Attackers mounting password-spraying campaigns are turning to the legacy Internet Message Access Protocol (IMAP) to avoid multi-factor authentication obstacles – thus more easily compromising cloud-based accounts.
That’s according to researchers with Proofpoint, who found that in the past half year, a staggering 60 percent of Microsoft Office 365 and G Suite tenants have been targeted with IMAP-based password-spraying attacks; and 25 percent of those targeted experienced a full-on breach as a result.
Password-spraying attacks are when an attacker attempts to access a large number of accounts or usernames with a few commonly used passwords – seen most recently in the Citrix security incident from last week. In a Thursday report that analyzed over 100,000 unauthorized logins across millions of monitored cloud user-accounts, it’s clear that more attackers using this method are leveraging IMAP – the legacy protocol used for accessing and storing mail on mail servers – and when combined with recent massive credential dumps, it allows the compromise of accounts “at an unprecedented scale.”
Legacy protocols (such as POP and IMAP) make it more difficult for service administrators to implement authentication protections like multi-factor authentication, according to Proofpoint. In turn, the lack of multi-factor authentication means that threat actors launching attacks through IMAP can avoid account lock-out and compromise accounts unnoticed.
“Attacks against Office 365 and G Suite cloud accounts using IMAP are difficult to protect against with multi-factor authentication, where service accounts and shared mailboxes are notably vulnerable,” researchers said.
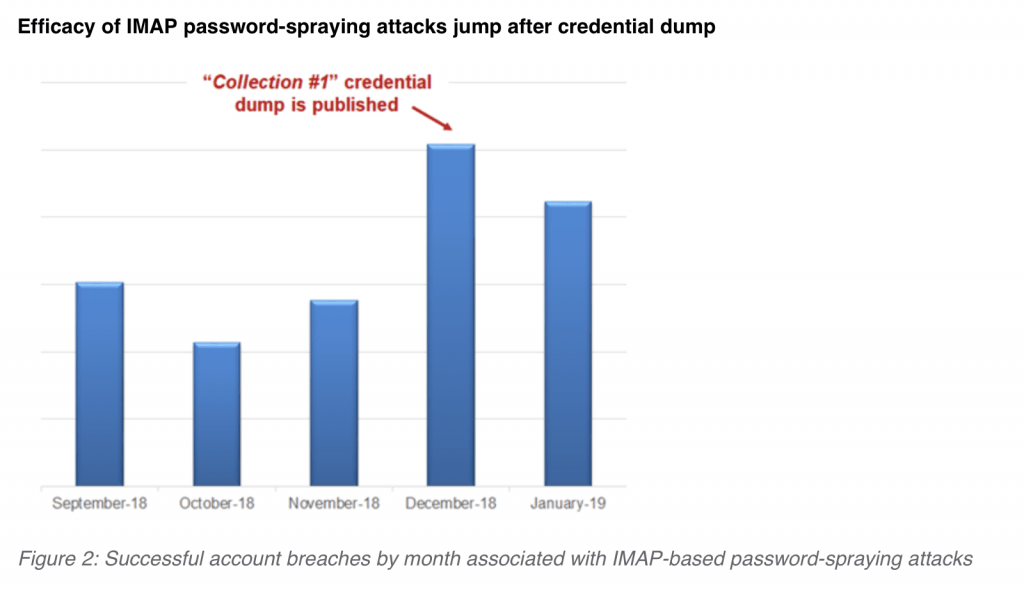
IMAP-based password-spraying campaigns appeared in high volumes between September 2018 and February 2019, according to the report, especially those targeting high-value users such as executives and their administrative assistants.
“Targeted, intelligent brute-force attacks brought a new approach to traditional password-spraying, employing common variations of the usernames and passwords exposed in large credential dumps to compromise accounts,” researchers said in a posting.
Meanwhile, the widespread number of credential dumps appearing on the cybercrime underground is another factor that helps threat actors carry out brute-force and password-spraying attacks.
In fact, in December 2018 when the “Collection #1” credential dump – and the subsequent Collection #2-5 – exposed billions of account records, researchers found a sharp increase in successful account breaches for that month over the months previous.
Overall, the report found that 72 percent of major cloud service tenants – like Office 365 and G Suite cloud accounts – were targeted at least once by threat actors. Forty percent of tenants had at least one compromised account in their environment.
Once they compromise an account, the attacker’s primary goal is typically to launch internal phishing attempts – especially if the initial target does not have the access needed to move money or data.
They can do so by sending internal phishing emails from “trusted” compromised accounts to target corporations’ payroll systems.
“Post-login access to a user’s cloud email and contact information improve an attacker’s ability to expand footholds within an organization via internal phishing and internal BEC [business email compromise], which are much harder to detect than external phishing attempts,” researchers said. “Attackers also leverage these trusted user accounts or brands to launch external attacks or make use of the infrastructure as part of broader attack campaigns.”