 We know a lot about the effects of malicious programs like rootkits and Trojan downloaders. The job of finding out exactly how the programs work, however, is painstaking. That’s because most malware authors worth their salt take steps to make their creations hard to understand. Code obfuscation and anti-debugging are common features of most sophisticated, modern malware. With patience and endurance, however, researchers are often able to pierce the veil, anyway.
We know a lot about the effects of malicious programs like rootkits and Trojan downloaders. The job of finding out exactly how the programs work, however, is painstaking. That’s because most malware authors worth their salt take steps to make their creations hard to understand. Code obfuscation and anti-debugging are common features of most sophisticated, modern malware. With patience and endurance, however, researchers are often able to pierce the veil, anyway.
That was the case this week, when researcher Giuseppe Bonfa published a detailed analysis of a ubiquitous and very complex piece of malware known as ZeroAccess. Bonfa made his research public in a four-part series that analyzes various aspects of ZeroAccess, including the rootkit’s criminal origins and the various tools it uses to maintain a hold on computers it infects – even after the operating system on those machines has been completely removed and reinstalled.
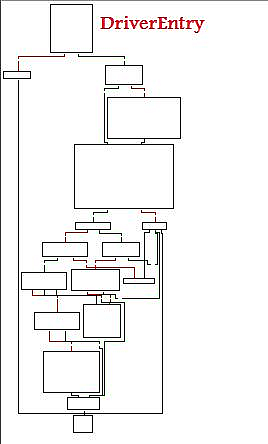
Our image of the day is taken from Mr. Bonfa’s report and shows a graphic created in the process of disassembling the rootkit. This picture is a graphical representation of the execution path for a key ZeroAccess driver, which is dropped on infected systems and used to support the stealth features and functionality of the malware, which is used to install fake antivirus software and other crimeware. The rookit “has low level disk access that allows it to create new volumes that are totally hidden from the victim’s operating system and anti virus,” Bonfa writes.









