An espionage campaign featuring precise targeting of victims and malware that allows the attackers one-on-one interaction with compromised systems has been uncovered. Government agencies, manufacturers, high tech companies and media organizations in South Korea and Japan have been the primary targets of the campaign called Icefog, which was reported today by researchers at Kaspersky Lab.
The China-based campaign is two years old and follows the pattern of similar APT-style attacks where victims are compromised via a malicious attachment in a spear-phishing email, or are lured to a compromised website and infected with malware.
However, while other APT campaigns maintain a long-term persistence inside infected networks, Icefog seems to do just the opposite. The attackers, Kaspersky researchers said, know what they need from a victim and once they have it, the target is abandoned. They’re also likely a small group of hired guns, akin to mercenaries, used to attack a particular group, steal data, and get out quickly.
“We’ve entered the era of a growing number of these smaller, agile groups hired on a per-project basis,” said Kaspersky Lab researcher Kurt Baumgartner, speaking today at the Billington Cybersecurity Summit in Washington, D.C. “The operational improvements have arrived and these polished APT groups become much better at flying under the radar.
“Finding a pattern in all the noise is not easy. It’s becoming harder and harder to identify the patterns and connect them with a group,” Baumgartner said.
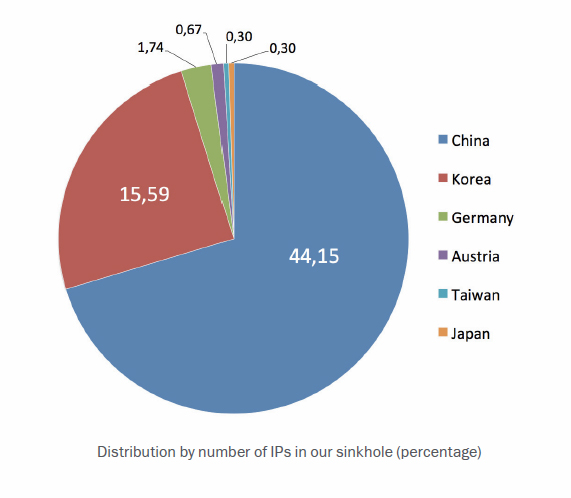
To date, Kaspersky Lab’s Global Research and Analysis Team has observed six variants of Icefog and has been able to sinkhole 13 domains used in the attack, capturing snapshots of the malware used and logs detailing victims and interaction with command and control servers.
Windows and Mac OS X versions of Icefog have also been observed, but it appears the OS X backdoor is merely a beta trial of the malware, largely found in online Chinese bulletin boards. Meanwhile, more than 200 unique Windows-based IP addresses have connected to a Kaspersky-controlled sinkhole, a fraction of the total infections researchers said.
 “There’s a team of operators that are being very selective and going after exactly what they need,” said Baumgartner, right. “It’s classic APT behavior. They likely have previous knowledge of the networks and targets.”
“There’s a team of operators that are being very selective and going after exactly what they need,” said Baumgartner, right. “It’s classic APT behavior. They likely have previous knowledge of the networks and targets.”
Those targets include defense industry contractors such as Lig Nex1 and Selectron Industrial Company, shipbuilding companies DSME Tech, Hanjin Heavy Industries, telecom operators such as Korea Telecom and media companies such as Fuji TV.
Icefog not only establishes a backdoor connection to the attacker-controlled command infrastructure, but it also drops a number of tools that allow the attackers to steal certain document types and pivot within an infected company looking for more computers to infect and additional resources to steal.
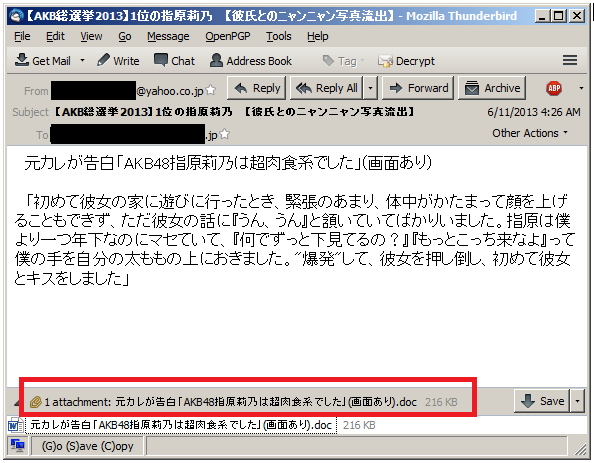
The campaign also relies on exploits for vulnerabilities that have been patched in Windows or Java to establish a foothold on an endpoint. Remote code execution bugs in Windows (CVE-2012-0158 and CVE-2012-1856) spread via malicious Word or Excel files are the most common means of initiating the Icefog attack. The infected attachments promise anything from an illicit image of a woman to a document written in Japanese titled: “Little enthusiasm for regional sovereignty reform.” Users are also sent links to compromised sites hosting Java exploits (CVE-2013-0422 and CVE-2012-1723).
Separate spear phishing campaigns were also spotted using HLP files—older versions of Winhelp files—to infect targets. Winhelp was supported natively until Windows Vista was released.
“Most likely, the choice to abuse Winhelp indicates that the attackers have an idea of what version operating systems they are attacking,” the Kaspersky report said.
Another spear phishing effort used HWP document files to spread Icefog; HWP is a proprietary document format used in South Korea, in particular by the government.
Once a machine is compromised, the attackers individually analyze system information and files stored on the machine and if it passes muster, the backdoor and lateral movement tools are remotely sent to the machine, including password and hash-dumping tools for saved Internet Explorer and Outlook passwords. A compression program is also sent down to compress stolen data before it’s sent to the command and control server. Beyond credentials, victims are losing Windows address book files (.WAB), as well as HWP, Excel and Word files.
Of the six variants, the oldest in 2011 was used in an attack against Japan’s House of Representatives and House of Councilors. Six AOL email addresses were used and commands were also fetched from these accounts.
The most commonly seen Icefog variant is called Type 1 and it has all the backdoor and lateral movement capabilities described earlier, as well as giving the attackers access to execute SQL commands on SQL Servers found on the network. It’s here where the term Icefog was seen in a string used in the command and control server (the C&C software is named Dagger Three). The command and control script, meanwhile, provides a professional looking interface used to communicate and interact with compromised machines. It uses the native file system to store stolen data and temporary files.
“Perhaps the most interesting part is that the Type 1 C&C panel maintains a full history of the attacker’s interaction with the victims,” the report said. “This is kept as an encrypted logfile, in the ‘logs’ directory on the server. In addition to that, the server maintains full interaction logs and command execution results from each victim.”
Another variant was used to enhance Type 1 infections with additional encryption obfuscating communication with command servers. It was not used against victims and disappeared once a machine was rebooted.
Samples for two other variants have yet to be obtained, but Kaspersky was able to sinkhole three domains used with these attacks. These two variants had only view and update capabilities.
The most recent version, Icefog-NG, doesn’t communicate with a central command server and instead of using a webserver, its command and control is a Windows desktop application that works as a standalone TCP server listening on port 5600.
Kaspersky said it first obtained an Icefog sample in June after an attack on Fuji TV. It was able to connect the dots back to the attack on the Japanese parliament two years ago.
“We predict the number of small, focused APT-for-hire groups to grow, specializing in hit-and-run operations, a kind of ‘cyber-mercenaries’ of the modern world,” the report said.