A phishing campaign aimed at Chinese Apple users that was thought to be in hibernation has been roused from its slumber.
Researchers in June spotted the campaign, dubbed Zycode, targeting Apple iCloud users. A rash of suspended domains that month led to a lull for the campaign however; researchers with FireEye who had been following the group said they saw little to no activity from Zycode throughout the second quarter of this year.
According to malware researchers Dr. Fahim Abbasi, Dr. Farrukh Shahzad, Abdul Salam, and Safwan Khan, the campaign stirred back to life near the tail end of summer.
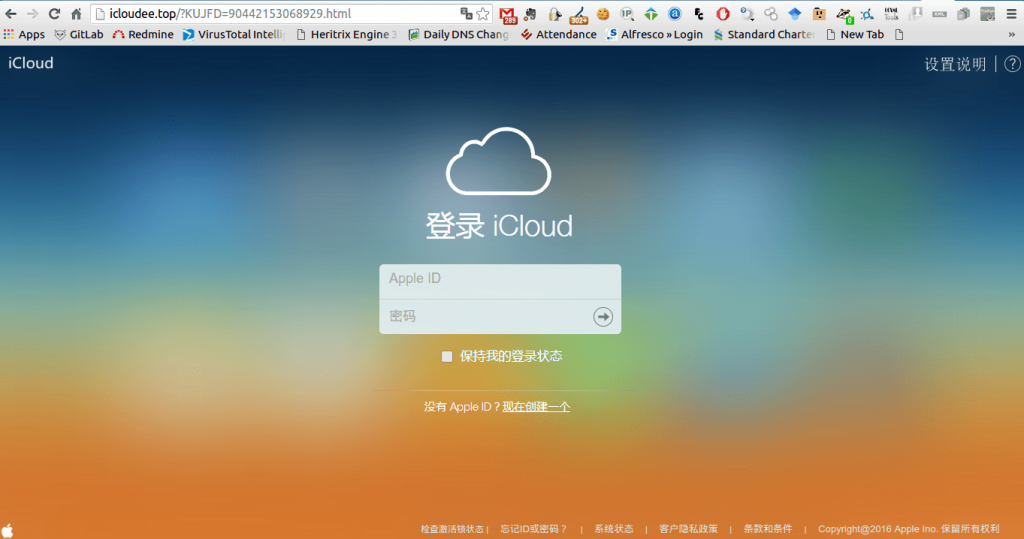
It was then when researchers discovered around 90 domains, registered from July to September, pretending to be Apple’s iCloud login site. Most of the domain names rely on typosquatting or URL hijacking to dupe victims, hoping users make a mistake when they type a website address into their browser’s URL bar. The domains have names similar to icloud.com, like iclnoud[.]com, icloud-af[.]com, and icluuod[.]com and other deceptive Apple names like apple-iphone[.]com, apple-safety-center[.]com, and find-apple-ios[.]com.
The content of the sites is designed to mimic Apple’s iCloud website too; the same obfuscated JavaScript that was used in June’s campaign is used in the new one, FireEye said. The JavaScript is used to create convincing phishing HTML content that resembles the legitimate China’s iCloud.com site.
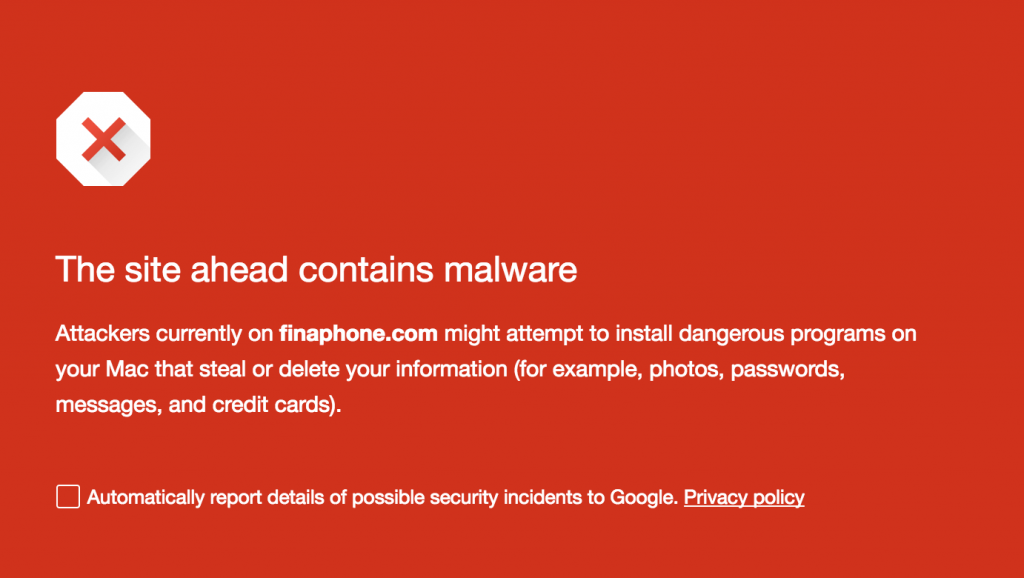
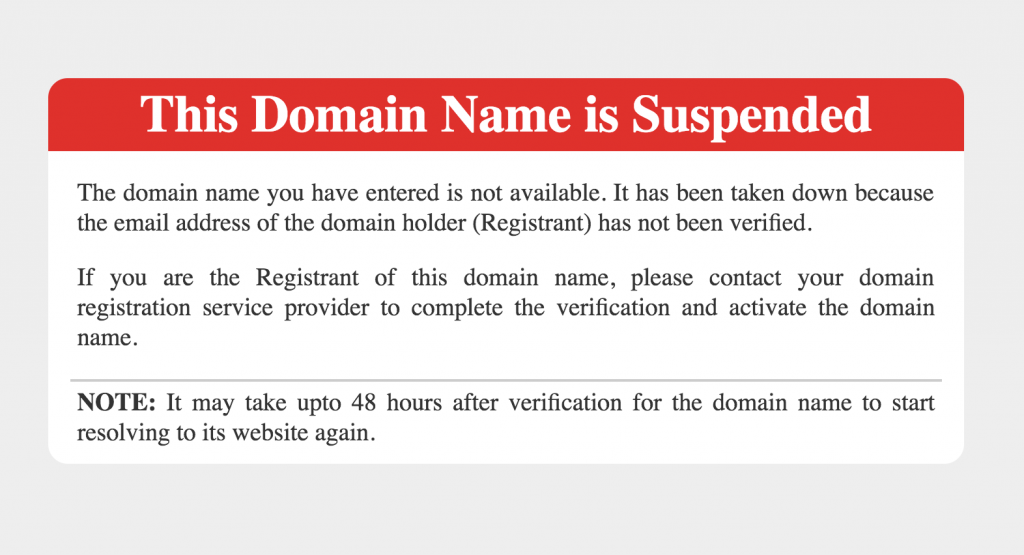
A cursory glance at some of the sites shows that most of the domains have already been suspended. Some ultimately lead to DNS errors but are preceded by red Google Safe Browsing warnings that warn the sites contain malware.
The email addresses associated with the domains – most of which are tied to a Chinese instant messaging program QQ.com, and the IP addresses, which trace back to mainland China have changed, too.
It’s not the first time Apple users in the country have been targeted by phishing scams.
GreatFire, a non-profit group that keeps track of websites censored by China and helps users there circumvent censorship, observed a man-in-the-middle attack carried out by Chinese authorities on Apple’s iCloud page in 2014. Officials with the organization said at the time the fake iCloud site was using a self-signed certificate, instead of one issued and verified by a trusted Certificate Authority. The attack coincided with the release of the iPhone 6 that month.
As FireEye points out, users, especially those based in China, should be vigilant when it comes to logging into their iCloud account. If they haven’t already, users should enable two factor authentication for their Apple ID and ensure the address bar is correct every time they login to iCloud.com.
The campaign described by FireEye is similar to one carried out earlier this year that targeted Bitcoin and blockchain wallet credentials. Researchers with OpenDNS uncovered the campaign and noticed more than 100 fake domains that had been set up to dupe visitors to blockchain.info. If a victim was tricked into logging into a spoofed version of the site, they could have unwittingly handed over their Bitcoin wallet credentials. Unlike the iCloud typosquatting scam, which relies on users navigating to the sites on their own, attackers were spreading the fake blockchain.info links through a pay-per-click advertising scam via Google Adwords.