A researcher claims that hundreds of thousands of shoddily made IP cameras suffer from vulnerabilities that could make them an easy target for attackers looking to spy, brute force them, or steal their credentials.
Researcher Pierre Kim disclosed the vulnerabilities Wednesday and gave a comprehensive breakdown of the affected models in an advisory on his GitHub page.
0day vulnerabilities found in GoAhead and in Wireless IP (P2P) cameras (pre-auth RCE as root) #0day #IoT #Cloud
https://t.co/pWq7tbzLRg— Pierre (피에르) (@PierreKimSec) March 8, 2017
Kim said the vulnerabilities exist in a mass-produced Chinese IP camera called the Wireless IP Camera (P2) WIFICAM. While the cameras more or less physically look the same, vendors resell them with custom software, Kim said, which is where vulnerabilities appear to have been introduced.
The issues are largely tied to an embedded web server that’s used in each camera. While Kim cautions the web server software, GoAhead, isn’t vulnerable, the OEM vendor who implemented it in each camera is likely responsible for introducing vulnerable code.
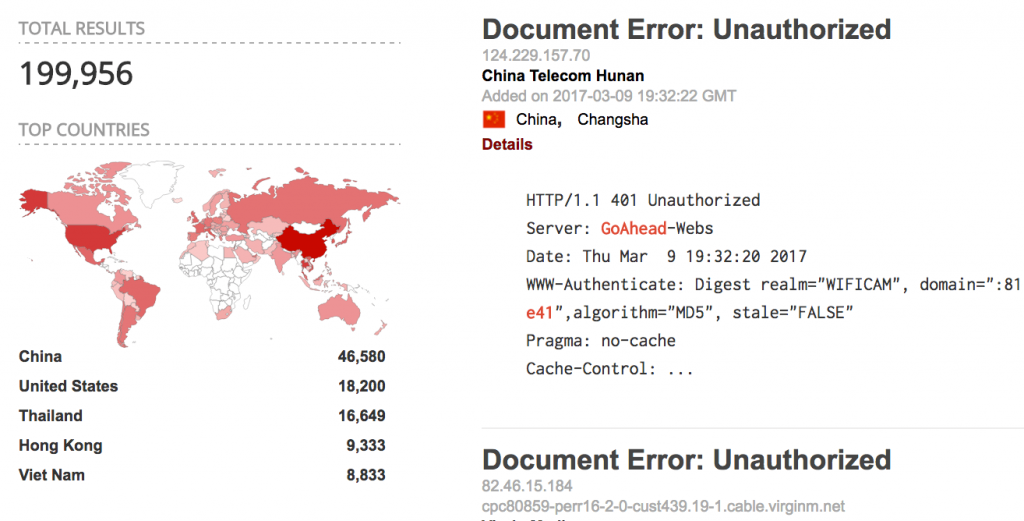
According to Kim, who conducted a search for the web server on Shodan, nearly 200,000 cameras should be considered vulnerable. While the bulk of the cameras are based in China, roughly 18,000 are based in the U.S., according to the search engine.
“I advise to IMMEDIATELY DISCONNECT cameras to the Internet,” Kim wrote, “Hundreds of thousands cameras are affected by the 0day Info-Leak. Millions of them are using the insecure Cloud network.”
The “Cloud” protocol Kim refers to is a functionality, enabled by default, on what he purports to be millions of IP cameras. The protocol is essentially a set of clear-text UDP tunnels that an attacker could use to send HTTP requests to cameras through.
An attacker could brute force requests and as soon as a camera registers a request as valid, the attacker could fetch the credentials. From there, any future HTTP requests would be sent to .CGI files hosted by the camera.
Since many of the cameras use the same protocols and the infrastructure seems to be managed by a single entity, Kim hints that it could only a matter of time until someone writes proof of concept botnet code, a la Mirai, to ensnare them all.
“This ‘cloud’ protocol seems to be more a botnet protocol than a legit remote access protocol,” Kim writes.
A faulty cloud management protocol is really just the tip of the iceberg when it comes to the cameras however.
Another, potentially worse outcome which affects 1,250 camera models, could come if an attacker chained together a series of vulnerabilities. Because of the way the custom HTTP server is set up on some cameras, an attacker could bypass authentication to steal credentials, FTP accounts, and SMTP accounts. By combining that with a remote code execution bug that exists in the camera’s FTP CGI file, an attacker could execute remote commands against the cameras. Because of the issue, a pre-auth remote code execution vulnerability, an attacker could execute commands through a local area network or via the internet.
Kim claims the exploit–which he posted proof of concept code for–could also extract valid credentials and allow an attacker to execute a payload.
Since some of the camera servers lack authentication, attackers could also stream content from some cameras via its TCP port 10554. Because telnetd is running on some cameras, a backdoor account exists as well, Kim claims.
It’s the second backdoor to be identified in a IP connected camera product line this week. On Monday an independent security researcher disclosed a backdoor he discovered in a collection of CCTV and IP cameras made by Dahua Techology. The company is urging owners to apply firmware updates it began pushing out the same day.
None of the mentioned files are part of the standard GoAhead distribution. This is a white label modified distribution.
— EmbedThat (@embedthat) March 8, 2017
Hello, I contacted you by mail. It appears the OEM vendor added some vulnerable and specific codes inside their custom GoAhead.
— Pierre (피에르) (@PierreKimSec) March 8, 2017
After getting in touch with Embedthis Software, the makers of GoAhead, Kim was able to clarify this week the vulnerabilities weren’t in the web server software and instead stemmed from the vendor-installed proprietary software. Because of the sheer number of vendors, however – almost 400 in total – Kim wasn’t able to contact them all. In lieu of a fix, the researcher is encouraging owners to discontinue use of the cameras.
Kim, who’s based in the Ivory Coast, has demonstrated a knack for unearthing vulnerabilities, mostly in routers, over the years. The researcher discovered a backdoor, backdoor accounts, and a default Wi-Fi Protected Setup PIN in a router made by D-Link last year. He previously discovered backdoors, hardcoded SSH keys, and a handful of remote code execution bugs in routers by TP-Link, Quanta, Huawei, and Totolink as well.