Organizations struggle with securing consumer mobile devices in the enterprise because A) they don’t own the device; and B) mobile traffic often isn’t accessible to network managers making it difficult to scan for infections or anomalous behavior.
At DEF CON last weekend, a team of researchers demonstrated an inexpensive cellular intrusion detection system (CIDS) built with a commercial femtocell, commodity hardware, and the open source Snort IDS. The researchers say the system, the first publicly available for cellular traffic inspection, can scale for enterprise deployments with better hardware and is a game-changer for securing personal devices at work.
“The CIDS changes the game for BYOD. It gives enterprise security professionals the capability to detect infected smartphones which are physically in their environments cheaply and efficiently,” said Sherri Davidoff of LMG Security, one of the researchers on the project. The presence of such a system could allow an organization to forego mobile device management software or the need for antimalware protection on every device. “You can detect infected smartphones that record audio or visual data, and block or shut down bots remotely, without needing to install antivirus software or MDM software on any device. That’s a huge step forward for smartphone security, especially in BYOD environments.”
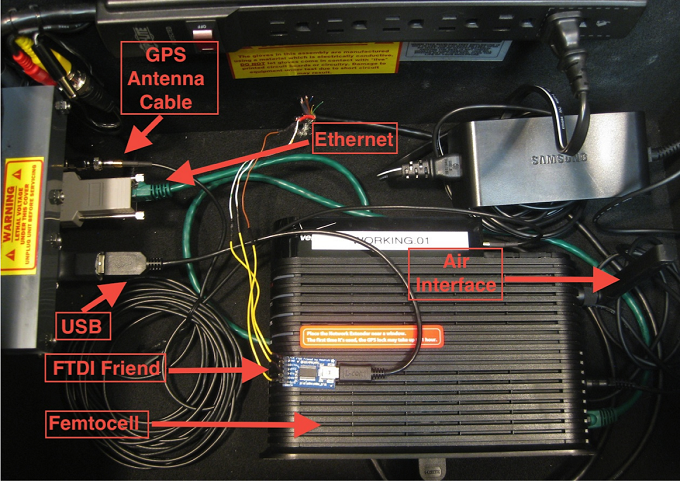
The LMG researchers used a commercial Verizon Samsung femtocell, a low-power cellular base station that connects to a mobile network provider via a subscriber’s Internet connection, and a server running Snort—all built for less than $300. The team infected an Android device with the Android.Stels malware and wrote Snort rules to detect it. The CIDS system gave the team sufficient visibility into network traffic to detect the malicious activity—including communication with a command and control server—by running traffic through the femtocell, which was modified to redirect traffic from the device to a separate system running Snort.
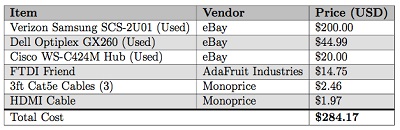 “For the proof-of-concept, we were monitoring traffic from only 1-2 cell phones at a time. This can easily be scaled up with a COTS server and some code polishing. Our CIDS server, an older Dell Optiplex G260, cost $44 on eBay (including shipping) and handled that small amount of traffic without any problems,” Davidoff said. “The solution scales well. You’d want to purchase ‘real’ server hardware to run Snort and handle the IDS portion (rather than the old desktop we used in the lab), with a modern processor and decent amount of memory. The precise specifications would depend on your volume of traffic.”
“For the proof-of-concept, we were monitoring traffic from only 1-2 cell phones at a time. This can easily be scaled up with a COTS server and some code polishing. Our CIDS server, an older Dell Optiplex G260, cost $44 on eBay (including shipping) and handled that small amount of traffic without any problems,” Davidoff said. “The solution scales well. You’d want to purchase ‘real’ server hardware to run Snort and handle the IDS portion (rather than the old desktop we used in the lab), with a modern processor and decent amount of memory. The precise specifications would depend on your volume of traffic.”
For this experiment, traffic was copied using NFQUEUE and routed to netcat, Davidoff said, which sent it across the network to a listener on the CIDS.
“For production use, we’d like to work with a femtocell manufacturer to export traffic directly to the CIDS via a network socket using encryption,” she said.
Davidoff added that there were challenges the team had to overcome with the complicated CDMA2000 protocol, in particular dissectors that would help them monitor SMS and voice traffic as well. And then there’s encryption.
“The biggest challenge was that the cellular traffic is sent from the femtocell to Verizon’s network using an encrypted IPSec tunnel,” Davidoff said. “Rather than trying to break the encryption, our team felt it would be simpler and more elegant to modify the open-source Linux software on the device and use it to bypass the tunnel entirely. We capture the unencrypted traffic before it is sent to the tunnel, or after it is received.”
One other pleasant offshoot, the researchers said, was that they were able to identify a weakness in the protocol used by the Android.Stels malware to communicate with its command and control server. Eventually, the team was able to remotely take over the bot.
“By making local cellular network traffic visible to everyday security professionals and researchers, we can reverse a critical asymmetry between attack and defense capabilities” researchers wrote in a paper on the project, “and give defenders tools for detecting and preventing mobile malware cheaply and effectively.”