A pro-Syrian regime hacker collective known as the Syrian Electronic Army (SEA) recently compromised the Twitter, Google Apps and other accounts belonging to The Onion, a long-running satirical news publication in the U.S. Like The New York Times before it, The Onion published a fascinating (non-comical) tell-all, indicating that it, like the Associated Press, had it fallen victim to a SEA spear phishing campaign.
Unlike the attack at The New York Times, which was the work of a state-funded, military-grade attack team, the SEA launched a fairly typical spear-phishing attack against the editorial team at The Onion. In fact, this campaign was almost identical to an attack it launched weeks earlier that resulted in a successful compromise of the Associated Press.
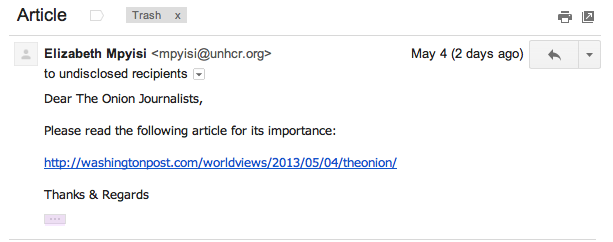
According to The Onion’s frank and honest assessment, the SEA used three distinct methods to compromise employee accounts at the Onion. First, on May 3, “from strange, outside email addresses,” the SEA sent the phishing email–screen-grabbed below–to a few of The Onion’s employees:
From here, The Onion’s IT Team said, at least one employee followed the link that appeared to lead to the Washington Post, but actually led to a compromised website that, in turn, redirected users to a fraudulent Google application credential reset page. Again, at least one employee fell for the ruse, and consequently gave the SEA access to his or her Gmail account.
Now that the SEA had access to an employee account, on May 6, it used it to send more of the same phishing email to other Onion employees. At this point, likely because the phishing emails were coming from a trusted email account, a number of employees followed the link. Only two employees actually entered their credentials into the fraudulent forms though, one of which had access to The Onions social media accounts.
The Onion then became aware of the compromise and sent out a company-wide password reset email. At the same time, the attackers sent a duplicate but fraudulent password reset email to everyone at The Onion except the IT teams, which compromised another two corporate accounts.
The Onion then published an article titled, “Syrian Electronic Army Has A Little Fun Before Inevitable Upcoming Deaths At Hands Of Rebels.” To which the SEA responded by publishing the contents of editorial emails on Twitter. The Onion’s IT team now admits that it did not know for sure which accounts were compromised and forced a password reset for every company account, ending the saga.
Ironically, this phishing post-mortem is hosted on an unrelated domain, so we reached out to The Onion for confirmation, because the People’s Daily, a Communist Party paper in China, looked silly when it ran with The Onion’s top available bachelor story about Kim Jong Un, which was, of course, a joke. The Onion’s press contact confirmed that this article is indeed a legitimate and accurate telling of what happened.