 Spam volume is down, there are fewer unpatched software holes and oftware application developers did a better job of writing secure code over the last year. But IBM’s X-Force Trend and Risk Report still found plenty to worry about in 2011, according to a copy of the report released this week.
Spam volume is down, there are fewer unpatched software holes and oftware application developers did a better job of writing secure code over the last year. But IBM’s X-Force Trend and Risk Report still found plenty to worry about in 2011, according to a copy of the report released this week.
Despite some improvements over 2010, the annual report found a growing crop of mobile attacks, phishing attacks and automated web server hacks.
First the good news. Spam was down 50 percent compared to 2010, only 36 percent of software flaws were left unpatched compared to 43 percent in 2010 and 30 percent fewer exploits were released overall.
But there was a 19 percent rise in mbobile exploits released publicly in 2011. IBM credits this largely to an increase in jail-breaking exploits, which in turn led to attackers launching attacks to gain elevated privileges on the phones.
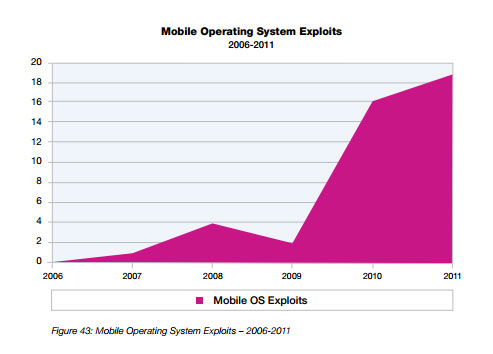
Phishing levels reached their highest level since 2008 last year, thanks to the proliferation of bogus links on social networking sites like Twitter and Facebook and a bit of advertising click fraud, IBM found.
And, while there may have been a 46 percent decrease in SQL injection vulnerabilities in Web applications, that may have been due to attackers shifting to a different tactic: shell command injections, which more than doubled in 2011. In addition to the attacks, IBM noticed an increase in brute force password attacks near the year’s end in November and December.
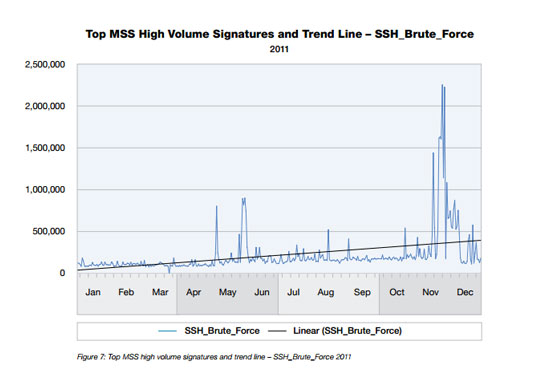
The annual report culls research from the past year gathered from the company’s 4,000+ clients and 13 billion events monitored daily.
In 2010, IBM released a mid-year version of the report calling out Google as the vendor having the highest number of unpatched, critical holes in their products. Google cried foul and IBM actually issued a retraction, claiming it had gotten its numbers wrong.
For more on the report, you can find the 136-page document here. (PDF)









