 Reports surfaced last week about an incident dating back to April, 2010 that involved the suspicious rerouting of Internet traffic through infrastructure belonging to a telecommunications carrier in China. Originally reported within technical circles in April, the incident simmered within the small community of network operators who debated the cause of what appeared to be a large scale hijacking of Internet traffic to infrastructure operated by China Telecommunications. But was it?The incident appeared to be yet another chapter in an ongoing saga about the problems flowing from an aging Internet infrastructure. In this case, the culprit appeared to be BGP, the Border Gateway Protocol – a core component that helps Internet connected routers figure out which networks are reachable and, thus, reliable routes for traffic to move from one Internet destination to another, based on routing policies. Likened to “routing by rumor,” BGP has long been recognized as an Achilles heel – prone to accidental or purposeful hijacking that can send a flood of Internet traffic of all types through the bottleneck of a single network operator or nation state.
Reports surfaced last week about an incident dating back to April, 2010 that involved the suspicious rerouting of Internet traffic through infrastructure belonging to a telecommunications carrier in China. Originally reported within technical circles in April, the incident simmered within the small community of network operators who debated the cause of what appeared to be a large scale hijacking of Internet traffic to infrastructure operated by China Telecommunications. But was it?The incident appeared to be yet another chapter in an ongoing saga about the problems flowing from an aging Internet infrastructure. In this case, the culprit appeared to be BGP, the Border Gateway Protocol – a core component that helps Internet connected routers figure out which networks are reachable and, thus, reliable routes for traffic to move from one Internet destination to another, based on routing policies. Likened to “routing by rumor,” BGP has long been recognized as an Achilles heel – prone to accidental or purposeful hijacking that can send a flood of Internet traffic of all types through the bottleneck of a single network operator or nation state.
That is, until a reference to the April incident turned up in the 2010 Report to Congress by the US-China Economic and Security Review Commission. While not pinning the incident on the Chinese Government, the report implied that, for a period of 18 minutes on April 8, sensitive government and military traffic may have been sent through Chinese systems on the way to its destination and that “incidents of this nature could have a number of serious implications... enabl(ing) surveillance of specific users or sites.”
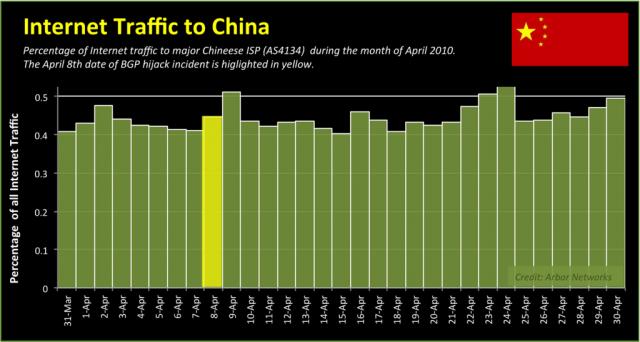
That report set off a flurry of coverage in the mainstream media, which seemed willing to take it faith that the incident had connections to the Chinese government or military. But did it? Craig Labovitz of Arbor Networks isn’t so sure. In a blog post Monday, Labovitz notes that the hijack – if it was a hijack – had little if any noticeable impact on the Internet routing infrastructure.
In a graphic published on Arbor’s blog, which is our image of the day, Labovitz is able to show that the now storied hijack is almost indistinguishable from other traffic spikes through the same Chinese infrastructure that month – and not even the highest spike at that.
“While traffic may have exhibited a modest increase to the Chinese Internet provider (AS23724), I’d estimate diverted traffic never topped a handful of Gbps,” he wrote” :And in an Internet quickly approaching 80-100 Tbps, 1-3 Gbps of traffic is far from 15% (it is much closer to 0.015%).”
Stay tuned for more!









