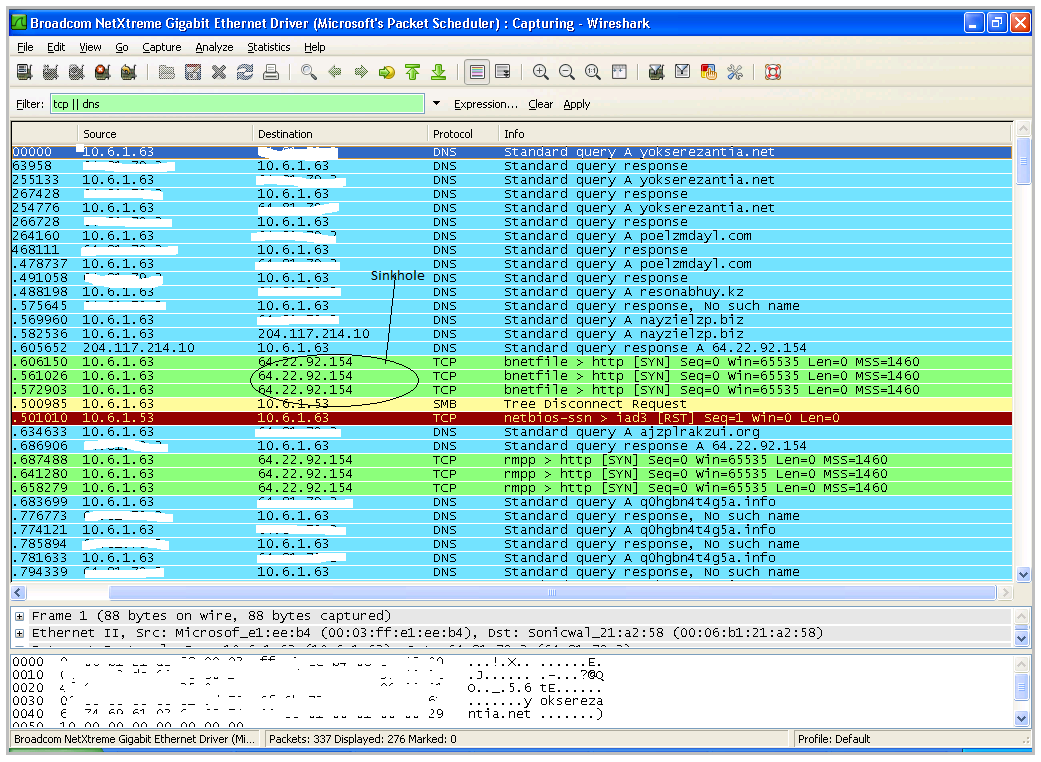
After identifying the list of unused domains that Mega-D would
register at some point if the current C&C domains went offline. So
FireEye’s researchers took the step of registering all of the unused
domains in Mega-D’s domain list and then pointing all of the domains at
a server that FireEye controls, effectively black-holing all of the
traffic.
All of these domains are
pointing to our sinkhole server now. What this means is that all the
Ozdok zombies instead of connecting to their real CnCs are coming to
this sinkhole server. Data collected from the sinkhole server logs will
be used to identify the victim machines and help them recover their
machines back to a normal state. So far we have seen 264,784 unique IPs
connecting to our sinkhole server in a 24 hour time frame. This could
be a rough estimate of the current size of Mega-d botnet.
This extra step may give researchers a head start on the botnet controllers, who likely will be looking for a new channel through which to communicate with their now-orphaned bots. The bots themsselves are of no use to the attackers without a way to control them, so it likely is only a matter of time before they find a way to circumvent the roadblocks that the FireEye researchers put in their way.









