A “critical water utility” has been targeted in a recent ransomware attack, significantly impeding its ability to provide service in the week after Hurricane Florence hit the East Coast of the U.S.
The Onslow Water and Sewer Authority (ONWASA) said in a Monday release that a “sophisticated ransomware attack… has left the utility with limited computer capabilities.” While customer data was not compromised as part of the attack, the lack of computing ability will impact the timeliness of service from ONWASA “for several weeks to come.”
“We are in the middle of another disaster following Hurricane Florence and tropical storm Michael,” CEO Jeff Hudson said in a video posted on Facebook, speaking to employees on the matter. “With a very sophisticated attack they penetrated our defenses, just as they penetrated the city of Atlanta and Mecklenburg county.”
ONWASA has received one email from the cybercriminals, who it said may be based in a foreign country: “The email is consistent with ransomware attacks of other governments and corporations. Ransom monies would be used to fund criminal and perhaps terrorist activities in other countries.”
The amount of ransom demanded was not specified by ONWASA. A team of local, state and federal agencies are cooperating to restore the utility, the company said.
The Attack
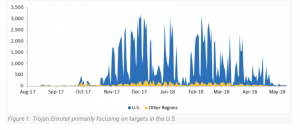
On Oct. 4, ONWASA first saw indications of the virus known as Emotet, a well-known polymorphic malware that has been popping up in the news for years, on its network.
Emotet stands out in its ability to self-propagate, meaning that once it’s on a computer, the malware downloads and executes a spreader module. That module has a password list that it uses to brute-force access to other machines on the same network. Emotet can also spread to additional computers using a spam module that it installs on infected victim machines.
Network-spreading particularly poses as a headache for organizations, because it means that victims can become infected without even needing to click on a malicious link or attachment.
While the utility said it has “multiple layers of computer protection in place” – including firewalls and AV software – they were unable to stop the penetration. And, while the virus was at first thought to be under control, it persisted.
Then, at what may have been a timed event, the malware launched a sophisticated virus known as RYUK at 3 a.m. on Oct. 13.
Emotet has been around for years – most recently, in early July, officials in Portsmouth, N.H. said that the malware cost them $156,000 to remove after spreading to the city’s entire computer network via phishing emails.
Tricky Emotet first emerged targeting banking credentials; but lately, researchers have spotted the trojan changing its tactics and its targets, catching the eye of both researchers and law enforcement this week.
“Despite its age, Emotet is far from just barely alive,” researchers with Check Point Research said in a report. “It spreads itself abundantly through spam emails, network shares and the Rig exploit kit. While some features have stayed constant, during the four years of Emotet’s lifecycle, modules have come and gone.”
A technical alert from the Department of Homeland Security in July said that Emotet infections on average cost state and local governments up to $1 million per incident to remediate.
While there was no indication of who the threat actors might be behind this particular incident, earlier this year, Symantec researchers linked Emotet to threat group Mealybug, a cybercrime actor that has been active since at least 2014.
Mealybug seems to have both expanded the trojan’s capabilities and its targets to become what Symantec researchers call an “end-to-end service for delivery of threats.”
“Mealybug’s shift from distributing its own banking trojan to a relatively small number of targets, to acting primarily as a global distributor of other groups’ threats, is interesting, and backs up an observation we made… that threat actors are evolving and refining their techniques and business model to maximize profits,” Symantec researchers said in a blog post.
The Fallout: Issues With Hurricane Relief
ONWASA said it would not pay the ransom, instead rebuilding its databases and computer systems from the ground up: “ONWASA will not negotiate with criminals nor bow to their demands. The FBI agrees that ransoms should not be paid.”
The company provides water and sewer service to all of Onslow county (except Jacksonville residents). That county is one of many in the southeast region of the U.S. to be grappling with fallout from Hurricane Florence, a storm that made landfall near Wrightsville Beach, N.C. in September. Despite ranked Category 1 when it landed, the slow-moving nature of the storm translated into epic flooding.
When the storm first hit, entire streets and cars were washed away by floodwaters, while county buildings sustained major damage from water. Weeks after, North Carolina is still struggling to rebuild. Onslow county’s schools are still closed this week due to major damage from the storm.
In the midst of these issues, after the ransomware attack the utility must operate manually while it rebuilds its system.
That means that service orders, account-creation, connections, disconnections, development review, backflow programs, engineering and human resources will all be operating manually until the computer systems are restored, ONWASA said.
Meanwhile, while the phone service remains active, email service has been interrupted for most of the utility.
“Whether they were targeted by a sophisticated adversary or just caught in a blast of malware looking to exploit people recovering from a devastating weather event, sadly, this is not that surprising,” Katherine Gronberg, vice president of Government Affairs at ForeScout, told Threatpost. “Smaller utilities have limited resources and cybersecurity capabilities, and the federal government has already acknowledged the need to do more to assist them. This incident calls to mind other efforts currently afoot in Congress and will likely entail some difficult decisions at all levels, from policymakers to power producers to consumers.”
Despite the painstaking effort behind rebuilding its computer systems, CEO Hudson said in the Facebook video that there is no expectation that paying the ransom would forestall repeated future attacks.
“Do your worst; we’ll come back from this… that’s what we’re going to tell the cybercriminals and the world,” he said.