It’s on: Adversaries, CISOs and researchers are all simultaneously involved in a frantic race to find cybersecurity vulnerabilities hiding within industrial networks, according to the latest Biannual ICS Risk and Vulnerability report from Claroty.
The report analyzed all publicly disclosed vulnerabilities in ICS networks in the second half of 2020 and found a nearly 33 percent increase in ICS disclosures over 2018, both from organizations like Claroty and from independent researchers.
Industries with the most disclosures include vital infrastructure components like critical manufacturing, energy, water, wastewater and commercial facilities.
Worse yet, more than 71 percent of the bugs were remotely exploitable, and every disclosure in the second half of 2020 ranked highly on MITRE’s 2020 CWE Top 25 Most Dangerous Software Weaknesses list because they were easy to exploit and potentially catastrophic, the report said.
ICS Cybersecurity Attracts Researchers
During the second half of 2020, Claroty counted 449 vulnerabilities reported across 59 ICS vendors; and there were 893 for the whole year. To put that in perspective, in 2018, the total number of disclosed ICS bugs for the entire year was 672, and in 2019 the year’s count was 716, Claroty reported.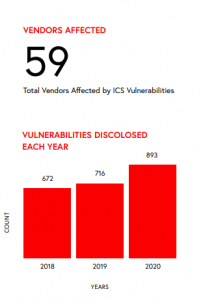
Increasingly, those reports are from independent researchers, the report said. In fact, Claroty found that 50 new researchers published disclosures in the second half of 2020, who hadn’t published in the two previous years.
“There has been a shift towards ICS research with strong growth in security research groups for this second biannual report, as more organizations try and understand the new attack landscape,” Amir Preminger, vice president of research at Claroty, explained to Threatpost. “With this increase in the amount of players coming into the market and focusing on ICS security, there will naturally be an increase in vulnerabilities [that are found].”
Adversaries Turn Attention Toward Industrial Bugs
Adversaries are also ratcheting up their pressure on industrial networks. For instance, Claroty observed the addition of industrial processes into the Snake ransomware kill list.
“The ICS environment has become a more attractive target for cybercriminals and this incentive is not just about what will cause the most damage, but also what equipment they can get their hands on,” Preminger said. “Attacks will grow increasingly sophisticated and targeted, so it is important that organizations use different walls of detection and practice security in depth.”
Legacy systems with long shelf lives are also weak spots.
“While ICS and SCADA vulnerability research is maturing, there are still many decades-old security issues yet uncovered,” the report explained. “For the time being, attackers may have an edge in exploiting them, because defenders are often hamstrung by uptime requirements and an increasing need for detection capabilities against exploitable flaws that could lead to process interruption or manipulation.”
ICS CISOs & SolarWinds PTSD
The report added that headlines about the SolarWinds attack have made CISOs in every industry think twice about the sheer scope of their networks and who might want to attack them.
“Nation-state actors are clearly looking at many aspects of the network perimeter to exploit, and cybercriminals are also focusing specifically on ICS processes, which emphasizes the need for security technologies such as network-based detection and secure remote access in industrial environments,” Preminger added.
The good news is that the industry is starting to react.
“It is heartening to see a growing interest in ICS within the security research community, as we must shine a brighter light on these vulnerabilities in order to keep threats at arm’s length,” Preminger said. “More vulnerabilities identified means the industry is more secure, so it is reassuring to see the security community take this seriously.
Download our exclusive FREE Threatpost Insider eBook Healthcare Security Woes Balloon in a Covid-Era World, sponsored by ZeroNorth, to learn more about what these security risks mean for hospitals at the day-to-day level and how healthcare security teams can implement best practices to protect providers and patients. Get the whole story and DOWNLOAD the eBook now – on us!











